Exploiting local file inclusion vulnerabilities in web applications
File inclusions are a piece of each propelled server-side scripting language on the web. They are expected to keep web applications’ code clean and viable. They additionally permit web applications to read documents from the file system, provide download functionality, parse configuration documents, and do other comparative tasks. Although, if not implemented correctly, they can turn into exploitable web vulnerability, which malicious aggressors can exploit.
Local File Inclusion (also known as LFI) is the process of including files, that are already locally present on the server, through the exploiting of vulnerable inclusion procedures implemented in the application.
This vulnerability occurs when this input is not properly sanitized, allowing directory traversal characters (such as dot-dot-slash) to be injected. Although most examples point to vulnerable PHP scripts, we should keep in mind that it is also common in other technologies such as JSP, ASP, and others.
To experiment with the file inclusion attack, click on the “File Inclusion” tab on the DVWA web page. Take a closer look at the last part of the URL “…/?page=include.php,” the website tries to load a page called “include.php.”
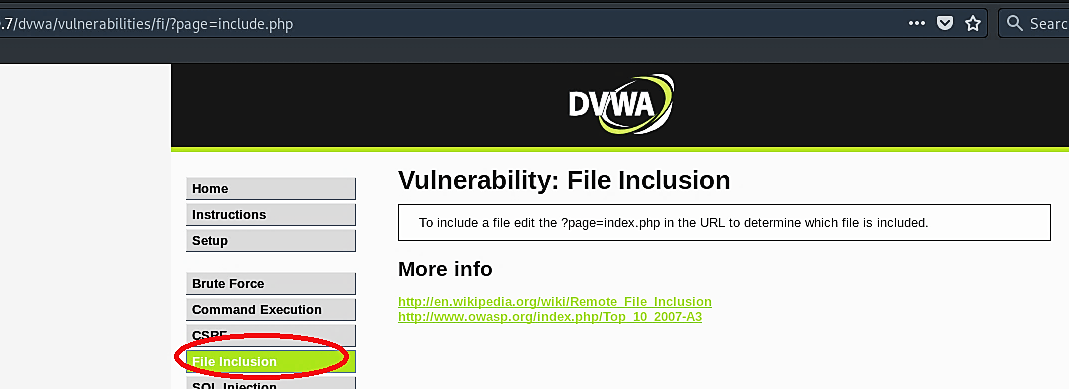
Let’s see if the file “include.php” exists using the same link, just removing the “?page=“ part.
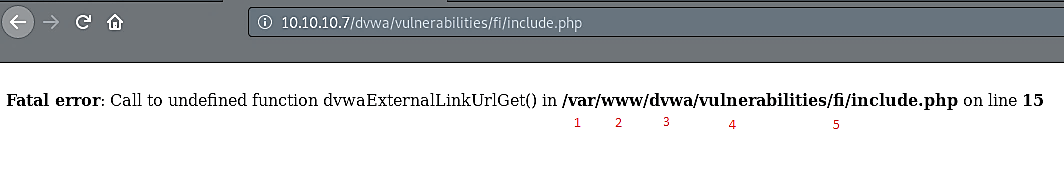
As you can see, the “include.php” file exists, and it locates within five directories. Now let’s see if we can use a file inclusion technique to move five directories back and list all information of the “passwd” file, which is located in the “/etc” directory. First, copy the direct path for the “include.php” file and add it to the link.
Ex: (10.10.10.7/dvwa/vulnerabilities/fi/?page=/var/www/dvwa/vulnerabilities/fi/include.php)
Then replace the names of the directories with two dots (this will exit the particular directory and take you back to the “/root/” directory). Add “/etc/passwd” to the end then hit “Enter.”
Ex: (10.10.10.7/dvwa/vulnerabilities/fi/?page=/../../../../../etc/passwd).

The image above shows us that it is possible to parse through directories and even list the contents of any files using by exploiting file inclusion vulnerability.
