“Defend the Web” write-up (Sid / Intro)
“Defend the Web” write-up (Sid / Intro — cookie tampering)
While temporary cookies are primarily used to store the session identifier, many applications also utilize them to store additional session-specific data (such as specific preferences). The application treats these cookies as if they were read-only parameters. The application’s use of these cookies is frequently susceptible, making it a target for attackers who modify the cookies to circumvent the application’s security features.
Let’s take a look at the challenge. First, click on the “Enter site” button and analyze the behavior.

Looks like in this example we need to tamper with the cookies. Right-click on the page and from the drop-down menu select the “Inspect” option.
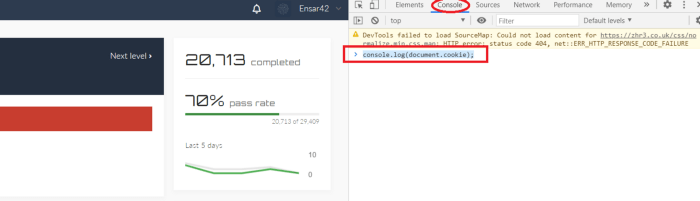
To view the cookie details, click on the “Console” tab, and then type the following JavaScript command “console.log(document.cookie);”.

As you can see, we could retrieve cookie information, but it looks like it is set to “false”. We need to change the “is_access=false;” to “is_access=true;”. To do so, type the following command “document.cookie=”i3_access=true;” and hit “Enter”.
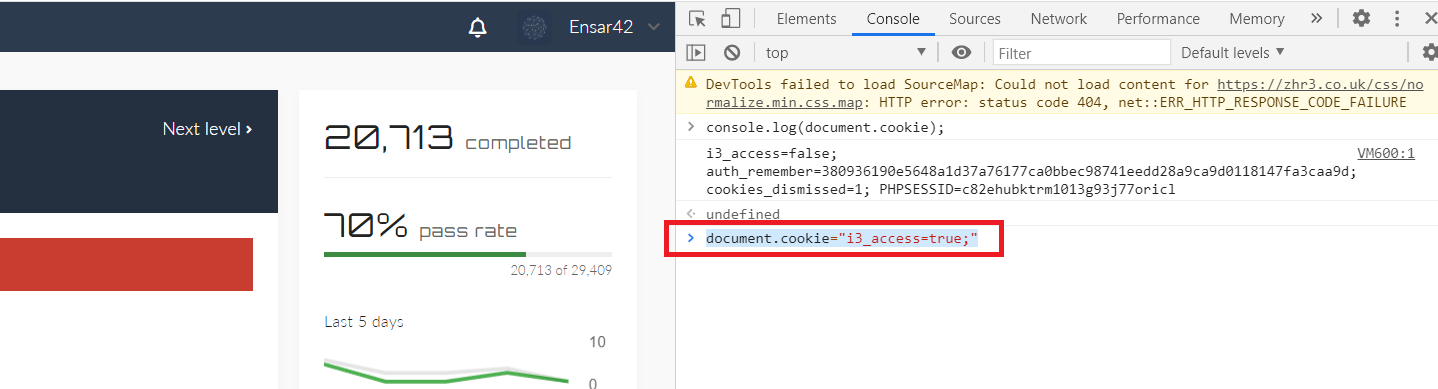
Now, the access to the cookies is set to “true”, we can go ahead and click on the “Enter site” button to access the page.
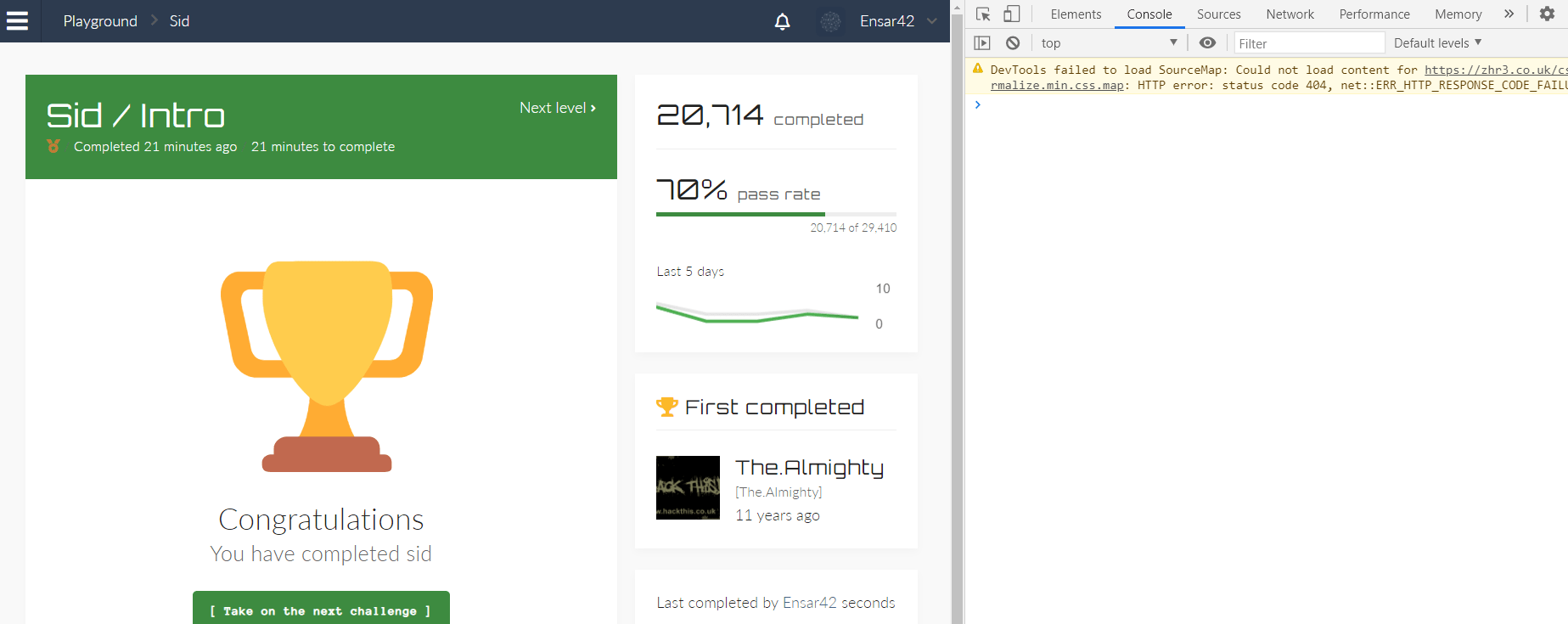
A single incidence of this violation indicates that a cookie’s value has been manually modified by an attacker. Because cookies are generally not changed by users, this modification cannot be made without manually modifying the HTTP traffic sent to the server.
In apps that use client-side javascript to change cookie values, a false positive alert can arise. While technically conceivable, this is a rare programming method that is unlikely to appear in the bulk of online applications. However, if this happens frequently, it’s possible that this is the case, and the violation would need to be disabled.
