“Defend the Web” write-up (Beach)
“Defend the Web” write-up (Beach — steganography analysis)
Steganography is a broadly utilized system that controls data to conceal their reality. The word steganography is gotten from the Greek words “stegos,” signifying “cover,” and “grafia,” meaning “writing,” characterizing it as “covered writing.” Steganography is one such pro-security development in which secret information is implanted in a cover. It is an art and science of communicating in a manner that conceals the presence of communication. Even though Steganography furnishes excellent security, you can use it with Cryptography for better confidentiality and security.
Let’s take a look at the challenge and see what we can find.

In this example, we are presented with the image and a login form. Right-click on the image and download it to inspect further. Once you downloaded it, open it with a WordPad application and look for strings.
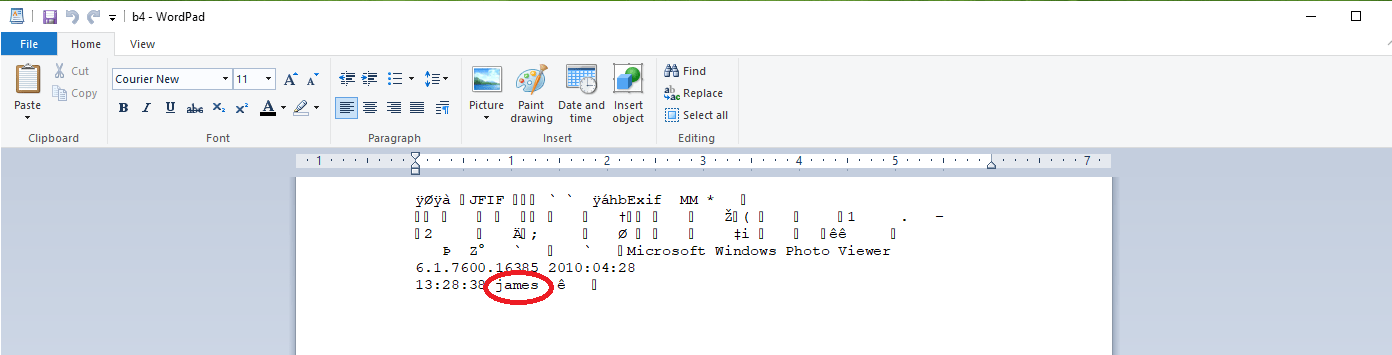
Here we found our first readable string “james”, take a note and look further.

Here is the second one. Copy the word “chocolate” and use this information on the login page to pass the challenge.

Image Steganography has numerous applications, particularly in the present modern, high-tech world. Privacy and anonymity are a worry for the vast majority on the web. It takes into consideration two parties to convey furtively and secretly. It takes into account some ethically cognizant individuals to securely whistle-blow on inner activities; it considers copyright assurance on excellent records utilizing the message as a digital watermark.
One of the other fundamental uses for Image Steganography is for the transportation of high-level or top-secret documents between international governments. While Image Steganography has many legitimate applications, it can likewise be very evil. It very well may be utilized by hackers to send infections and Trojans to compromise computers, and by terrorists and different associations that depend on clandestine tasks to impart covertly and securely.
