“Defend the Web” write-up (Secure agent)
“Defend the Web” write-up (Secure agent — browser spoofing)
A user agent is a “string” — a line of text — that the webserver uses to identify the browser and operating system. This may appear straightforward, yet user agents have evolved into a jumbled mess over time.
In this challenge, the browser allows access to the page only as a “secure_user_agent”. Let’s see how we can accomplish it. For this particular example, it would be better to use Google Chrome.

A User-Agent field is included in the HTTP header when your browser connects to a website. The user agent field’s contents differ from browser to browser. Each browser has its own user agent, which is unique to it. A user agent is essentially a mechanism for a browser to say to a web server, “Hey, I’m Mozilla Firefox on Windows” or “Hello, I’m Safari on an iPhone.” You need to find a way to spoof the brother as “secure_user_agent.”
Right-click on the page and select the “Inspect” option to analyze further.
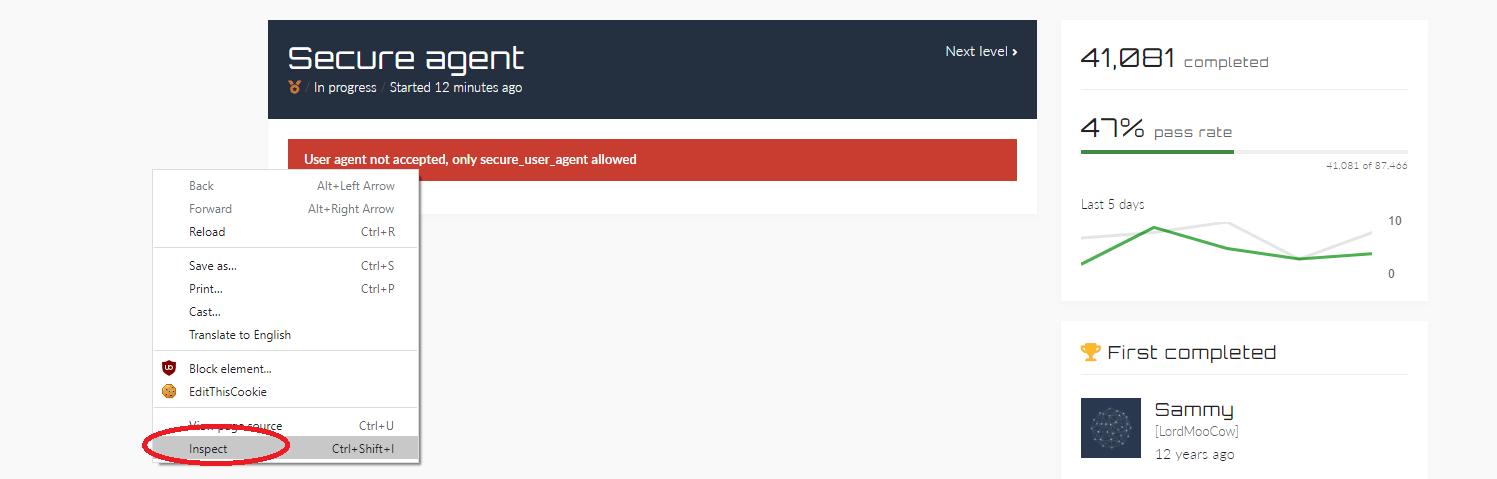
Click on the three dots on the top right corner and from the drop-down menu click on the “More tools” option, then select the “Network conditions” option.
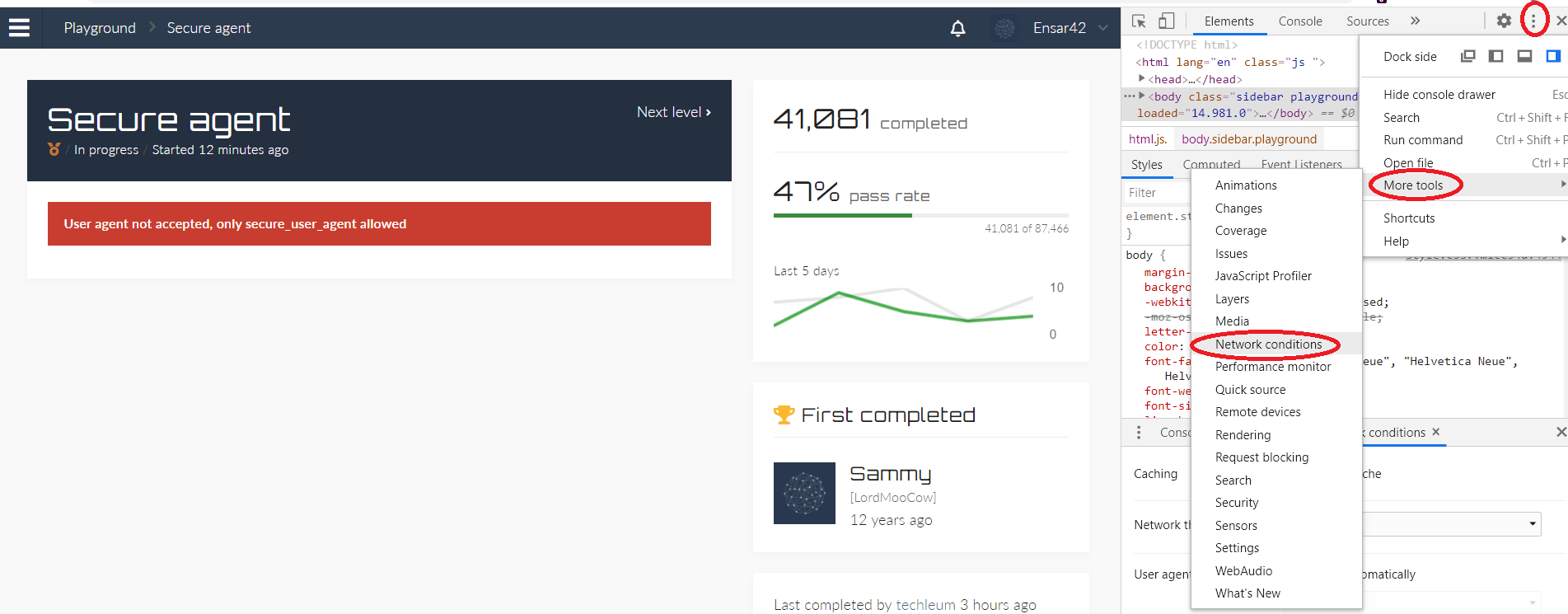
From the “Network condition” window uncheck the box for the “Select automatically” option, and then add a custom User-Agent.
