Vulnerability Assessment using Qualys
A vulnerability assessment is a way toward characterizing, distinguishing, ordering, and organizing vulnerabilities in computer frameworks, applications, and network infrastructures. To provide the organization an evaluation with the vital information, awareness, and risk background to comprehend the dangers to its condition and respond appropriately. Vulnerability assessment isn’t explicit to one industry; it connects all businesses extending from IT frameworks to Energy and other utility systems.
Vulnerability evaluations permit security groups to apply a steady, far-reaching, and precise way to deal with recognizing and settling security threats and risks. It has a few advantages to an organization:
- Early and predictable distinguishing proof of dangers and shortcomings in IT security.
- Remediation activities to close any holes and ensure sensitive systems and data.
- Meet cybersecurity compliance and administrative requirements for areas like HIPAA and PCI DSS.
- Ensure against information breaches and other unauthorized access.
There are different approaches to perform vulnerability evaluations; however, one of the most well-known is through automated vulnerability scanning software. These devices use databases of known vulnerabilities to recognize potential defects in your systems, applications, information, equipment, and many more. The vulnerability assessment tools will extensively scan each part of your network.
After the scanning, they will report on all the issues found, and recommend activities to expel dangers. The more full-highlighted scanning devices may offer insight into the security and operational effect of remediating a risk, as opposed to tolerating the uncertainty. Vulnerability scanning information may likewise be incorporated into a SIEM alongside other details for even more holistic threat analytics.
In this instructional tutorial, we will be focusing on different types of vulnerability scanning tools and discussing their functionality.
Qualys
Qualys Community Edition gives organizations the usability, adaptability, accuracy, and centralized management of the Qualys Cloud Platform, free of charge. This cloud-based offering enables associations to shield themselves from threats present in the wild without conveying any equipment or causing support costs.
Key Features:
- Map your entire IT infrastructure and discover all your assets, wherever they are — in the cloud or on-premises.
- Detect and survey vulnerabilities on inward and outer IT resources and frameworks.
- Scan an external or internal web application for vulnerabilities, including the OWASP Top 10.
- Customize dynamic dashboards to mirror your organization’s necessary security data.
- Qualys Community Edition Includes:
- 16 Cloud Agents.
- Vulnerability Management up to 16 Internal and 3 External IPs.
- Web Application Scanning for 1 URL.
- 1 Virtual Scanner Appliance.
- CloudView — for reviewing open cloud remaining burdens and foundation.
The Community Edition is a limited form of Express Lite, but scan functionality, full CVE coverage, and Six Sigma accuracy remain the same.
To use the cloud platform of Qualys, we need to register first. Once all the information is provided, Qualys will send you a confirmation email with the link to a login page of the web platform.
To perform a scan, first, we need to provide the IPs/ranges of the objective. From Qualys VM, go to the “Assets” tab and click the “Host Assets.” From the “New” menu, select the tracking method for your hosts.


By default, the “IP Tracked Hosts” option is selected. You can also track hosts by DNS or NetBIOS hostname, which enables reporting scan outputs in a dynamic networking system. For instance, if the hosts on your network are assigned IP addresses dynamically through DHCP, then you can use DNS or NetBIOS hostname tracking options.
In the “New Hosts” window, go to the “Host IPs” tab, and add new IP addresses for the webservers you want to scan. That’s it! The IPs will appear on your “Host Assets” list, and they will be ready for scanning.
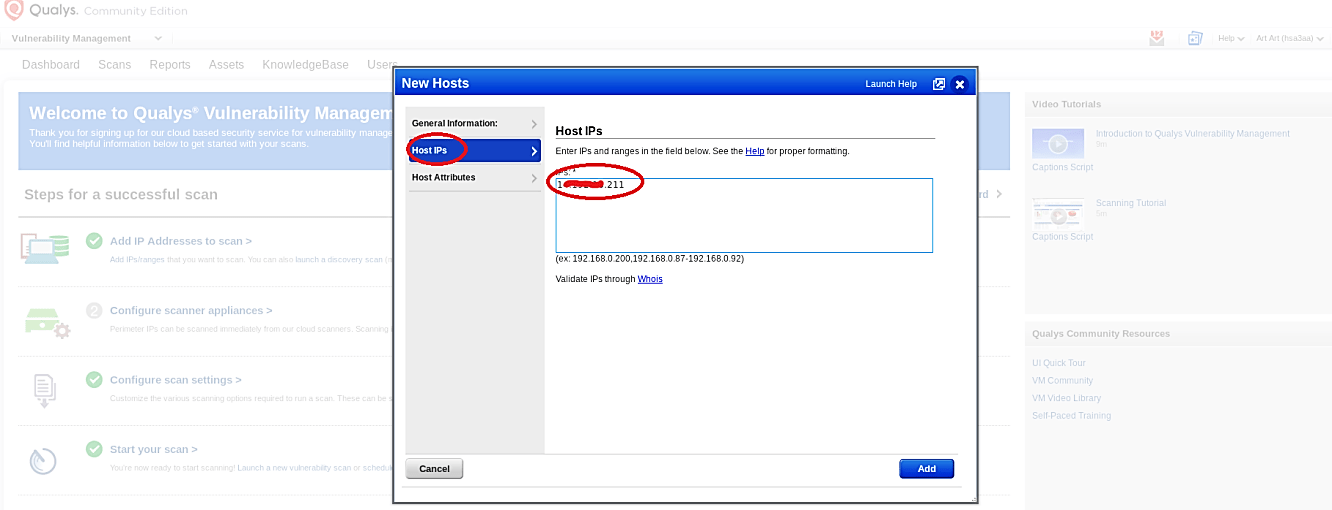
Next, return to the dashboard and select the “Start your scan” option to launch a vulnerability scan window. In the “Vulnerability Scan” window, provide some information related to the tile, option profile, and the IPs/Ranges then click on the “Launch” button to start the scanning process.

Once the scanning process is complete, Qualys will send you the scan results via email.

Click on the link provided to view all vulnerabilities based on their severity level.

The report also provides countermeasure techniques that you can apply to patch those problems.

