Analyzing a bot-infected host with Wireshark
In this instructional exercise, we will be using a sample “.pcap” file that was created by the Chappell University (https://www.chappell-university.com/studyguide) to analyze an infected device.
Visit the website and download all trace files if you want to examine them in your lab environment. Here we will be covering a bot analysis with Wireshark, so we downloaded the “Trace File Part 1” zip file and used the “sec-sickclient.pcapng” trace file.
Let’s start analyzing the captured file by adding it to the Wireshark. Select the “File” tab and click on the “Open” option. In the “Wireshark-Open Capture File” window search for the “sec-sickclient.pcapng” file and click on the “Open” button.

Let’s start by analyzing our first packet. The host 10.129.211.13 goes to 10.129.56.6 and does a DNS query to “bbjj.househot.com.” Then it gets a response from the canonical name “ypgw.wallloan.com.” Let’s select that query and look closely in the information panel under the “Domain Name System (response)” option. You can see here that the “Answer RRs” show 12 records, which are very unusual for answer resource records to display. Generally, it should show one or two records, so this type of information triggers us to think that there is something funny going on. Now, host 10.129.211.13 will probe all IP addresses that are on the answer list, and try to accomplish some connections.

On the 3’rd packet, we can see that the host 10.129.211.13 goes to 216.234.235.165, and it makes an SYN request on port 18067. This is not s standard port, so 18067 can run anything on it. Generally, to SYN request, we should receive an SYN+ACK or RST response, but in this case, we received “ICMP Destination Unreachable,” which means there is a firewall or something installed. So it fails a few times, and then it directly queries “ypgw.wallload.com,” and we get a response from it. Let’s analyze packet No: 10 and view the “Domain Nama System (response).” As you can see, we found another “Answer RRs” with a high record value. This type of activity increases our suspicion.

Next, the client probes the first IP address. It communicates successfully and completes the three-way handshake. After that client sends a PSH flag, which is very unusual to see, we generally observe this type of action in telnet communication.

When you see something like this, you can use a “Follow TCP Stream” option to investigate further.
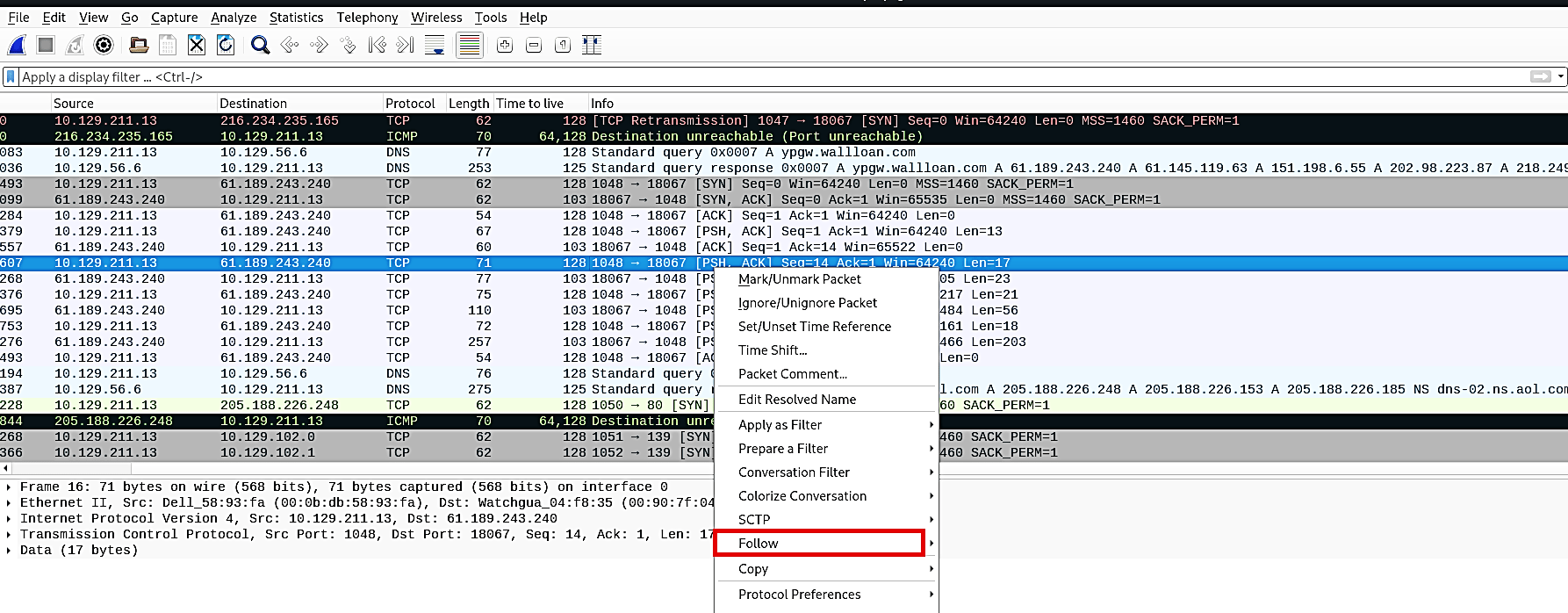
Right-click on the highlighted packet and select the “Follow” option. From the drop-down menu, click on the “TCP Stream” option, and it will show you the stream content.

