Anyone can now generate bogus Chrome browser windows thanks to a new phishing toolkit
- March 22, 2022

Red teamers and cybercriminals may now develop successful single sign-on phishing login forms using phony Chrome browser windows thanks to the introduction of a phishing kit. It’s typical to see options to sign in with Google, Microsoft, Apple, Twitter, or even Steam when visiting websites. For instance, the DropBox login screen, as shown below, makes it possible to connect with an Apple or Google account.

A single-sign-on (SSO) browser window will appear when you click the Login in Google or App buttons, enabling you to input your credentials and log in with the account. These Windows have been trimmed down to just the login form and an address bar with the login form’s URL.
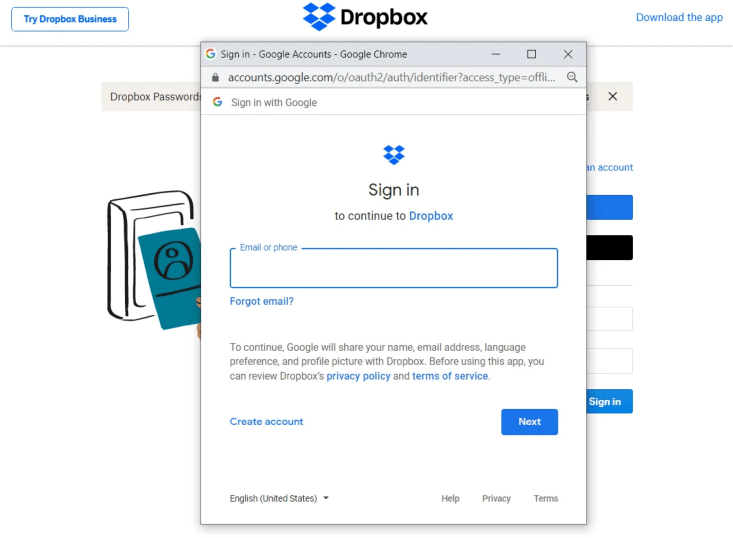
Cyber attackers have managed to generate false SSO windows in the past using HTML, CSS, and JavaScript, but the windows always have something odd about them, making them suspicious. This is where a new “Browser in the Browser (BitB) Attack” comes into play, in which prefabricated templates are utilized to build phony yet realistic Chrome popup windows with customized address URLs and headlines that can be used in phishing attacks.
To produce convincing phishing scams, this method generates false browser windows within genuine browser windows (Browser in the Browser). Mr.d0x, a security researcher, designed the Browser in the Browser attack templates, which he shared on GitHub. There are templates for Google Chrome for Windows and Mac, as well as dark and light mode variations.
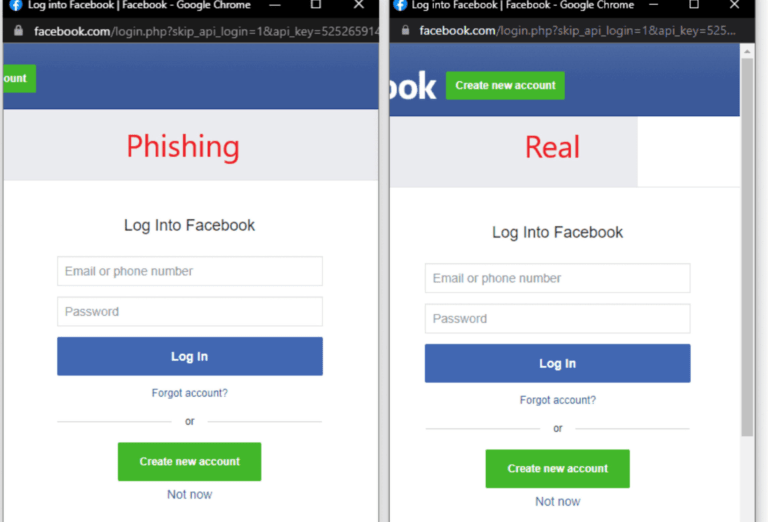
The templates, according to mr.d0x, are very easy to utilize in constructing realistic Chrome windows that present single sign-on login forms for any web platform. Redteamers, according to the researcher, can easily download the templates, modify them to include the desired URL and Window title, and then exhibit the login form using an iframe. It’s also feasible to insert the login form’s HTML directly into the template, but mr.d0x informed that you’d have to use CSS and HTML to align the form properly.
Kuba Gretzky, an inventor of the Evilginx phishing toolkit, put the new method to the test and demonstrated how well it worked with the Evilginx platform, implying that it might be used to obtain 2FA keys during phishing attempts.
Spoofing the reverse-proxied Sec-Fetch-Dest value to "document" worked like a charm and it's beautiful 🔥
— Kuba Gretzky (@mrgretzky) March 15, 2022
Evilginx loves it! ❤️
Kudos again to @mrd0x 🍻 pic.twitter.com/ODjblvNvho
According to mr.d0x, this is not a new technique, as Zscaler discovered it being used by rogue gaming platforms to obtain Steam credentials in 2020. However, now that prefabricated Chrome window templates are accessible, red teamers can use them to generate plausible phishing sign-in forms to test the defense of their clients or staff.
You may get the templates from GitHub if you want to try out the new Browser in the Browser phishing assault.
