Subdomain enumeration with - Knock
“Knock” is a python tool created to enumerate subdomains on a target system through a wordlist. It scans for DNS zone transfer and tries to bypass the wildcard DNS record automatically if it is enabled. Now Knock supports queries to VirusTotal subdomains. You can set the API_KEY within the “config.json” file.
To download the tool, visit the following GitHub page: “https://github.com/guelfoweb/knock.”

Copy the downloadable link and clone it into the “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/guelfoweb/knock.git).
From the “knock” directory, run the setup file.
Ex: (root@kali:/opt/knock# python3 setup.py install).
Now, change the directory to “knockpy” and run the tool with the “-h” argument at the end to see what kind of usage options we have.
Ex: (root@kali:/opt/knock/knockpy# python3 knockpy.py –h).

To perform a necessary subdomain enumeration, use the following command: (root@kali:/opt/knock/knockpy# python3 knockpy.py exampledomain.com). It will list all possible subdomains for the website exampledomain.com and their running server names.
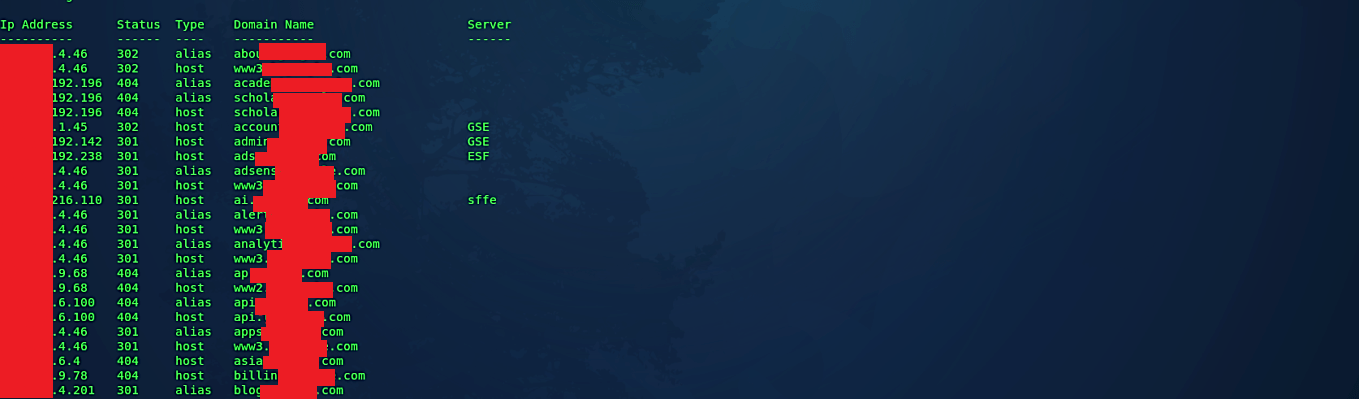
Always look for DNS subdomains that refer to services that aren’t in use in your configuration.