Here we can accurately tell that this conversation is based on the user, nick, and especially join command information. It is IRC communication. Let’s see what this is trying to accomplish.

If we investigate it further and search for the first query “bbjj.househot.com” from Google, we can see that this is a bot activity. It tries to join password-protected IRC channels where the hacker can send commands to the bots to control them.

If you don’t want to miss this type of activity and detect them right away, let’s create a color filter. Highlight the “Answer RRs” then right-click and select the “Prepare a Filter” option. From the drop-down menu, click on the “Selected” option.

Wireshark will prepare a filter based on the selection you made.

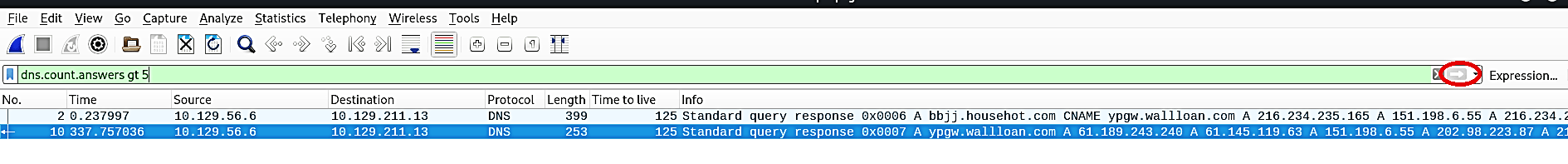
Change the selected field to “dns.count.answers gt 5” to detect all activities that have “Answer RRs” values higher than five, and then click on the “Apply” to see the changes.
Now let’s apply the coloring rule to it. Right-click on the packet and select “Colorize Conversation,” then select the “Ethernet” option. Click on the “New Coloring Rule…” option from the drop-down menu.
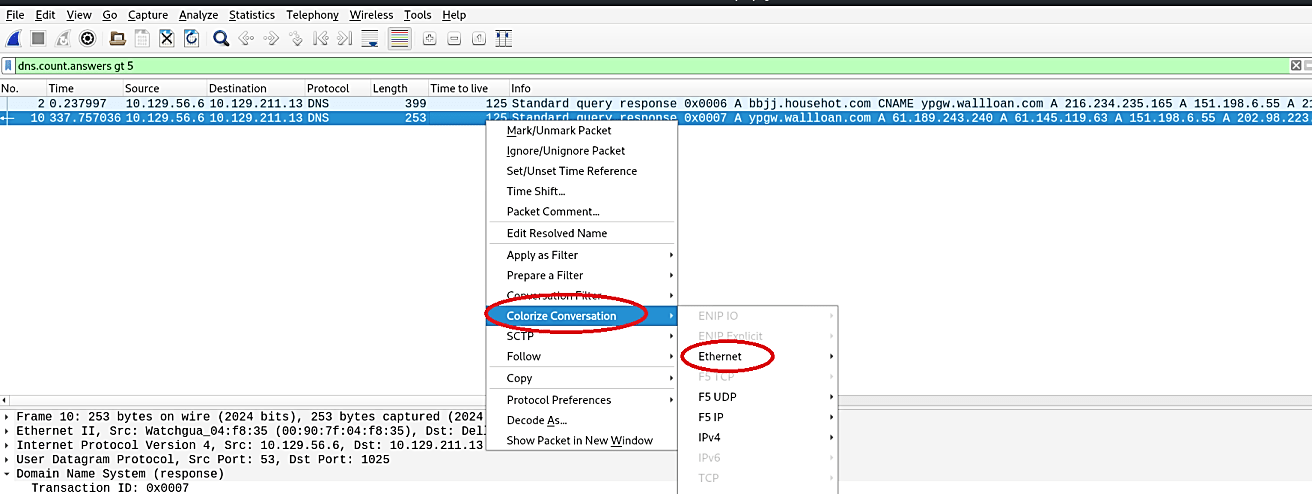
Then, click on the “+” icon to add a new rule on the new window.

Name your new rule, for instance, “DNS Answer RRs gt” and then specify the filter “dns.count.answers gt 5”. Lastly, pick the color for the background, and the foreground then apply it as a filter.

So, anytime your network experiences this type of traffic, you will be able to detect them right away.

