Analyzing patterns and signatures of SYN flood attacks using wireshark
In an SYN flood, the assailant sends a high volume of SYN packets to the server utilizing spoofed IP addresses making the server send a reply SYN+ACK and leave its ports half-open, anticipating a reply from a host that doesn’t exist. In a more straightforward, direct attack, without IP spoofing, the assailant will utilize firewall standards to dispose of SYN+ACK packets before they reach him.
By flooding an objective with SYN packets and not responding to ACK, an assailant can without much of a stretch overpower the objective’s assets. In this express, the target battles to deal with traffic, which thus will expand CPU utilization and memory utilization, at last, prompt the exhaustion of its assets. Now the server will never again have the option to serve genuine customer solicitations and eventually lead to a Denial-of-Service.
In most cases, attackers will use the “hping3” tool or another tool to spoof IP random addresses. The line below lets us start and direct the SYN flood attack to our target 10.10.10.6.
Ex: (root@kali:~# hping3 10.10.10.6 -S -p 80 – -rand-source – -flood).

SYN flood assaults are very simple to recognize once you realize what you’re searching for. As you’d expect, a significant giveaway is the vast amount of SYN packets being sent to our target device.
Straight away, administrators ought to have the option to take note of the beginning of the assault by an immense surge of TCP traffic. We can filter for SYN packets without an affirmation utilizing the following filter: “tcp.flags.syn == 1 and tcp.flags.ack == 0.”
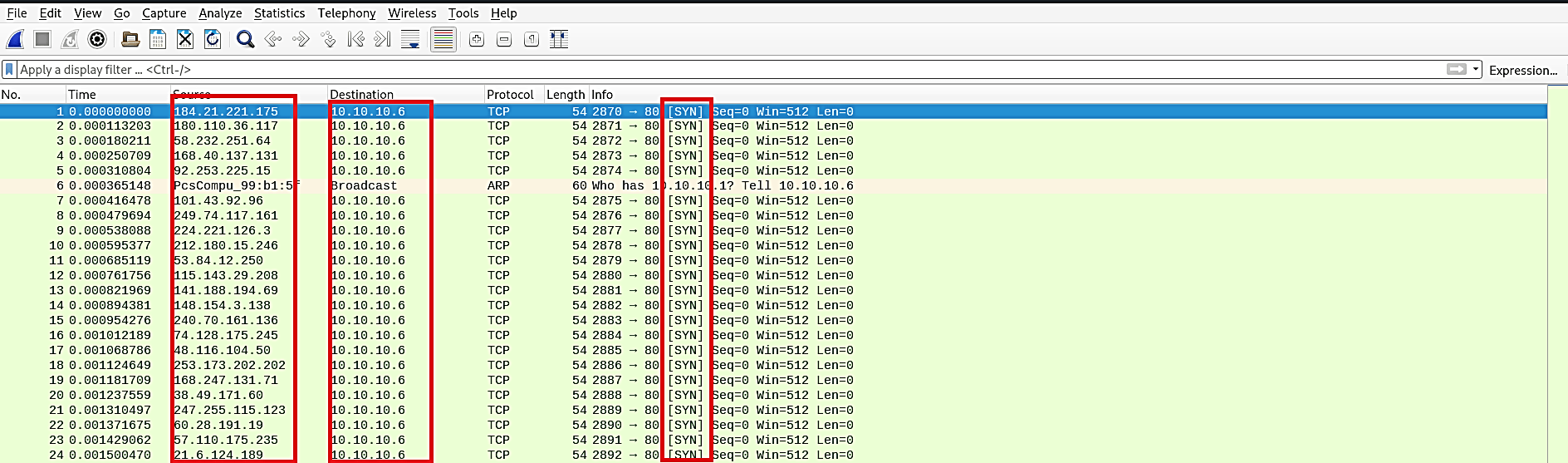
As should be obvious, there’s a high volume of SYN packets with next to no fluctuation in time. Each SYN packet demonstrates it’s from an alternate source IP address with a goal port 80 (HTTP), equal length of (0), and window size (512).
