“Defend the Web” write-up (Recon)
Defend The Web – (Recon – Information gathering and finding B6-Key)
With regards to getting a clear data gathering idea, the least complex way of characterizing it would be the most common way of gathering data about something you are keen on. A pragmatic model: gathering data with your eyes is called visual insight. Similarly, in the digital world, a great deal of data can be assembled in various ways, not with your faculties, but rather with a few strategies, instruments, and procedures.
For those in the cybersecurity industry, this is the initial step to take during the prior phases of any hacking action, when any black or white-hat researcher needs to acquire however much data as could reasonably be expected with regards to the ideal objective. While it’s a fun activity for certain researchers, data gathering is additionally quite possibly the most tedious task during the intel-recon process, and that is the reason using time productively is so significant.
In this specific example, we will be doing a basic reconnaissance and inspecting the webpage to find the B6-Key header.

This challenge wants us to find the IP address of the webserver and the hosting company name. One of the easiest ways to find this type of information would be to use an online “Whois” service. Go to the following page: “https://www.whoishostingthis.com/” and search for the website’s name.
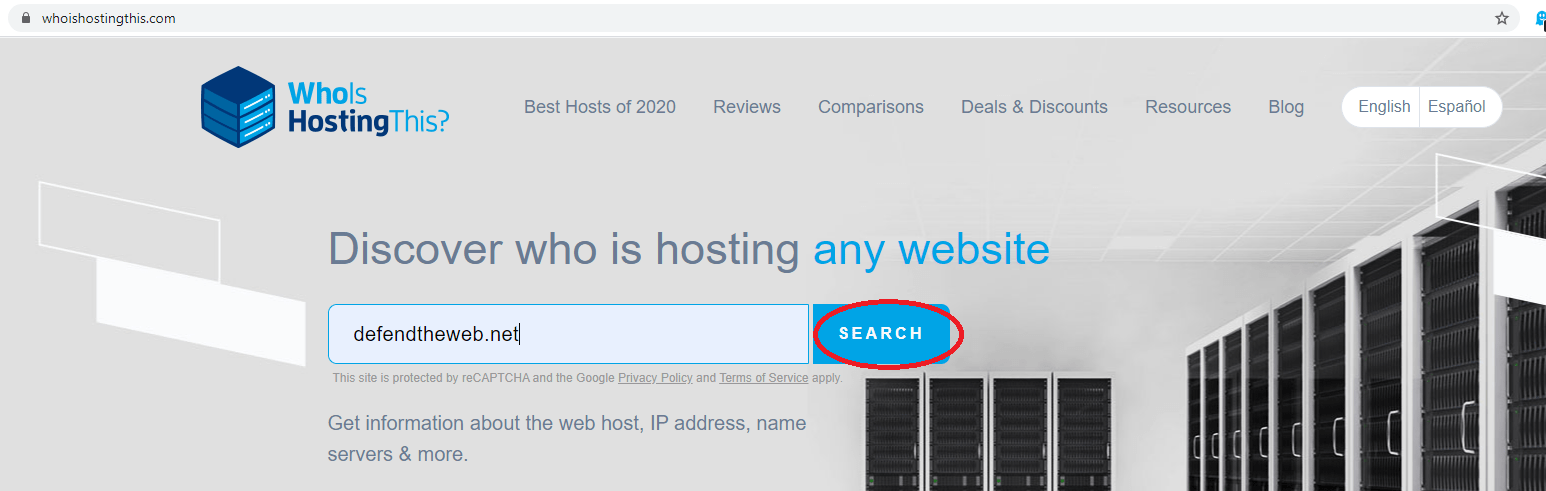
The “Whois” service can provide you with lots of good information including the IP address of the webserver and the name of the company that hosts it. Copy this information and note them somewhere because we will use them later on to finish the challenge.

Now that we found answers to two basic questions, it’s time to find the B6-Key header. To do so, we need to inspect the page and dig further.

From the source-code page go to the “Network” tab, and click on the “Doc” option shown in the screenshot below. Then refresh the page.
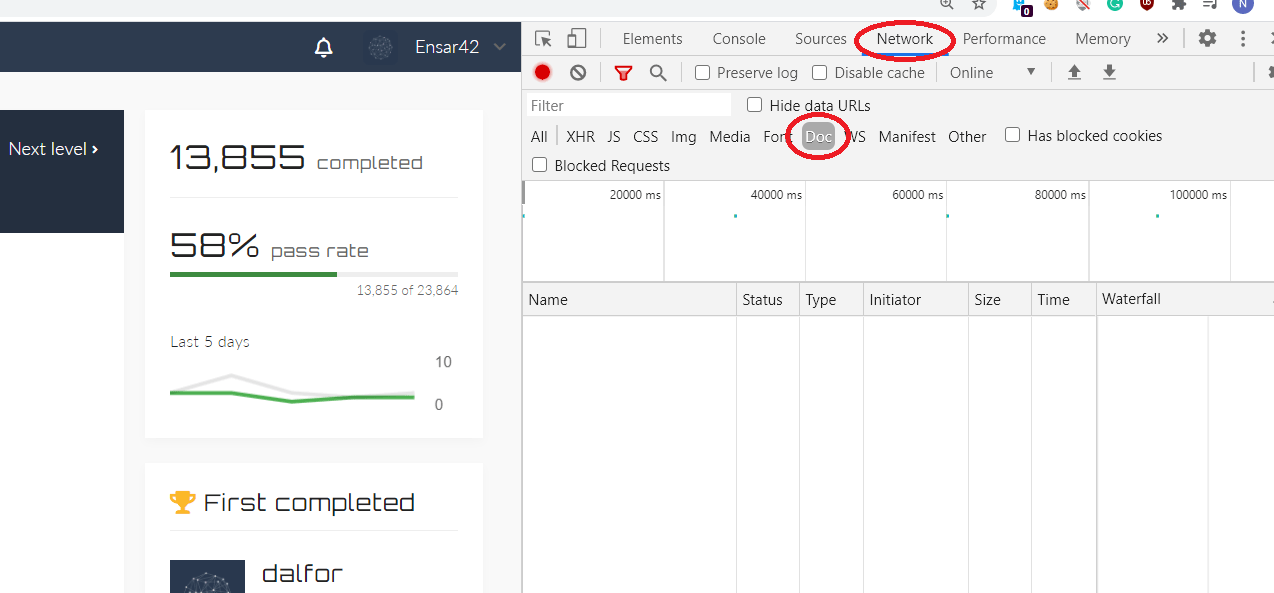
After the refresh, a file should appear under the “Network” tab on the source code page. Click on the file, and select the “Headers” tab. From the “Headers” tab search for “b6-key” and you’ll find the key.

Now let’s put all found information on the login page and try to access it

Congratulations! You have completed the challenge.

