Creating macro files
Any reasonable person would agree that Microsoft Office and OpenOffice are probably the most popular applications on the planet. We use them for composing papers, making slides for introductions, breaking down deals or budgetary information, and more. This product is so vital to organizations that, even in developing nations, specialists that are capable of an Office suite can make a reasonable living relying on this ability alone.
Sadly, high popularity for programming likewise implies more high-esteem focuses according to an attacker, and malware-pervaded Office macros resemble an irritating rash that doesn’t leave for IT experts.
A macro is an element that enables clients to make robotized forms within an archive utilized by software like Microsoft Word, Excel, or PowerPoint. It is used to upgrade client experience, increment efficiency, or mechanize generally manual assignments. But, in other words, it executes codes. What sort of codes? Anything you desire, even a Meterpreter session.
Macro attacks are nothing new or unusual. A typical attack usually involves embedding malicious macro code in the Microsoft Office document, sending it to the victim, and asking him/her to enable that code. The saddest part isn’t how lame the attack is since you are begging the victim to run your malware. It’s that people have been falling for this trick for decades.
In this section, we will show you how to make a macro file using the “Empire” tool and Microsoft Office product. Without further ado, let’s get started.
Run the “Empire” tool from the terminal and use the stager “windows/macro.”
Ex: ((Empire: Listeners) > usestager windows/macro).
Then use the “info” command to list all available options.

Next, we need to set the “Listener” and “OutFile” options.
In this example, we will use “http_empire” as a listener that we have created in our previous lectures and save the file in the “var/www/html/Evil-Files/” directory as “macro_empire.” Once you run an “execute” command, it will save a malicious code in a designated location.

Now let’s see the malicious content — open up your browser and search for your webserver to locate the “macro_empire” file.
When you click on the “macro_empire” link, it will display a backdoor code. We need to copy everything because we will be using it with Microsoft Office’s macro option.

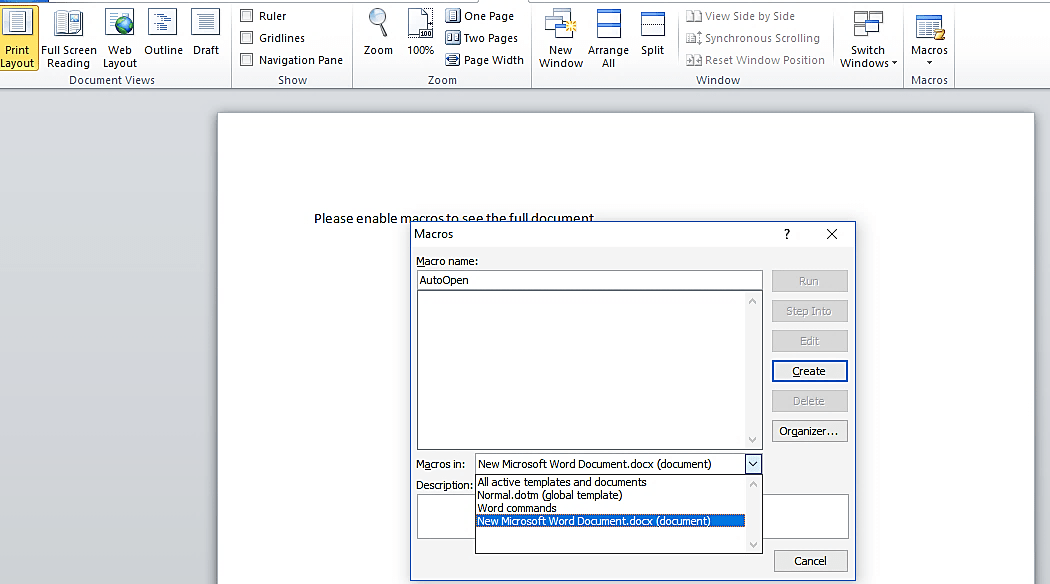
Next, open up an Office product, navigate to the “View” tab, select the “Macros” icon, and click on the “View Macros” option.
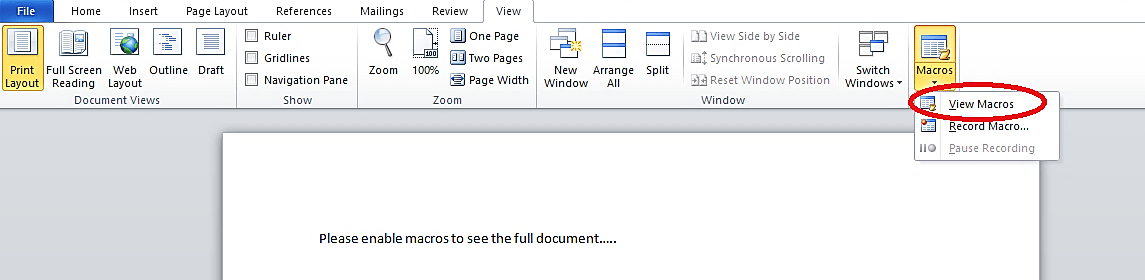
A small “Macros” window will appear. Name the macro as “AutoOpen” then select the “New Microsoft Word Document.docx (document)” option from the drop-down menu, and click on “Create” to make a macro.
In the “NewMacros (Code)” page, delete all content and paste the malicious backdoor that we copied from the web browser.
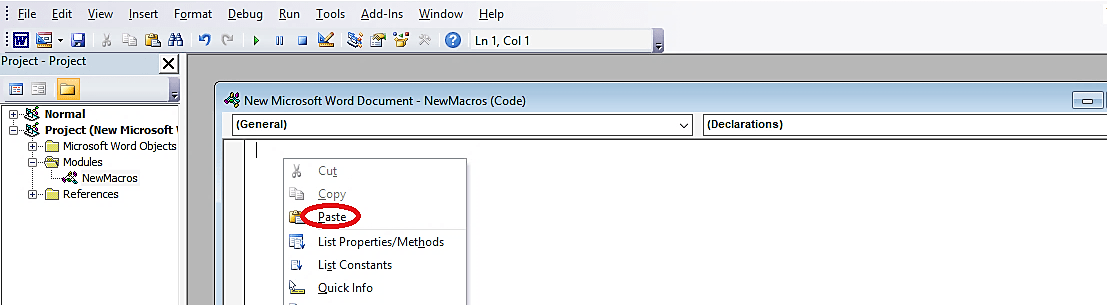

