“Defend the Web” write-up (Intro 9)
“Defend the Web” write-up (Intro 9— client code modification vulnerability)
This challenge is similar to the “Intro 6”.In this tutorial, we are not going to spend much time explaining what client code modification is. We are going to dive into the core of this challenge just exploiting it and having fun.
Let’s take a look at the challenge.
Ok, so here, we have username and password fields, which we do not have any information, and there is a third field for an email to request a password. Try to use bogus email and see if you can receive any information. If nothing interesting happens, then right-click on the email field and select the “Inspect Element” option to analyze it further.

When you analyze the email form field, please pay attention to the assigned value for that specific field.
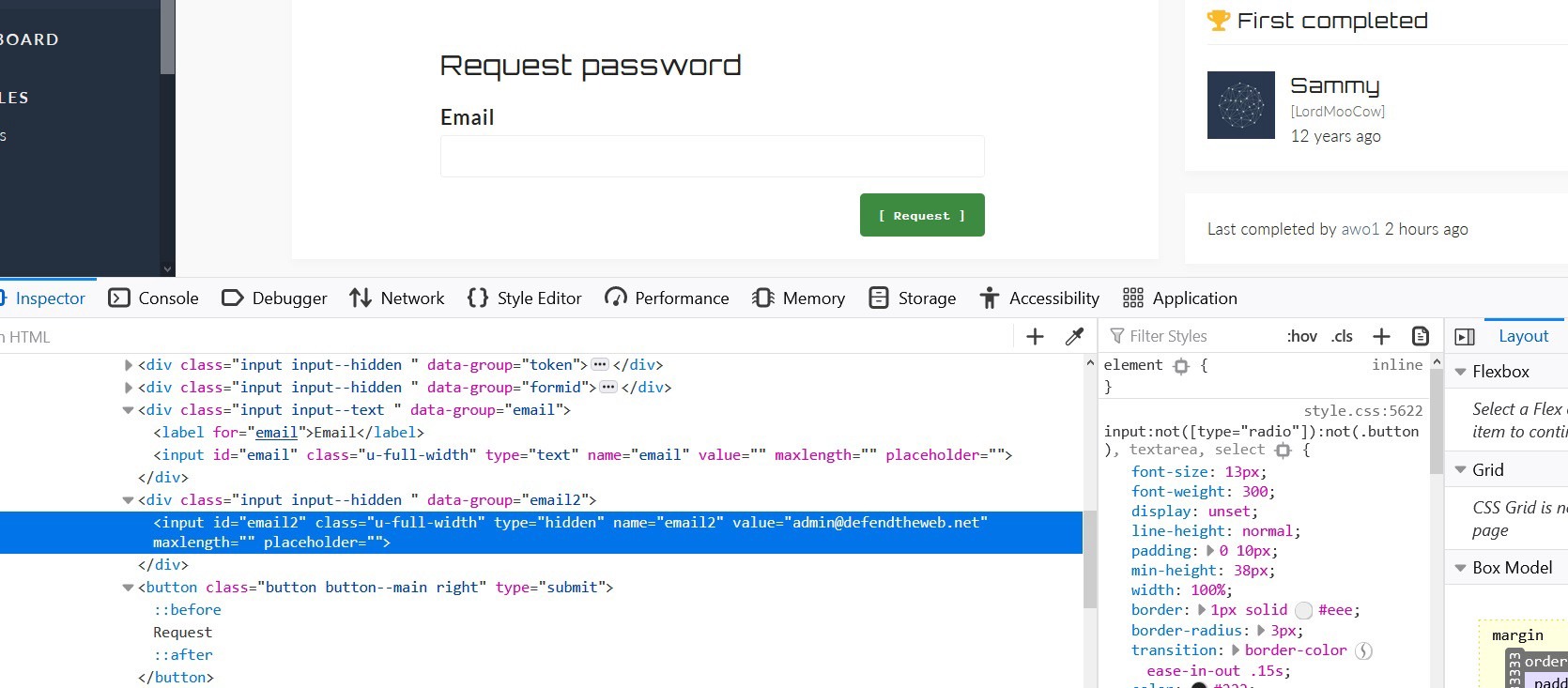
Looks like the value for “email2” is set to the default admin email account “admin@defendtheweb.net.” Double-click on the value field and change the default email to your own email and submit the request.

Once you submit the request, you should receive the user credentials.
