Online DNS reconnaissance with Robtex
DNS reconnaissance is a piece of the data-gathering stage on a penetration test engagement. When a penetration tester is playing out, DNS surveillance is endeavoring to acquire as much data as he can in regards to the DNS servers and their records. The information that can be accumulated may unveil the network foundation of the organization without alarming the IDS/IPS. It is foreseeable that the majority of the organizations are not checking their DNS server traffic and those that do monitor the zone transfer endeavors.
One of the online DNS reconnaissances is “Robtex,” which uses various sources to gather public information about IP addresses, domain names, autonomous systems, hostnames, routes, etc. It then indexes the information in a big database and provides free access to the data.
To use this tool, visit the “https://www.robtex.com/“ webpage and type any target domain name to perform a DNS reconnaissance.

From the subsequent page, you can navigate further between the different tabs.
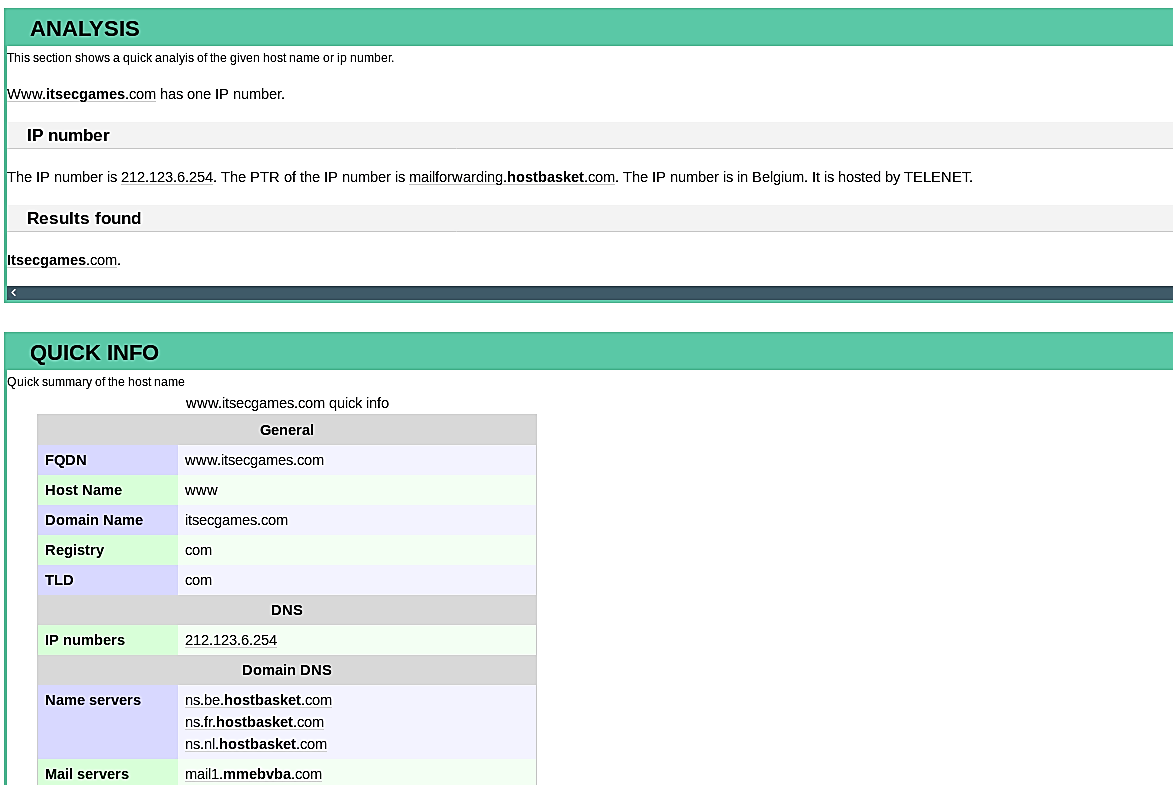
This tool searches for an IP number and gets which hostnames point to it. The reverse DNS records work not only for IP addresses but also for MX (mail server) records and NS (name server) records. It also makes a Whois lookup for a registered domain in different Whois databases to find contact information with the registration and expiration date.

Robtex can provide information on reverse DNS lookups. It will look for an IP address and determine which hostnames are associated with it. Not only do reverse DNS records function for IP addresses, but they also work for MX (mail server) and NS (name server) records.
