Crack WPA/WPA2 Wi-Fi routers
The Wi-Fi WPS vulnerability has been known for years, so it scarcely qualifies as news. Then again, even after years, the general population has no clue that their home or small office Wi-Fi router is conceivably vulnerable against a simple hack! If you have a cutting-edge home or small office router with Wi-Fi and the WPS (Wi-Fi Protected Service) functionality, you might be in genuine danger of being compromised. Some accessible tools exploit a characteristic security imperfection inside the WPS framework and empower hackers to infer the router PIN and, consequently, your WPA/WPA2 pre-shared key or secret phrase! When somebody has your wireless secret phrase, they can gain admittance to about anything on your local network.
The tool used to exploit the WPS vulnerability is known as “reaver.” This exploit defeats WPS via an intelligent brute-force attack to the static WPS PIN. It can be misused to brute-force the WPS PIN and enable recovery of the WPA passphrase in an incredibly short period, as opposed to the standard attack on WPA.
Let’s take a look at one of the WPS cracking methods. First, we need to list all devices that have the WPS feature enabled by typing “wash – -interface [interface in monitor mode].”
Ex: (root@kali:~# wash – -interface wlan0mon).

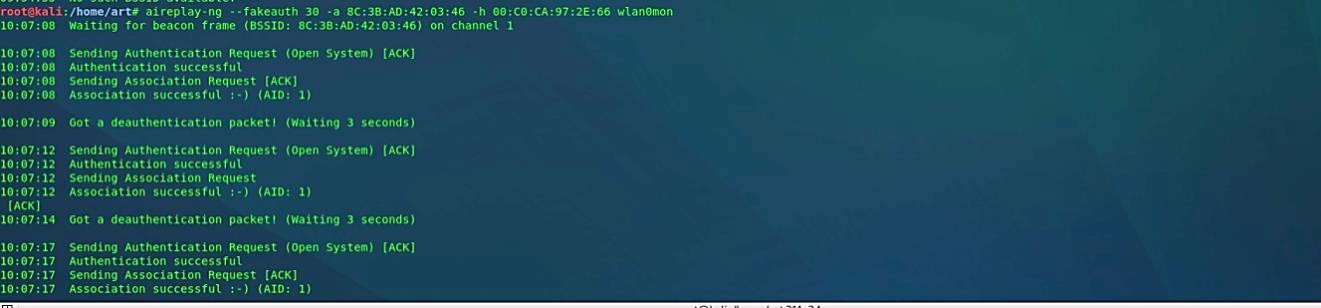
As you can see in the image, it shows the available network that has the WPS feature enabled. Now we need to authenticate our wireless adaptor to the target AP running the aireplay-ng command “aireplay-ng – -fakeauth 30 -a [BSSID of target AP] -h [MAC address of Wi-Fi adaptor] [interface in monitor mode].”
Ex: (root@kali:~# aireplay-ng – -fakeauth 30 -a 8C:3B:AD:42:03:46 -h 00:C0:CA:97:2E:66 wlan0mon).
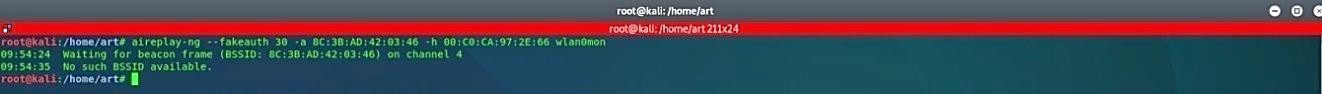
If, for some reason, you get the error like in the image below, then run the “reaver” command first and repeat the aireplay-ng.
Next, we need to start “reaver” to crack the WPS PIN “reaver – -bssid [BSSID of a target AP] – -channel [channel] – -interface [interface in monitor mode] -vv – -no-associate.”
Ex: (root@kali:~# reaver – -bssid8C:3B:AD:42:03:46 – -channel 1 – -interface wlan0mon -vv – -no-associate).
Here “-vv” means the verbosity of the reaver’s outcomes, and “ – -no-associate” means not to associate our wireless adaptor to the target AP. We need to specify this last option because we have already associated ourselves with the target AP using fake authentication. You may disregard the phony authentication step and directly run the “reaver” command, it should automatically associate us to the target, but we noticed that it is not reliable and doesn’t work most of the time.

