Emails Spoofing Technique
Email spoofing is the creation of fake email messages with a modified sender address. Since the core email protocols don’t have any mechanism for authentication, it is common for spam and phishing emails to use such a spoofing attempt to mislead the recipient about the origin of the message.
To perform such an attack first, we need to create an SMTP server relay to use it with Kali Linux to spoof emails. There are a lot of online services; the one we used is called “SendGrid.” SendGrid provides a cloud-based email delivery service that assists businesses with email delivery. The service manages various types of email, including shipping notifications, friend requests, sign-up confirmations, and email newsletters. You can register for free and start sending 100 free emails per day.
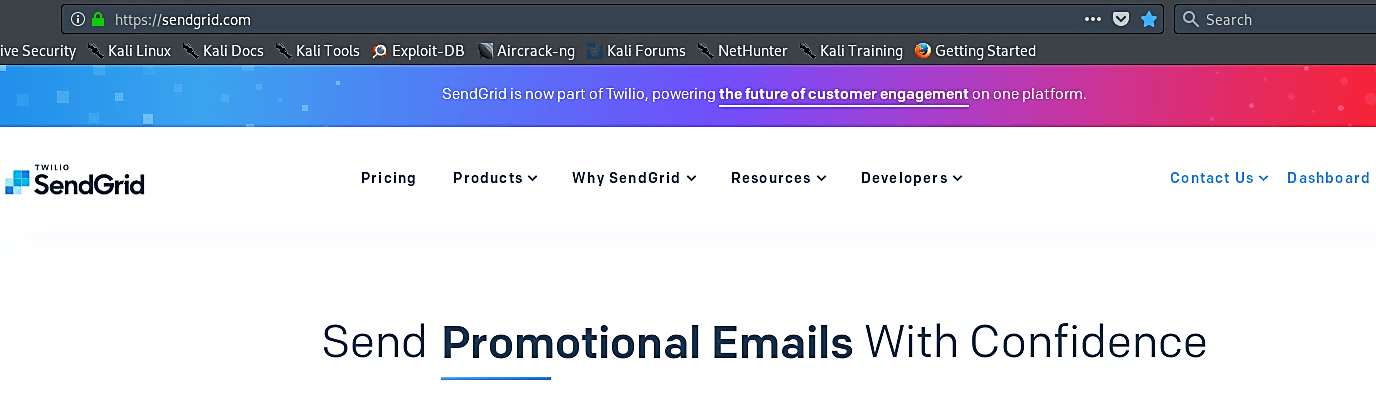
Once you create an account, from the welcome screen, click on the first option, “Integrate using our Web API or SMTP relay.”

Then chose an SMTP relay option.
Next, we need to create a key that later can be used in spoofing emails using Kali Linux. Once you start the process, SendGrid will generate all the necessary information to use in fake email attempts.

Now we are going to use a Kali tool called “SendEmail” to start sending fake emails. SendEmail is a lightweight, command-line SMTP email client. If you need to send an email from a command line, this free program is perfect, simple to use, and feature-rich.
Ex: (root@kali:~# sendemail -s smtp.sendgrid.net:587 -xu apikey -xp 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 -f “john.doe@gmail.com” -t “john.smith@gmail.com” -u “Cool Car” -m “Hey bro, I’m planning to get a new car, check this out and let me know what do you think. http://10.0.2.15/Evil-Files/Nissan.zip” -o message-header=“From: John Doe <john.doe@gmail.com>“).
· -s: Server relay and port number.
· -xu: Username.
· -xp: Password.
· -f: “From” email address.
· -t: “To” email address.
· -u: Email subject.
· -m: Message.
· -o: [message-header]: Advanced option to make “From” header look more convincing.
(To learn more about other available options, please view “help” or “man” pages for this particular tool).
When an email is spoofed successfully, the victim will receive a compelling email from a fake user trying to exploit the target, as is shown in the screenshot.
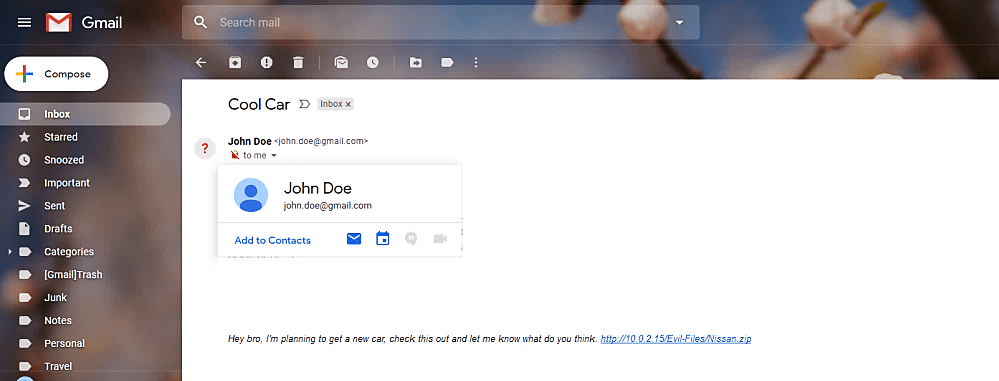
The success rate of social engineering using this method might be very high if you craft the spoofed email more realistically. Everything depends on how well you did in information gathering related to your target.
