Discovering and enumerating with Metasploit
Metasploit is one of the best consoles for data gathering, as it is an exceptionally far-reaching penetration testing device. In this instructional tutorial, we are going to cover some information-gathering techniques of a system utilizing Metasploit.
Let’s start the msfconsole and create a new workspace. Type “workspace –h” to list the help menu and see the options on how to create a workspace.

To create one use the “-a” option and specify the name of your new workspace.
Ex: (msf5 > workspace -a NetworkEnum).
Once you hit “Enter,” your workspace will be changed from the default to the name you specified.

Using Nmap database
After changing our workspace, now we can perform some scanning techniques using the Nmap database. Let’s first list the help menu of the database and see what options we can use.
Ex: (msf5 > db_nmap –h).

To perform a standard Nmap scan, type “db_nmap” and then provide the target IP address.
Ex: (msf5 > db_nmap -v 10.10.10.7).
It will display the results of a normal scan that we have mentioned in the Nmap section.

To view the hostname and the services that it runs, use the following commands.
Ex: (msf5 > hosts).
Ex: (msf5 > services).

Port scanning
You can also perform port scanning using some build-in auxiliaries in msfconsole. Use the “search” command to find a particular module in Metasploit.
Ex: (msf5 > search portscan).

In this example, we are going to use a TCP port scanner, so to select that module, type the “use” command and specify the module name.
Ex: (msf5 > use auxiliary/scanner/portscan/tcp).
Next, we should view all available options that need to be set to perform an accurate scan. To do so, type “show options” and hit “Enter.”
Ex: (msf5 auxiliary(scanner/portscan/tcp) > show options).

Set the target host IP or the range of IP addresses.
Ex: (msf5 auxiliary(scanner/portscan/tcp) > set RHOSTS 10.10.10.7).
Set the port range you would like to scan.
Ex: (msf5 auxiliary(scanner/portscan/tcp) > set PORTS 1–1024).
Set the number of concurrent ports to check per host.
Ex: (msf5 auxiliary(scanner/portscan/tcp) > set CONCURRENCY 50).
Then type “run” to begin the scanning process.
Ex: (msf5 auxiliary(scanner/portscan/tcp) > run).

Enumeration
Now, let’s perform one of the enumeration techniques. For that, we need to search for enumeration modules first.
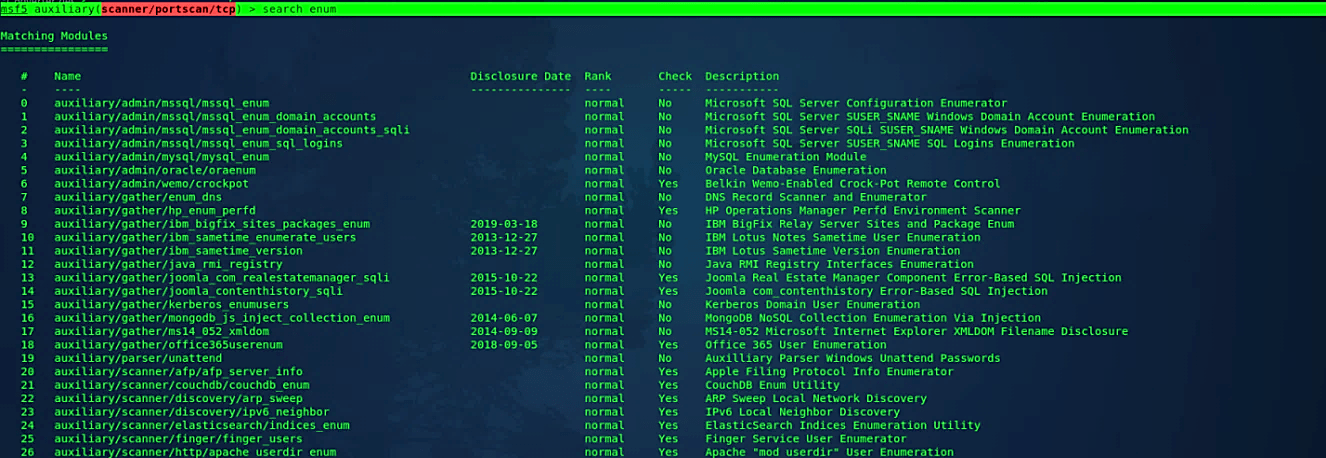
Ex: (msf5 auxiliary(scanner/portscan/tcp) > search enum).
It should display all possible enumeration modules.
If during your scanning, you target machines running Secure Shell (SSH), you should determine which version is running on the target. SSH is a secure protocol, but vulnerabilities in various implementations have been identified. You never know when you might get lucky and come across an old machine that hasn’t been updated. You can use the “auxiliary/scanner/ssh/ssh_version” module to determine the SSH version running on the target server.
Ex: (msf5 auxiliary(scanner/http/http_version) > use auxiliary/scanner/ssh/ssh_version).
View all available options and set the target host’s IP address.
Ex: (msf5 auxiliary(scanner/ssh/ssh_version) > set RHOSTS 10.10.10.7).
Then type “run” to begin SSH enumeration.

Let’s do another one. We know that the target device runs port 80 (HTTP), so, let’s find what version it runs. For this, we will be using the “auxiliary/scanner/http/http_version” module.
Ex: (msf5 auxiliary(scanner/portscan/tcp) > use auxiliary/scanner/http/http_version).
Set the target host’s IP address.
Ex: (msf5 auxiliary(scanner/http/http_version) > set RHOSTS 10.10.10.7).
Then run the enumerating process.

There are some instances where we can’t just go ahead and run noisy Nmap scans on our target for a number of reasons, such as when you’re running a black-box test for a client and there’s a firewall or intrusion detection device in place that would impede or alert sysadmins about your Nmap scans. As a result, integrating two of the most successful penetration testing methods becomes more sensible and realistic for us.
