Conduct red team engagements on WiFi with Wifiphisher
Wifiphisher is a rogue access point structure for conducting red team engagements or Wi-Fi security testing. Utilizing Wifiphisher, security analyzers can, without much of a stretch, accomplish a man-in-the-middle position against remote customers by performing focused on Wi-Fi affiliation assaults. Wifiphisher can be additionally used to mount victim altered web phishing assaults against the associated clients to capture credentials. WiFi-Phisher device utilizes the “Evil Twin” assault scenario.
Same as Evil Twin, the instrument initially makes a fake remote access point, disguising itself as the real Wi-Fi AP. It, at that point, coordinates a DOS assault against the genuine Wi-Fi or makes RF obstruction around it that disconnects remote clients of the association and prompts them to inspect accessible networks. When detached from the authentic Wi-Fi access point, the tool at that point forces offline PCs and gadgets to consequently reconnect to the evil twin, enabling the attacker to intercept all the traffic to that gadget. The technique is also known as AP Phishing, Wi-Fi Phishing, Hots potter, or Honeypot AP.
To download this tool, visit “https://github.com/wifiphisher/wifiphisher“ and clone it to your computer.
Ex: (root@kali:/opt# git clone https://github.com/wifiphisher/wifiphisher.git).
Running this tool by itself is OK, but we noticed that using it with “roguehostapd” is much better. You can get “roguehostapd” from the “https://github.com/wifiphisher/roguehostapd“ GitHub page.
After using Wifiphisher, we encountered some error messages telling us to install missing dependencies. If you have experienced similar problems, use the following command to fix them.
Ex: (root@kali:/opt# apt install libnl-3-dev libnl-genl-3-dev libssl-dev –y).

To install roguehostapd, navigate to its directory and change the mode of the “setup.py” file to executable.
Ex: (root@kali:/opt/roguehostapd# chmod +x setup.py).
Then, use the “python” command to start the installer.
Ex: (root@kali:/opt/roguehostapd# python setup.py install).

Use the same commands to install Wifiphisher.
Ex: (root@kali:/opt/wifiphisher# chmod +x setup.py),
(root@kali:/opt/wifiphisher# python setup.py install).

To run Wifiphisher from anywhere in the terminal, copy the “wifiphisher” executable file from the “/opt/wifiphisher/bin” directory to “/usr/bin/wifiphisher.”
Ex: (root@kali:/opt/wifiphisher/bin# cp wifiphisher /usr/bin/wifiphisher).

Once the installation process is complete, type “wifiphisher -h” anywhere in the terminal to start the tool and view all available options.