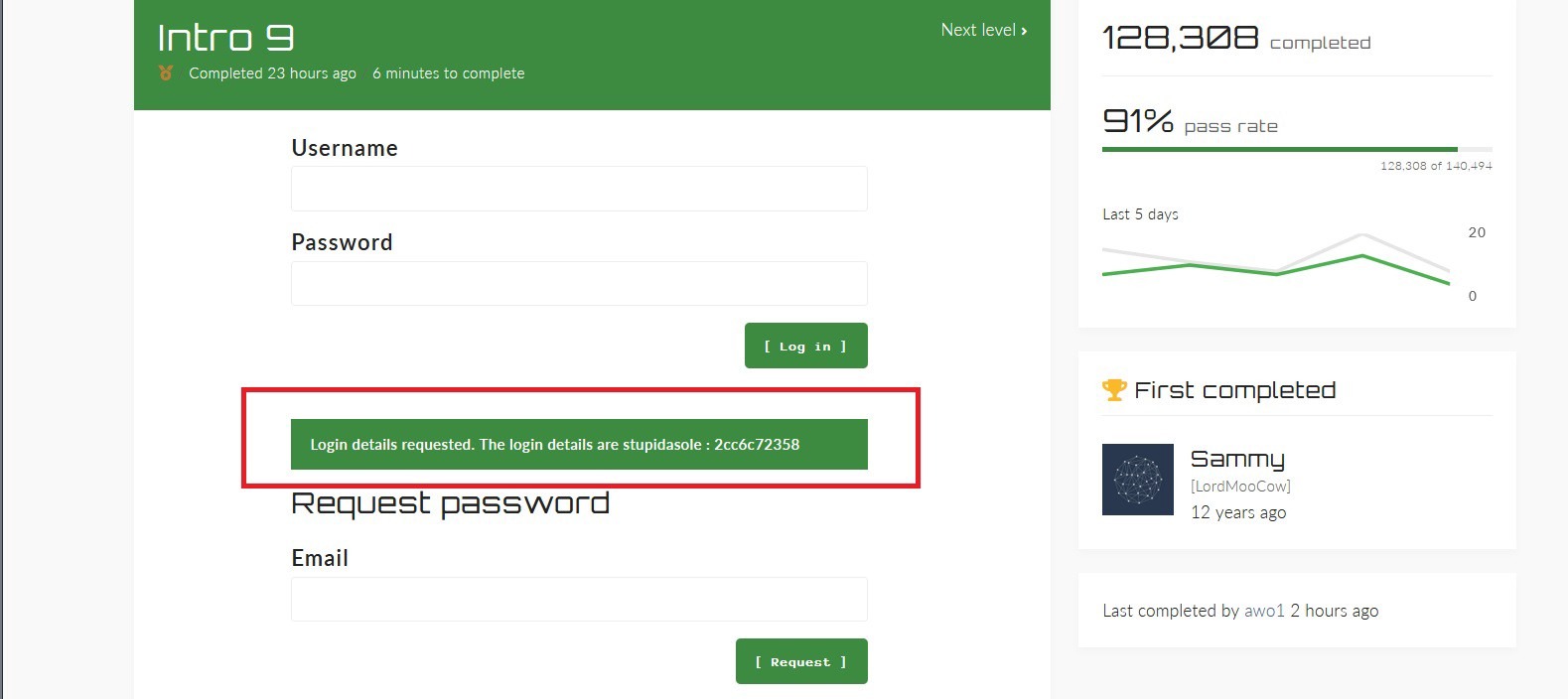
Copy and paste them into the username/password field to pass the challenge.
Use the least privilege technique to grant your users the fewest possible permissions to use the product. Hackers’ attack surfaces will be reduced. Limiting cases should have an appropriate output and action. Attackers try to confuse software by using codes and scripts that the software recognizes but for which there is no predefined reaction. Your code must be able to recognize and reject all sorts of input, even malicious ones. Include tools that help you distinguish your source code from that of others. Your source code is a key for hackers to locate and access databases, as well as your intellectual property.
There are numerous tools available for various programming languages, such as obfuscator for Visual Studio, which prevents reverse engineering and makes duplicating your source code extremely difficult. Using Code Access Security, ensure that your code operates in a variety of sandboxes without affecting its integrity. Validate all users and inputs. If the program works with money and important storage, user validation must have several clearances. Injection attacks will be prevented by validating data from all sources. Attack the code you’ve written. Get a white-hat hacker to look over your code and see if there are any holes or vulnerabilities. Perform a secure code review for all of your coding techniques. It is really important when developing software.
