Analyzing patterns and signatures of an exploit using wireshark
In this instructional example, we will analyze a sample pcap file that has an exploit in it. To get this file, go to the “https://www.chrissanders.org/captures/” page and download the “aurora.pcap” sample file. Once you download it, click on the “File” tab and select the “Open” option.

From the “Open Capture File” window, select the “aurora.pcap” file that you have just downloaded and click on the “Open” button.
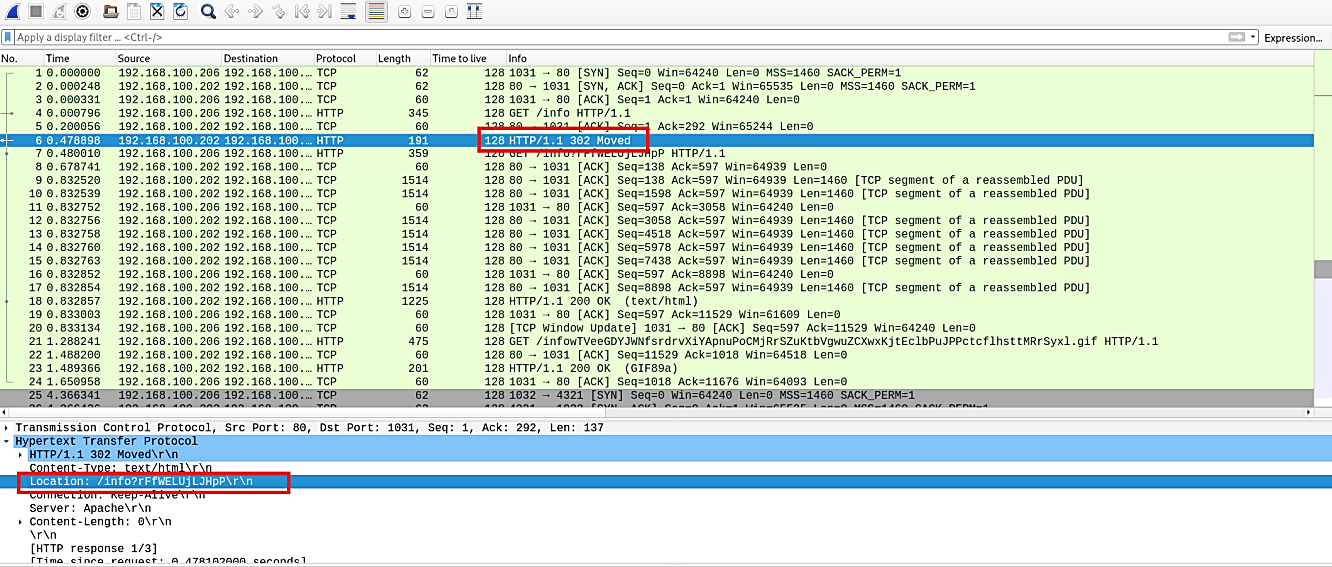
Now, when you analyze the traffic packets in Wireshark-like tools, you generally go one by one and look at every packet. When you come across a packet that looks a little bit suspicious, you stop there and try to investigate it further. Same for this example, we found an HTTP packet (6) that says “302 Moved.” This type of packet is not so common in network traffic. When you click on that packet and view the detail, you can see that it saved itself in a particular location.
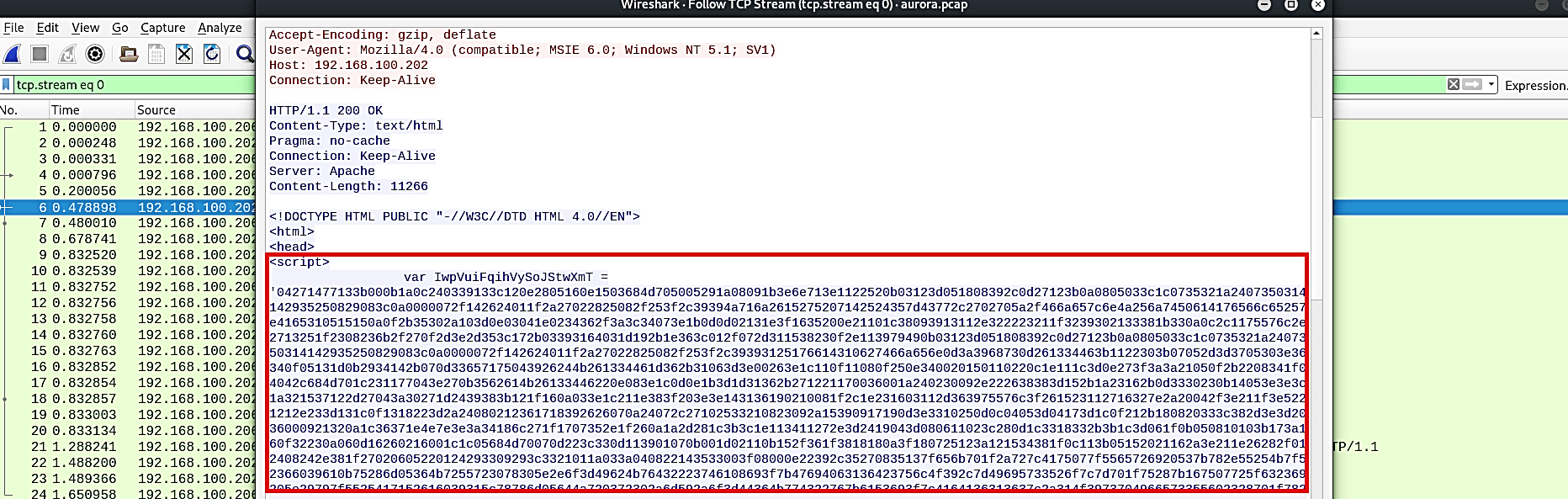
Sometimes the detail pane of Wireshark can’t give you the information that you want, so in this case, we should follow the TCP stream.