Now we need to wait for a “reaver” to crack the pin, this should take about 10 minutes.
When you run this attack, some routers will present a warning: “WARNING: Detected AP rate limiting, waiting 60 seconds before re-checking”. If this is the case, while “reaver” is running, type a command below to flood the router and reset it.

Countermeasures:
- Disable WPS: Analyze whether your Wi-Fi AP needs to be using WPS at all. (Some routers do not provide in their configuration interfaces to allow you to disable WPS. Some of them will enable you to disable PIN-based WPS authentication while still using push-button authentication. Some routers offer the opportunity to disable WPS, but this option does nothing, and WPS can be enabled without your knowledge. In 2012, this vulnerability was found on every Linksys and Cisco Valet wireless access points as tested.)
- Increase the timeout period: For advanced routers, we can increase the Receive Timeout to slow down the attack.
- WPS Lock: Set the WPS Lock time to a large value.
- MAC Filtering: Of course, the old dog, but sometimes can protect against script kiddies.
- Physically Secure the Router.
- Some routers don’t support WPS at all. These are probably the most secure.
How to capture the handshake
In new routers by default, PIN authentication is disabled, and push-button authentication is enabled. So, cracking WPS is no longer an easy step anymore. For this particular case, we should break the WPA/WPA2 passwords. WPA/WPA2 underpins numerous kinds of authentication beyond pre-shared keys. Aircrack-ng can ONLY crack pre-shared keys.
So ensure airodump-ng shows the network that has the authentication type of PSK, otherwise, don’t even bother trying to break it.
There is another critical distinction between cracking WPA/WPA2 and WEP. It is the methodology used to break the WPA/WPA2 pre-shared key. Unlike WEP, where measurable strategies can be utilized to accelerate the cracking procedure, only plain brute-force methods can be utilized against WPA/WPA2. It is because the key is not static, so collecting IVs like in WEP encryption does not speed up the attack. The only thing that gives the information to start an attack is the handshake between the client and the AP.
Handshaking is done when the client interfaces with the network. Since the pre-shared key may be from 8 to 63 characters long, it viably ends up challenging to break the pre-shared key. The only time you can brute-force the pre-shared key is on the off chance that it is a dictionary word or moderately short in length. On the other hand, on the off chance that you need to have an unbreakable wireless system at home, use WPA/WPA2 and a 63 character secret key made out of arbitrary characters, including special symbols.
The effect of utilizing a brute-force approach is generous. Since it is incredibly computing-intensive, the regular PC can test 50 to 300 conceivable keys every second contingent upon the CPU and GPU. It can take hours, if not days, to crack through extensive dictionary words. If you are pondering creating your secret phrase list to cover every one of the changes and mixes of characters and unique symbols, check out this brute force time calculator link first (http://lastbit.com/pswcalc.asp). You will be exceptionally astonished at how much time is required to brute-force one.
Without further ado, let’s get started by capturing the handshake between the client and the target AP. Type this command in the terminal “airodump-ng – -bssid [BSSID] – -channel [channel] – – write [file name for output] [interface in monitor mode].”
Ex: (root@kali:~# airodump-ng – -bssid 8C:3B:AD:42:03:46 – -channel 1 – -write test wlan0mon).

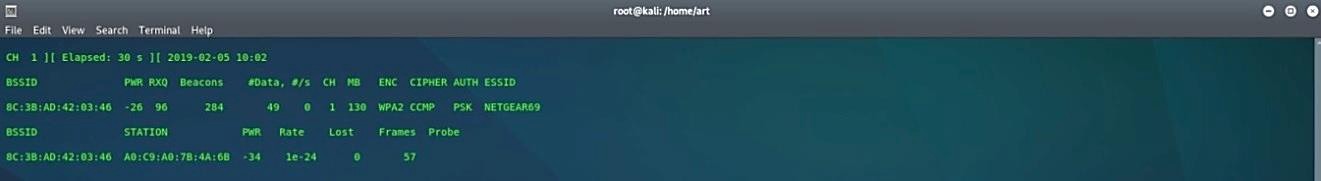
Now we can do two things;
1. Wait until one client connects to the target AP. Once it links to the target AP, it’ll generate traffic so we can get the handshake.
2. We can de-authenticate any connected client for a few seconds; once it reconnects back, we can get the handshake.
In this example, we are going to use the second option because the first one is self-explanatory.
To de-authenticate a specific client in a network, type “aireplay-ng – -death [number of packets] -a [BSSID of AP] -c [BSSID of a target] [interface in monitor mode].”
Ex: (root@kali:~# aireplay-ng – -deauth 4 -a 8C:3B:AD:42:03:46 -c A0:C9:A0:7B:4A:6B wlan0mon).