Once everything is complete, save the document as whatever you want but make sure that the “Save as type” is selected to “Word 97–2003 Document (*.doc).”

Now our macro Office file is ready, and it looks and operates as a legitimate Microsoft Office file as it is shown in the image below.

After this point, we need to send this file to our victim and ask to run it. This step depends on your social engineering skills. When the victim opens the malicious file and clicks on the “Enable Content” button, the attacker will receive a remote connection to the target computer.

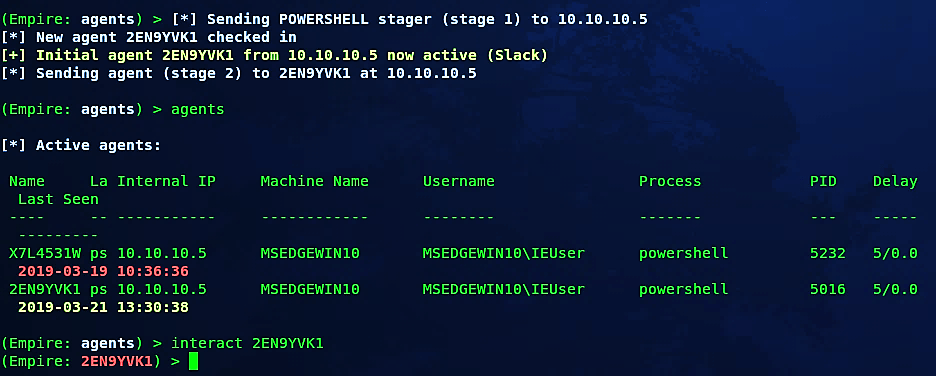
As it’s shown in the screenshot, we have a new active agent with the ID “2EN9YVK1” that we can interact with and exploit further.

This method might be detectable by anti-virus programs unless you modify the patterns of the code we used in this example.
On the off chance that the criminals figure out how to hack or socially engineer one individual’s email password, they’ll have access to that individual’s contact list– and on the grounds that many people utilize one secret key all over the place, they’ll most likely have access to that individual’s informal communication contacts also. When the criminals have that email account under their control, they send messages to all the contacts or leave messages on the entirety of their companion’s social pages, and perhaps on the pages of the individual’s friend’s friends.
