Keystroke capturing tool BeeLogger
Another python-based and fascinating key strobe capturing tool is “BeeLogger,” written by Chong Jin Wei. This tool can generate fake adobe flash updates, fake word documents, pdf, ppt, which are windows keyloggers. It includes some phishing methods and sends captured information every two minutes.
To obtain this tool, go to the BeeLogger’s GitHub page and copy the downloadable link.

Open your terminal and use the “git clone” command to download it.
Ex: (root@kali:/opt# git clone https://github.com/4w4k3/BeeLogger.git).
Next, change your directory to “/BeeLogger/” and run the following command “chmod +x install.sh” to make the installer file executable, then run it using the “./install.sh” command to start the installation process. After the installation is complete, you may begin the BeeLogger with the following command “python bee.py.”
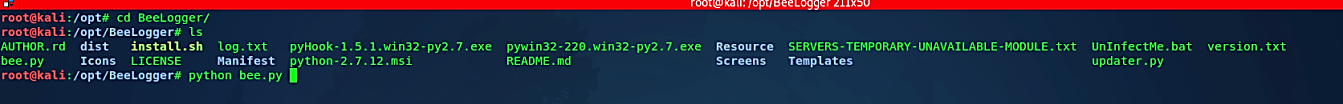

Once it starts, you will be presented with the page shown in the image above. Press “Enter” to continue. Next, type “k” to view options for generating a keylogger.
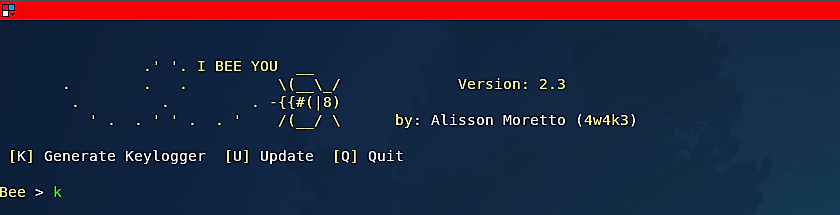
Out of six options, select one that you like and hit “Enter.”

Next, provide your email address and a password so the keylogger can send you captured data.

When the keylogger generating process is complete, it will be saved in the “BeeLogger/dist/” directory.

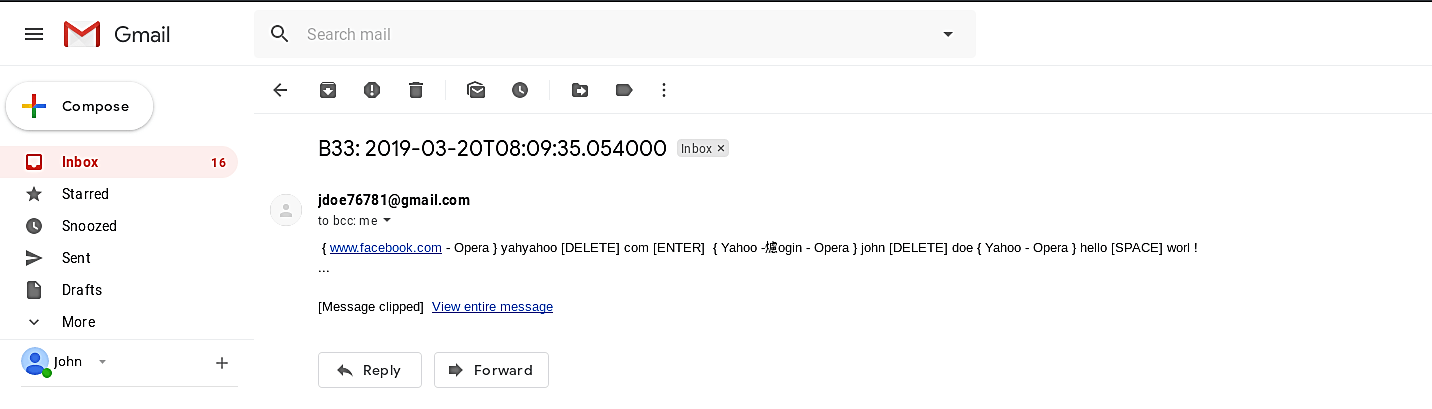
Now let’s send this executable file to our victim machine and start capturing key strobes. Once the program is run, it will begin logging every key typed on the keyboard and send a report to an attacker via email.


When you go back to the attacker machine and view your emails, you should be able to receive a report from BeeLoger with captured information.
Most antivirus companies have already added established keyloggers to their databases, making keylogger protection similar to defending against other forms of malicious software: install an antivirus product and keep its database up to date. However, since most antivirus products identify keyloggers as potentially harmful or undesirable programs, users should ensure that their antivirus software can detect this form of malware using default settings. If this is not the case, the product should be designed to defend against the majority of popular keyloggers.