As you can see in the screenshot below, Wireshark was able to identify the file that was moved, and this file contains a script that can perform any sort of activity on the target device.
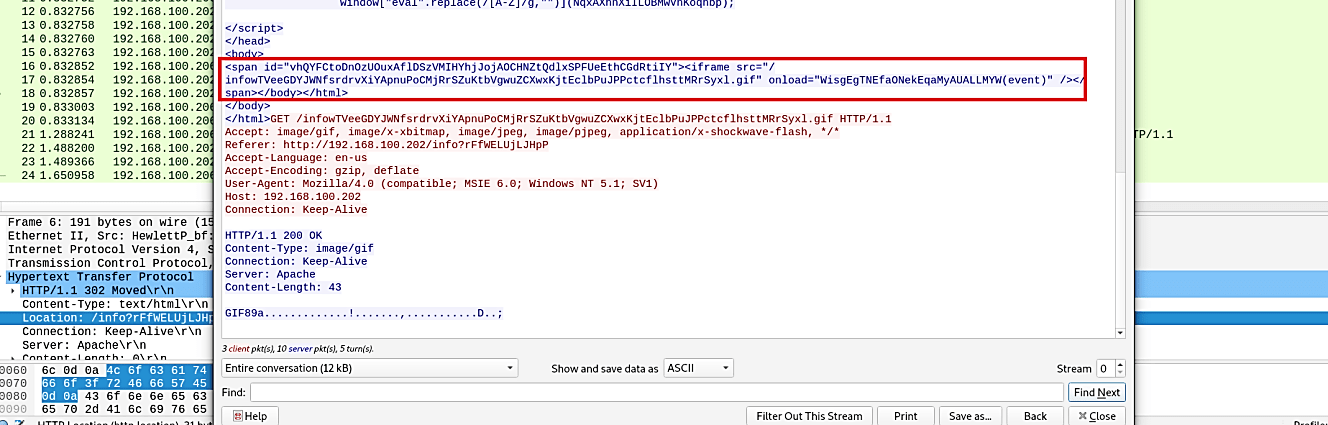
We can see our first three-way handshake after the file was moved down through the packets. Let’s analyze it with the TCP stream and see what we can find.

Based on the TCP stream outputs, we can say that the malicious file is executing internal commands without the victim’s acknowledgment.
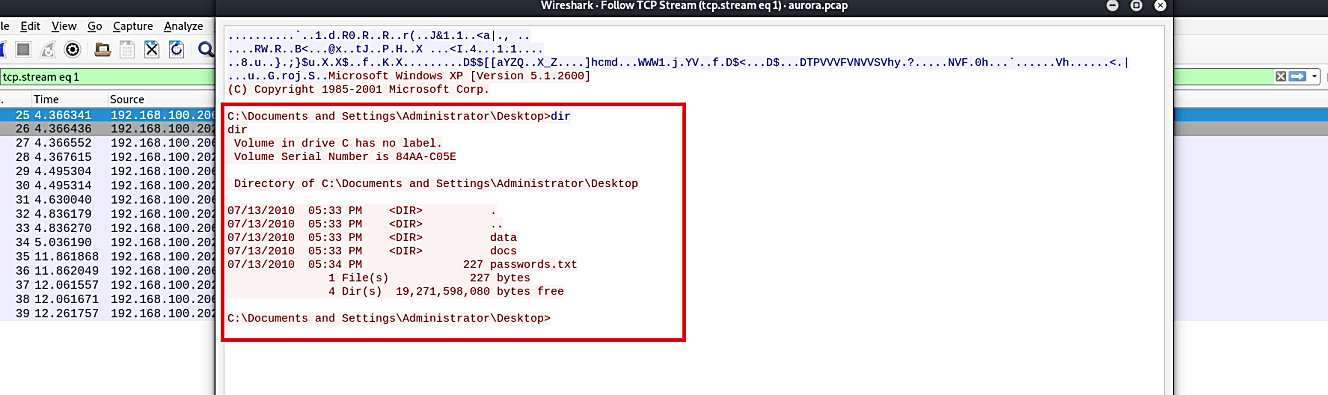
This type of activity indicates that the backdoor is installed on the target device and controlled by the attacker.
Note: If you want to practice and analyze more packets with different types of scenarios, visit “https://www.chrissanders.org/captures/“ or “http://malware-traffic-analysis.net/training-exercises.html“ to download sample “.pcap” files.
