Creating a fake access point using Mana-Toolkit
MANA-Toolkit is a set of tools for rogue access point (evilAP) attacks and wireless MITM. More specifically, it contains the improvements to KARMA attacks implemented into hostapd, as well as some useful configurations for conducting MITM once you’ve managed to get a victim to connect.
Mana has recently been added to the Kali Linux repositories, which means it’s automatically available to download and install by merely running the “apt-get install mana-toolkit” command.
Once it’s installed, navigate to the Mana directory located at “/usr/share/mana-toolkit,” and then enter the folder named “run-mana.” Here you’ll find several scripts used to control how Mana operates. Mana has three main start scrips;
1. Start-noupstream.sh — starts fake AP with no internet access
2. Start-nat-simple.sh — starts fake AP with internet access
3. Start-nat-full.sh — starts fake AP with internet access, automatically begins sniffing data, and bypasses the HTTPS.
Before starting the rouge AP using Mana-Toolkit we need to make a few configurations in “/etc/mana-toolkit/hostapd-mana.conf” and “/usr/share/mana-toolkit/run-mana/start-nat-simple.sh.”
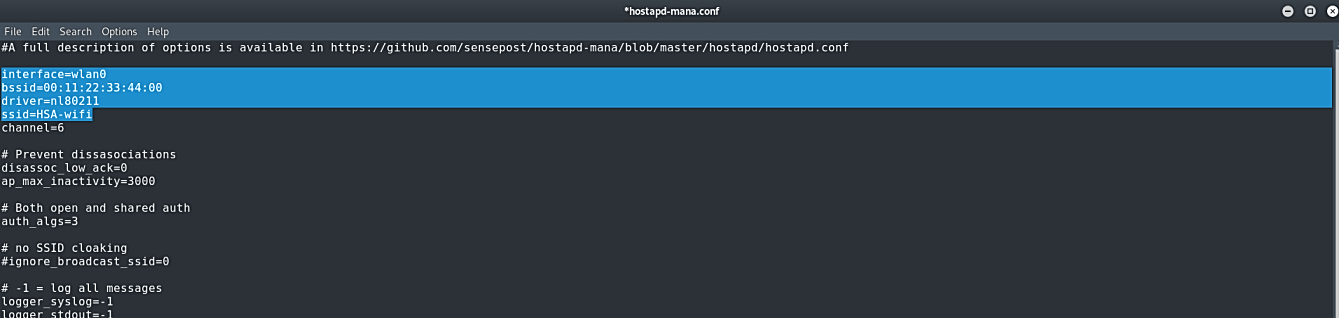
In the “hostapd-mana.conf” file we should edit the interface in which our wireless adaptor is connected and add a fake SSID name.
Ex: (root@kali:~# leafpad /etc/mana-toolkit/hostapd-mana.conf).
Then we need to modify mana start scripts according to our needs. Here, edit the “upstream” and “physical” interfaces. For the “upstream,” specify the interface of your internet source, and for the “physical,” provide the interface of your Wi-Fi adaptor that acts as a fake AP.
Ex: (root@kali:~# leafpad /usr/share/mana-toolkit/run-mana/start-nat-simple.sh).

Now we are ready to start fake AP by typing this command “bash /usr/share/mana-toolkit/run-mana/start-nat-simple.sh.”
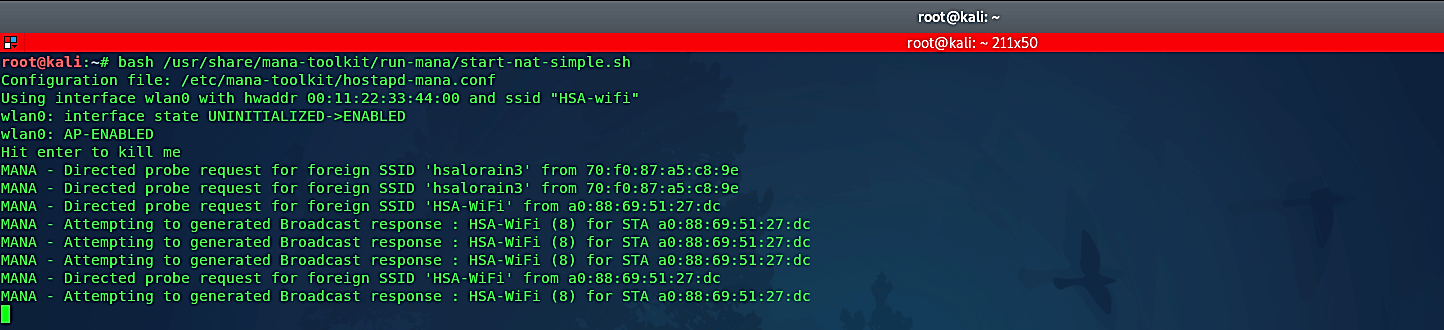
Mana will now be advertising a wireless network named “HSA-wifi,” as well as attempting to spoof other systems as it sees SSID broadcasts from clients searching for previously connected access points.
This tool incorporates the important setup files to capture credentials on various famous websites; obviously, not all are currently supported. As Mana is still being developed, additional sites and services are as yet being included. Meanwhile, the engineers recommend utilizing the effectively available code as a layout to redo your Mana establishment for your particular needs and targets.
The main Mana script dumps out a somewhat overpowering measure of continually updating data, and it tends to be extremely hard to decipher as everything passes by. It’s in this manner simpler to physically check the SSLstrip logs to search for captured credentials than attempting to read them from the script’s output. The original SSLstrip log document is situated at “/var/lib/mana-toolbox/sslstrip.log,” which holds all the previously SSL information that Mana managed to capture.
