DNS enumeration techniques
When we talk about DNS enumeration, we generally refer to every technique we use to gather as much data as possible by querying the DNS server of a website or host. DNS is regularly a rewarding hotspot for active data gathering. DNS offers an assortment of information about open organization servers, for example, IP addresses, server names, and server usefulness.
Interacting with a DNS server
A DNS server will typically disclose DNS and mail server data for the domain it has authority over. As open solicitations for mail and DNS server addresses make up the fundamental Internet experience, it is a need. By default, every configured domain should provide at least one DNS and mail server responsible for the domain.
For instance, let’s inspect the hackthissite.org (Hack This Site is a safe, free, and legal training place for hackers to test and expand their hacking skills.) domain for this activity. We’ll utilize the “host” command, together with the “-t” (type) parameter, to find both the DNS and mail servers for the hackthissite.org domain.
Ex: (root@kali:~# host -t ns hackthissite.org),
(root@kali:~# host -t mx hackthissite.org).

Automating lookups
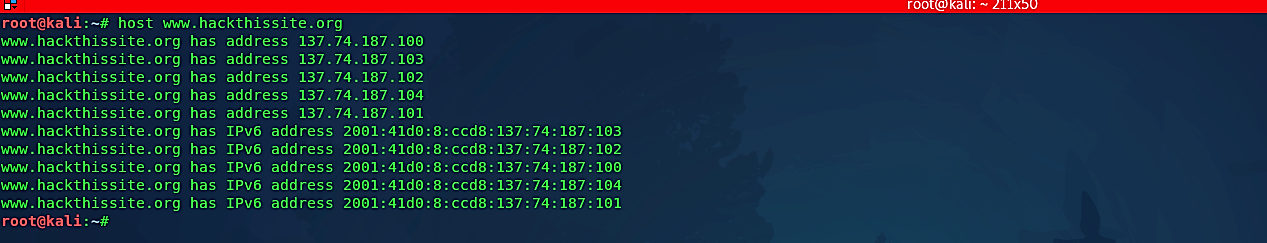
Since we have some underlying information from the hackthissite.org domain, we can keep on utilizing additional DNS inquiries to find more hostnames and IP addresses belonging to hackthissite.org. For instance, we can accept that the hackthissite.org domain has a web server, presumably with the hostname “www.” We can test this hypothesis by utilizing the “host” command once again.
Ex: (root@kali:~# host www. hackthissite.org).
Now, let’s check if hackthissite.org also has a server with the hostname “helloworld.”

Notice the difference between the query outputs.
DNS zone transfers
A zone transfer is like a database replication act between related DNS servers. This procedure incorporates replicating the zone record from a master DNS server to a slave server. The zone record contains a rundown of all the DNS names designed for that zone. Zone transfers ought to, as a rule, be restricted to approved slave DNS servers.
Sadly, numerous network administrators misconfigure their DNS servers, and thus, anybody requesting a duplicate of the DNS server zone will get one. All the servers’ names, locations, and usefulness can be presented to prying eyes. An effective zone transfer does not straightforwardly result in a network breach. Be that as it may, it facilitates the procedure. The “host” command syntax for preforming a zone transfer is as follows: (host -l <domain name> <dns server address>).
Ex: (root@kali:~# host -l hackthissite.org c.ns.buddyns.com).
