Cybercriminals use Microsoft Teams chat rooms to spread malware
- February 18, 2022

Some hackers are exploiting Microsoft Teams accounts, according to security researchers, in order to enter into chats and transmit malicious executables to other users. Every month, more than 270 million people depend on Microsoft Teams, with many of them naively trusting the platform regardless of the lack of anti-malware measures.
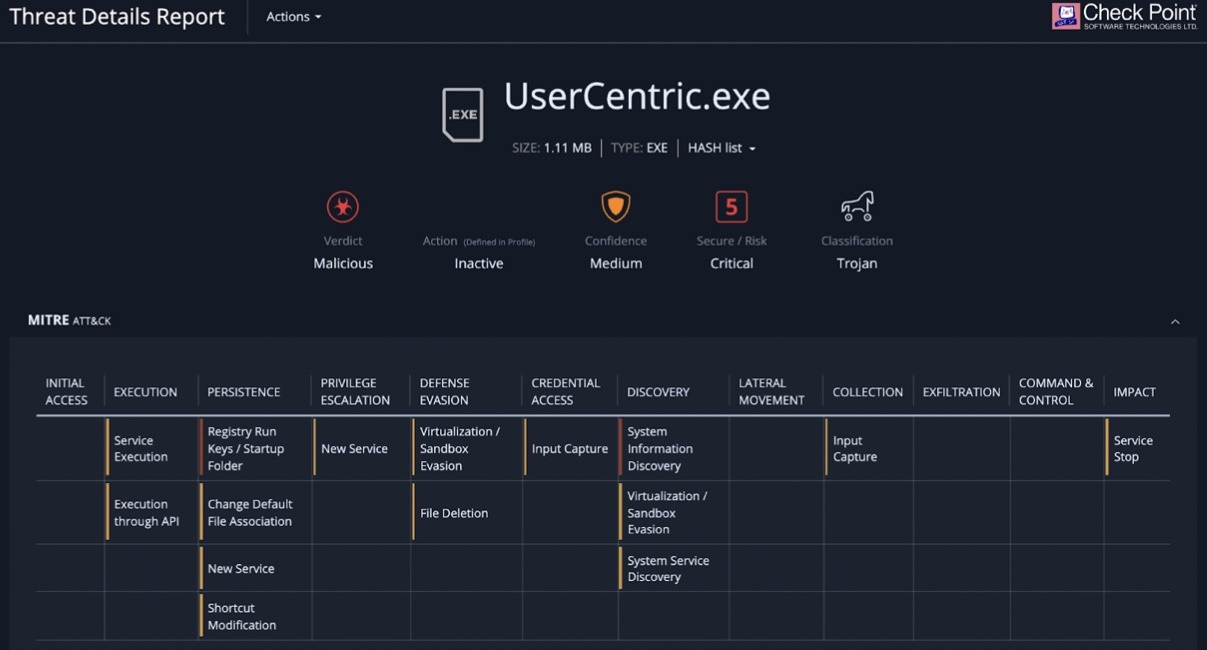
Hackers began dropping dangerous executable files in chats on the Microsoft Teams communication network, according to researchers at Avanan, a Check Point business that secures cloud email and collaboration services. The attacks began in January, according to the firm, and the malicious user adds an executable file called “UserCentric” into a chat to deceive the victim into executing it.
The malware uploads data to the system registry, installs, DLLs, and maintains persistence on the Windows PC once it has been launched.
“Hackers uploaded a malicious Trojan document to a chat thread in this Teams assault. When the file is activated, it will eventually take control of the user’s machine.” — Avanan
The technique utilized to obtain access to Teams accounts is unknown, however, it could involve phishing for email or Microsoft 365 credentials or compromising a partnering organization. The malware can create persistence using Windows Registry Run keys or by adding an item in the startup folder, according to automatic analysis of the malware deployed in this manner.
It furthermore gathers comprehensive data about the operating system and the hardware on which it runs, as well as the device’s security status based on the OS version and patches installed.
The exploit is simple, but it might be highly effective because many users trust files sent through Teams, according to Avanan experts. Data from Teams-enabled institutions revealed that doctors freely discuss medical information on the network.
Individuals are generally wary of information received by email, but because of email phishing awareness training, they are not wary of files received via Teams. Additionally, Microsoft Teams allows for guest and external access, allowing for collaboration with persons outside the corporation. According to Avanan, these invites are frequently met with little monitoring.
“Because of the unfamiliarity with the Teams platform, many will just trust and approve the requests. Within an organization, a user can very easily pretend to be someone else, whether it’s the CEO, CFO or IT help desk” — Avanan
“The fact that default Teams protections are insufficient, since scanning for malicious links and files is limited,” according to the researchers, and “many email security solutions do not offer robust protection for Teams.”
Avanan suggests the following measures to counter such attacks:
- Enable security that downloads and inspects all files in a sandbox for dangerous information.
- Implement a comprehensive security solution that protects all lines of corporate communication, including Teams.
- Encourage end-users to contact IT if they encounter an unexpected file.