As it is shown in the screenshot, we were able to capture the handshake, and it was saved in a file named “test.” Now it is time to crack it using the word list.
Creating a wordlist
Kali Linux comes with some pre-loaded wordlists that you can use for this particular purpose. These wordlists are located in the “/usr/share/wordlists” location. In this tutorial, we would like you to show another popular method of creating a wordlist using “Crunch.” “Crunch” is a tool designed for generating wordlist, which can be used to brute-force or audit password strength. This tool can use patterns to reduce wordlist size, can compress output files in various formats, and now includes a message showing the size of the wordlists that will be created. You can create a custom wordlist using “Crunch” to crack someone’s Wi-Fi password if you have collected some information using social engineering. We will discuss more on social engineering later in this book.
To install this tool, use the “apt-get” command.
Ex: (root@kali:~# apt-get install crunch).
For more information on how to use this tool, please view the “help” or “man” page.
Ex: (root@kali:~#crunch – -help) or (root@kali:~#man crunch).
Some of the options are as follows:
· -b: Maximum bytes per file. So by using this option, the wordlist can be split into different sizes such as KB / MB / GB (must be used in combination with the “-o START” switch).
· -c: Number of lines to write to the output file (must be used together with “-o START” switch).
· -d: Limits the number of continuing identical characters (crunch v3.2).
· -e: Specifies when crunch should stop early (crunch v3.1).
· -f: Path to the charset.lst file to use, standard location is “/pentest/passwords/crunch/charset.lst” to be used in conjunction with the name of the desired charset list, such as “mix-alpha-numeric-space.”
· -i: Inverts the output sequence from left-to-right to right-to-left
(So instead of aaa, aab, aac, aad, etc., the output would be aaa, baa, caa, and daa).
· -l: When specifying custom patterns with the “-t” option, the “-l” switch allows you to identify which of the characters
should be taken as an actual character instead of a place holder (@, %, ^).
· -o: Allows you to specify the file name/location for the output, e.g., /media/flashdrive/wordlist.txt.
· -p: Prints permutations of the words or characters provided in the command line.
· -q: Prints permutation of the words or characters found in a specified file.
· -r: Resumes from a previous session, the same syntax to be used followed by “–r.”
· -s: This allows you to specify the starting string for your wordlist.
· -t: This allows you to specify a specific pattern to use. Probably one of the most important functions! Place holders for fixed character sets are;
““– upper case characters, “@”– lower case characters, “^”– special characters, and “%”– numeric characters.
· -u: Suppresses the output of wordlist size and line count before starting wordlist generation.
· -z: Adds support to compress the generation output, supports gzip, bzip, and lzma.
Now, let’s run “Crunch” to generate some word list. To do so, type “crunch [min char] [max char] [char combinations] -t [pattern] -o [File name to output].”
Ex: (root@kali:~# crunch 9 9 qwertyuiopasdfghjklzxcvbnm1234567890 -t p@@@@@@@7 -o wordlist.txt).

Using a wordlist attack
To crack the password, run the aircrack-ng command “aircrack-ng [output file that captured handshake] -w [wordlist].” Aircrack-ng will test every possible word combination in the “wordlist.txt” file against the captured handshake in the “test-01.cap” file to find a key.
Ex: (root@kali:~# aircrack-ng test-01.cap -w wordlist.txt).


Let’s take a look at the screenshot of a previous section for a moment. As you can see, the “Crunch” tool came up with 78364164096 words and saved them in a text file called “wordlist.txt.” This text file occupies almost 730 GB of space on a PC, and it’ll take years or even decades to crack the password, but eventually, it will succeed. In the real-life scenario, it is not practical to use this method if the password you are trying to crack is more than five characters long. If you think waiting years in the hope of getting your password cracked is worth it, then do not hesitate and implement this method; if it doesn’t worth it, then forget about it and move on to different techniques.
