“Defend the Web” write-up (Intro 8)
“Defend the Web” write-up (Intro 8— path traversal vulnerability)
The goal of a path traversal attack (commonly referred to as directory traversal) is to get access to files and directories stored outside of the web root folder. It may be possible to access arbitrary files and directories contained on the file system, including application source code or configuration, by manipulating variables that reference files with “dot-dot-slash (../)” sequences and variations, or by employing absolute file paths. It should be remembered that system operational access control restricts file access (such as in the case of locked or in-use files on the Microsoft Windows operating system).
Let’s analyze the source code of the page and see what we can find.
Press on “CTRL + F” and search for the word “password”. Look for hidden type inputs to see if we can find any interesting stuff. In this example, we found another path.

Copy the path and paste it at the end of the root domain (in the URL field), then hit “Enter.”
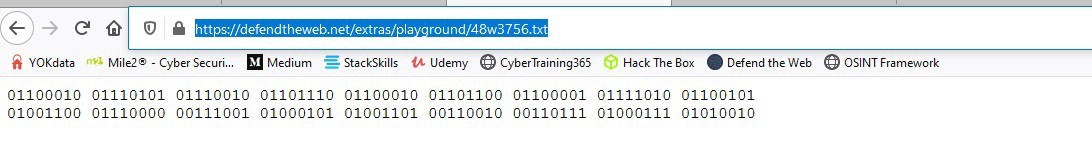
Looks like we managed to find the credentials but they are in binary form. To convert binary to a human-readable format is very easy. Just open up Google and type “binary to text”, then hit “Enter.”

Select any available converter and paste the binary code in to convert it.
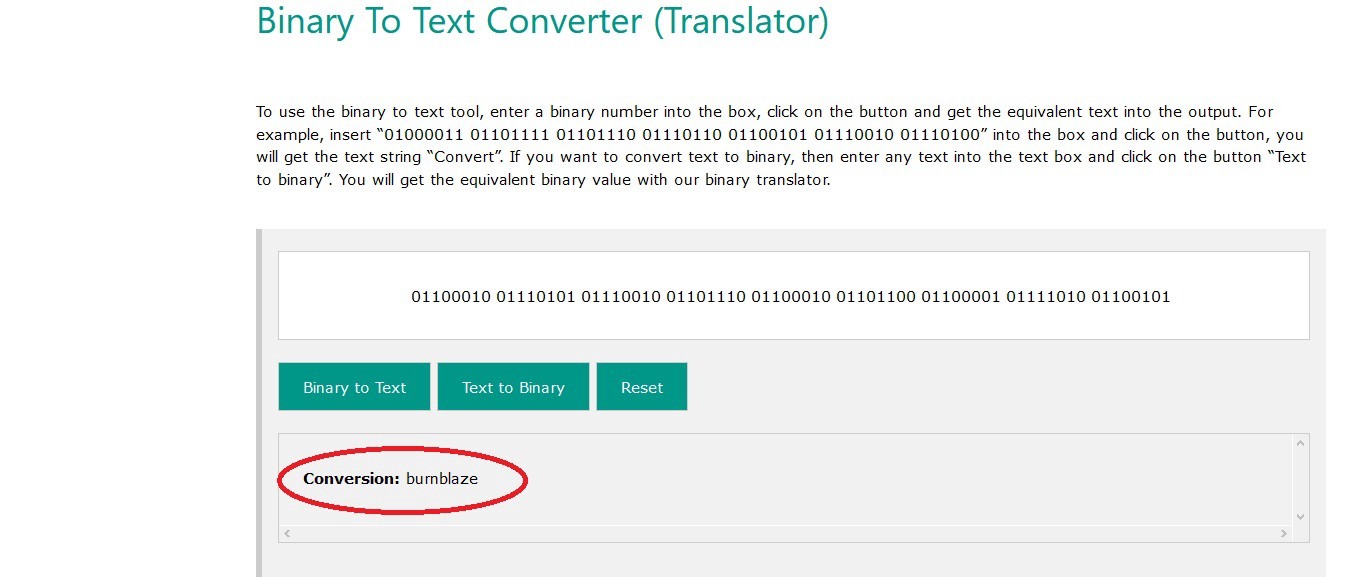
Looks like the username is “bumblaze”.

And the password is “Lp9EM27GR”. Copy your findings and use them on the login page to pass the challenge.
It is recommended that you implement the following procedures to safeguard the application from this flaw:
- When executing operations on files or folders, never utilize attacker-controlled data as a filename or part of a filename.
- If the filename should be determined by the user, utilize specified conditions rather than direct input.
- When working with files or folders using user-controlled input, make sure to verify the whitelist.
While you’re building or waiting for a security patch, Web Application Firewalls might be a useful tool for preventing vulnerability exploitation. Please keep in mind, that it is not recommended to use a WAF as a long-term solution or as a substitute for a properly crafted security patch.
Path traversal attack isn’t a new concept. Furthermore, like with other vulnerabilities, preventing it simply comes down to implementing sufficient input data validation in the program. The databases that collect data on application problems, on the other hand, reveal that this is unquestionably not a weakness that should be overlooked. New applications continue to enable for successful execution of this attack, allowing for unauthorized access to resources and even remote code execution.
