“Defend the Web” write-up (Intro 6)
“Defend the Web” write-up (Intro 6— client code modification vulnerability)
Modified versions of programs are far more prevalent than you might imagine. There is a whole security sector dedicated to detecting and deleting illegitimate mobile app versions from app marketplaces. Organizations can have limited to extremely successful means of discovering unauthorized copies of code in the wild, depending on the approach adopted to solve the problem of detecting code change.
Binary patching, local resource modification, method hooking, method swizzling, and dynamic memory alteration are all included in this category. The code and data resources are stored on the mobile device once the program is downloaded. An attacker can edit the code directly, change the contents of memory dynamically, change or replace the system APIs that the application uses, or change the data and resources used by the application. This gives the attacker a clear way to undermine the software’s intended usage for personal or monetary benefit.
Depending on the nature of the modification, code modification can have a wide range of consequences. The following are examples of common types of impacts: Unauthorized new features, identity theft, or fraud are all possibilities.
In this particular challenge, we are asked to log in as an already existent user “raving_cute”. Let’s see how we can accomplish this.
Right_click on the “Username” field and select the “Inspect Element” option from the drop-down menu.

Locate the “Username” form filed and change the value of one of the available users. In this example, we are going to change “jTman’s” value to “raving_cute.” To do so, double-click on the name and then edit the field.
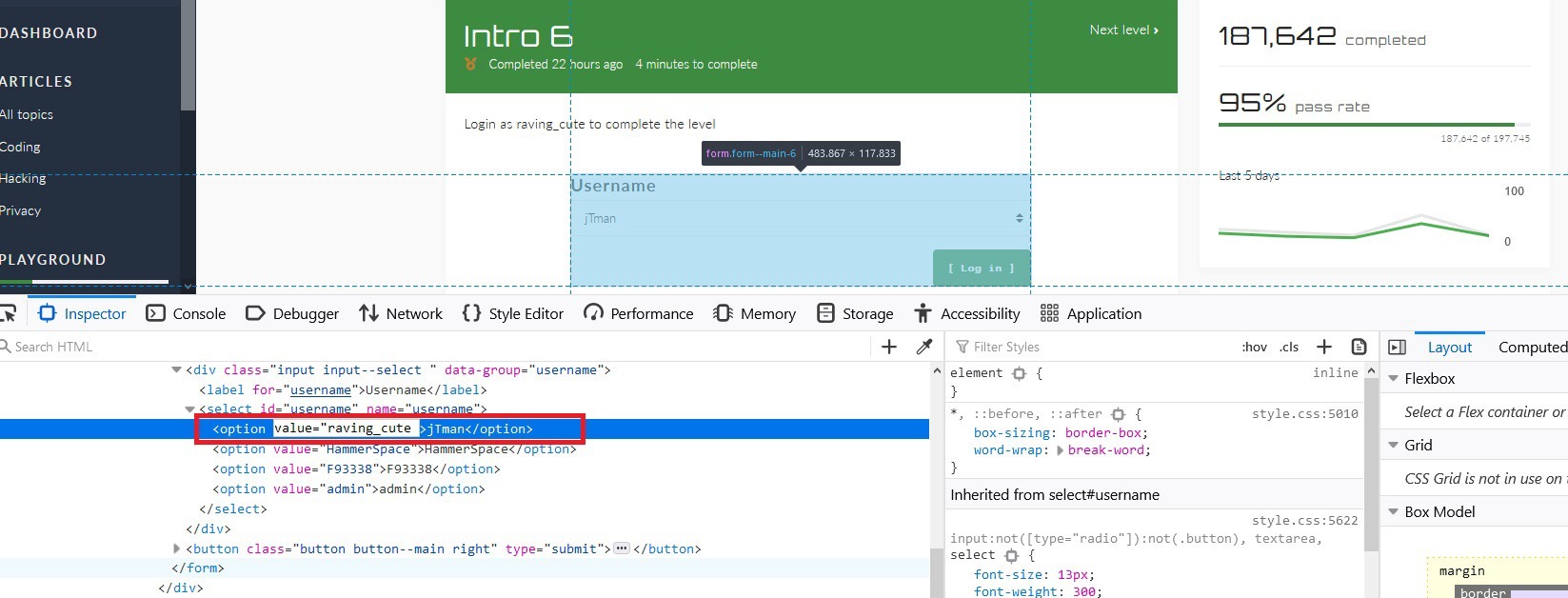
Once done, select the “jTman” username and click on the “Log in” button to access the page and finish the challenge.