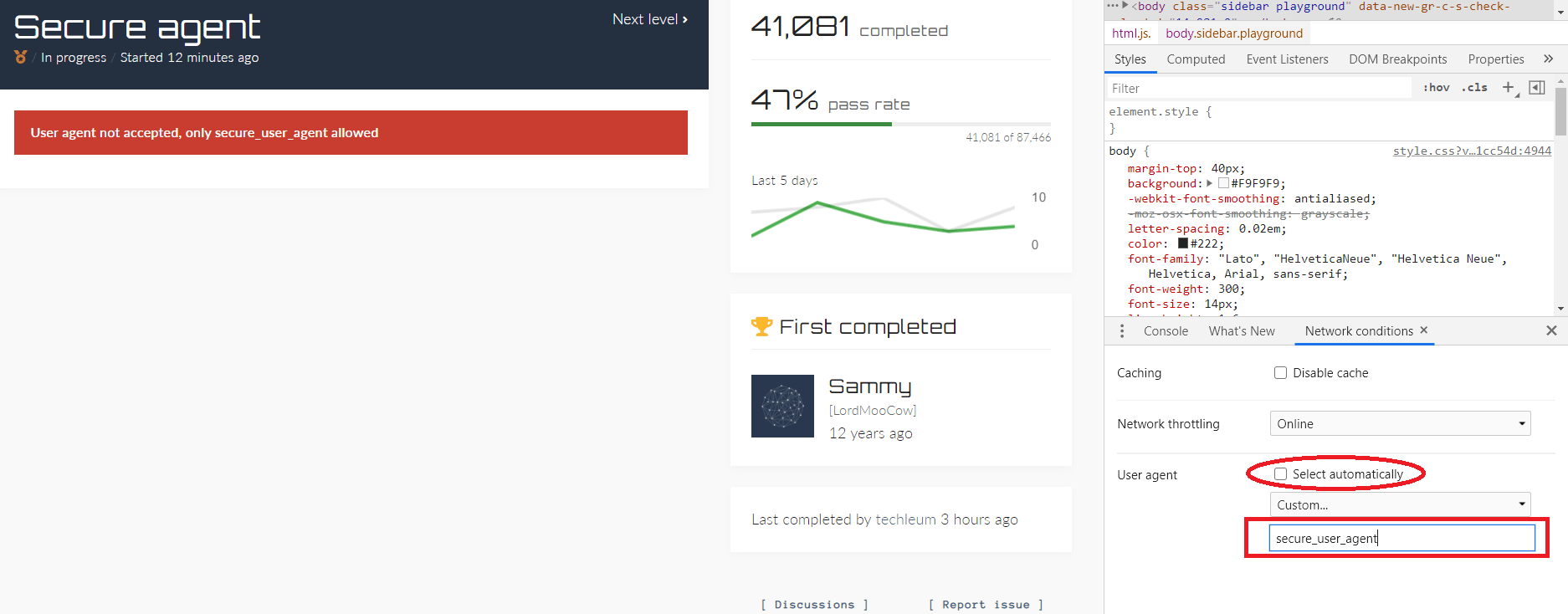
Refresh the website and the browser will be spoofed to “secure_user_agent.”

Custom user agents are available in all major browsers, allowing you to monitor what web servers communicate to different browsers. Set your desktop browser’s user agent string to that of a mobile browser, for example, and you’ll see mobile versions of online pages on your desktop.
The number of User-Agent exploitation attempts we’re seeing isn’t particularly high, but it’s consistent. It demonstrates that the illegal business model still works and that there are still susceptible systems out there being scanned for, attacked, taken over, and then used to spread the attack even further.
This is an intriguing attack vector, and we’d like to raise awareness about it. Of course, the most critical thing you can do is ensure that all security updates are installed on a regular basis. This is a single-point-of-failure that permits attacks like these to continue.
If you’re a security professional, you should be working in the hunting mode rather than the fishing mode. Don’t only wait for your security outfits to alert you when something is discovered. Look for it on your own. Manually or with a simple script, the User-Agent string is fairly straightforward to log and analyze. It won’t provide you with a real-time alarm, but if an assault manages to get past your defenses, you’ll be able to track it down and counteract it.