Now, let’s perform a Wi-Fi phishing attack without de-authenticating the clients. For this, we are going to use the “ –nodeauth” option.
Ex: (root@kali:~# wifiphisher – -nodeauth).
The tool looks for the appropriate Wi-Fi interface and opens in a GUI mode, as shown in the following screenshot.
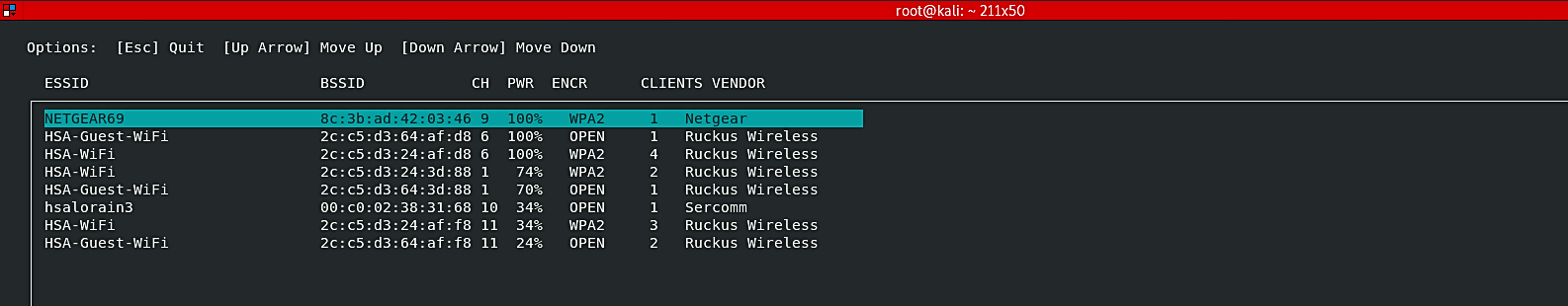
After the GUI interface is open, the tool searches for available Wi-Fi networks (ESSIDs) in the surrounding area. The target ESSID can be selected through the up/down arrow keys. Once the target network is selected, Wifiphisher will present you with all available phishing scenarios. One of the common situations is the “Firmware Update Page” option. It displays a router configuration page without logos or brands asking for WPA/WPA2 passwords due to a firmware upgrade. The beautiful part of this, it is mobile-friendly.
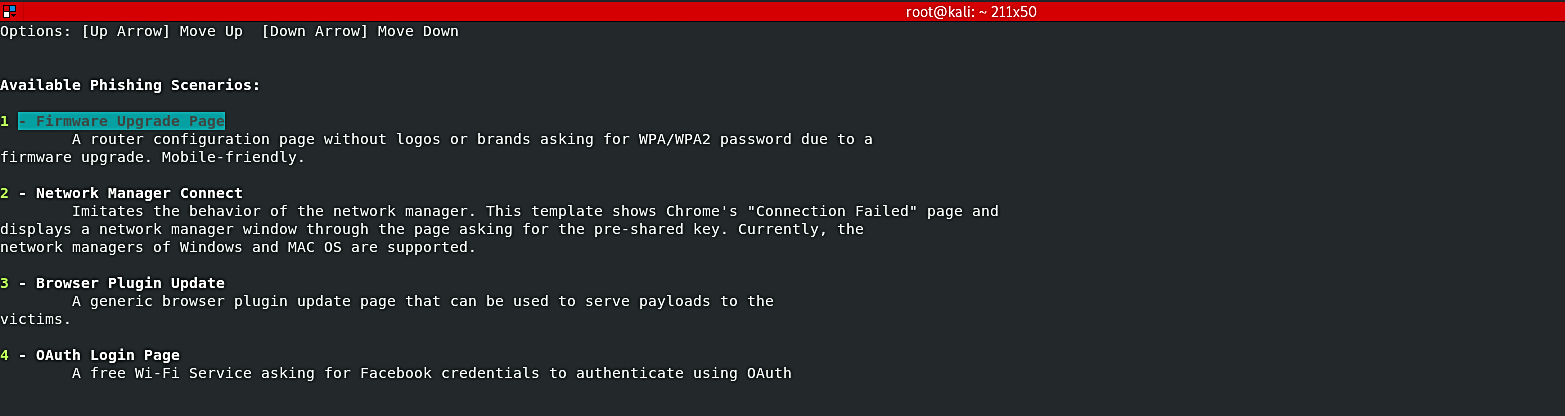
After choosing the assault type, it will promptly dispatch. A page will open to monitor for targets joining the system. Wifiphisher will likewise listen for devices trying to associate with networks that aren’t present, and it will make fake versions to lure those devices into connecting.

When the victim submits the credentials to start the upgrade, the fake progress page will appear and let the victim wait for about 10 minutes, making them go crazy.

Meanwhile, in the attacker’s computer, the script will exit and present you with the password you just captured.

Conclusion
Wifiphisher uses the Evil Twin attack to gain a man-in-the-middle spot, then redirects all HTTP requests to a phishing page managed by the attacker.
From the victim’s point of view, the attack is divided into three stages:
- The victim’s access point is being de-authenticated. Wifiphisher constantly jams all wifi devices within the range of the target access point by forging “Deauthenticate” or “Disassociate” packets to interrupt established associations.
- A rogue access point is joined by the victim. Wifiphisher sniffs the area and copies the settings of the target access point. It then generates a rogue wireless access point based on the target’s configuration. It also configures a NAT/DHCP server and routes the appropriate ports. Clients would finally start connecting to the rogue access point as a result of the jamming. The victim is MiTMed after this point.
- A believable, specially-customized phishing page is served to the victim. Wifiphisher uses a simple web server that can handle both HTTP and HTTPS requests. Wifiphisher will respond with a realistic fake page that asks for credentials or serves malware as soon as the victim requests a page from the Internet. This page will be tailored specifically for the victim. For example, a router config-looking page will contain logos of the victim’s vendor. The tool supports community-built templates for different phishing scenarios.
