Analyzing patterns and signatures of ARP spoofing using wireshark
ARP spoofing includes developing forged ARP replies. By sending forged ARP replies, an objective PC could be persuaded to send frames bound for PC A instead go to PC B. At the point when done appropriately, PC A will have no clue that this redirection occurred. The way toward refreshing an objective PC’s ARP reserve with a forged entry is alluded to as “poisoning.”
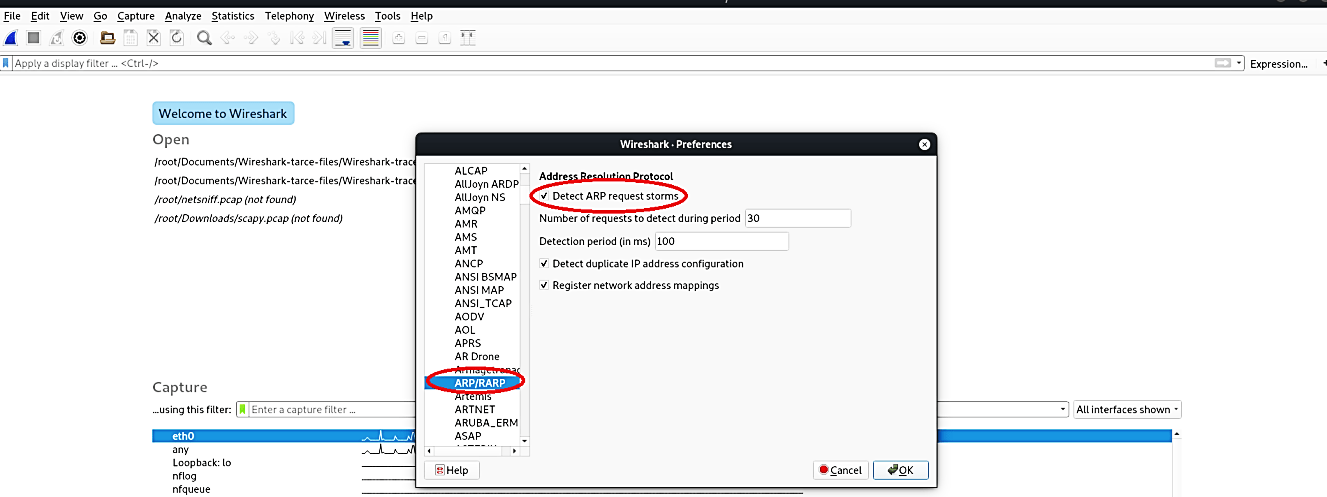
To automatically detect ARP packet storms and duplicate IP addresses, we need to perform some configurations on the Wireshark. First, click on the “Edit” tab and select the “Preferences…” option.

Under the “Protocols,” click the “ARP/RARP” option and select the “Detect ARP request storm” checkbox, and click “OK.” Wireshark is now ready to detect packet storms and duplicate IP addresses.
Let’s see this in action by scanning our network for live hosts.
Ex: (root@kali:~# netdiscover -i eth0 -r 10.10.10.1/24).

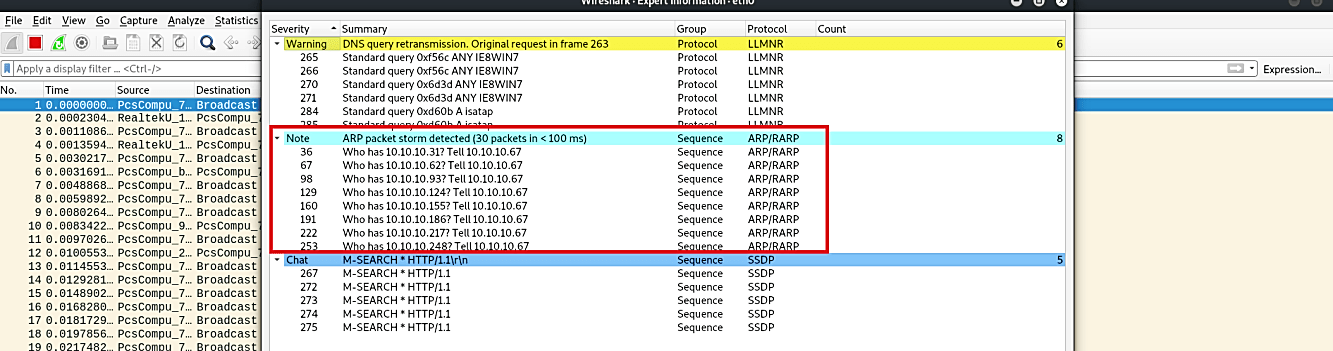
The screenshot below shows a vast number of ARP requests. To analyze it, click on the “Analyze” tab and select the “Expert Information” option from the dropdown menu.

In the “Expert Information” window, you will be presented with a bunch of useful information. The main point here is to look at whether the ARP packet storm was detected or not, which in this case, it did. If you experienced such traffic in your organization, this means that somebody is scanning your network.
To analyze duplicate IP address traffic, first, run the ARP spoof command from the terminal.
Ex: (root@kali:/opt# arpspoof -i eth0 -t 10.10.10.6 -r 10.10.10.1).
Then select one of the ARP packets and click on the “Analyze” tab followed by the “Expert Information” option from the drop-down menu.

Here we can see a warning telling us that the duplicate IP address has been detected, which is a clear indication of a spoofing attempt.

