File upload by injecting null hex character
One of the exciting approaches to upload pernicious documents is to utilize URL-encoded null byte characters. Unapproved access to the system documents could be yielded through such infusion of an invalid byte resulting in a blank space in the ASCII interpretation. Embedding an invalid byte will lead a web application utilizing C/C++ libraries when checking for the record name or its content. It will try to deceive as if it is the end of the string, and it should stop perusing at this progression.
Before uploading our PHP file, let’s make a small change to it and rename it from “image_file.php.jpeg” to “image_file.phpA.jpeg.” Here we added a capital “A” character after the “.php” extension (you can put whatever you want).
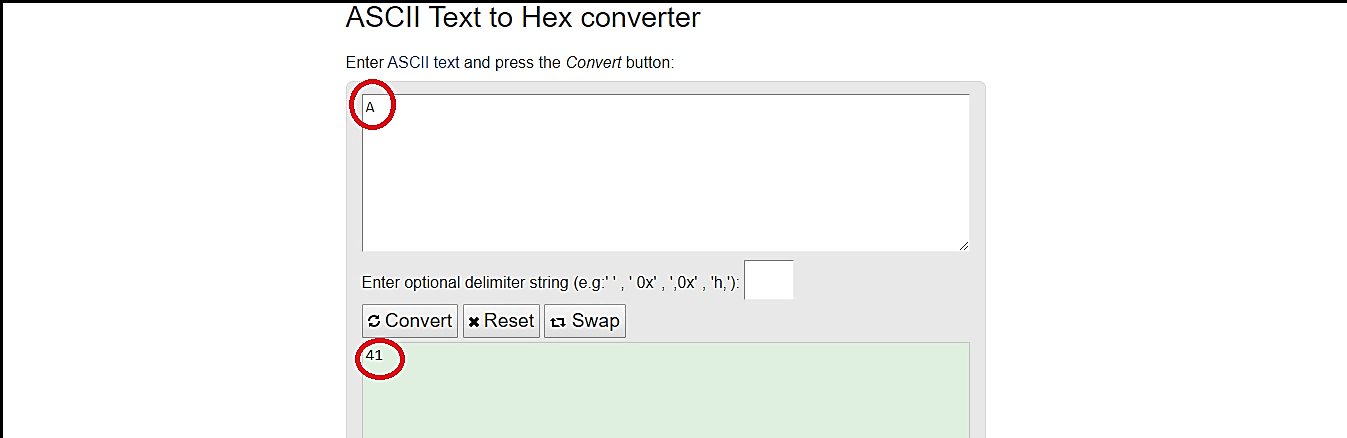
The purpose of it is to quickly identify this character in the hex field and change it to the null character before submitting the request. To find this hex byte of the “A” ASCII character, we need to know what it looks like. For this, we can use any online “ASCII to Hex” converters, and in our example, the “A” character stands for “41” in hex byte. Note it down so we can use it later on.
Now, go to the DVWA web page and try to upload the malicious PHP file, but before uploading it, make sure that the Burp interception is on.

Return to the “Burp Suite” and from the “Proxy” under the “Intercept” tab analyze the “Hex” field. On the right side of the display, try to find the filename “image_file.phpA.jpeg.” Once you find it, on the left side where all the hex bytes are listed, you’ll be able to see the hex byte “41”. Double click on the byte and change it to “00” to make it null, and then click on the “Forward” button to complete the request.

Once the file is uploaded, the directory’s path to the uploaded file will be shown.

Copy and paste this path in the URL and hit “Enter” to execute the PHP file on the web server.

If everything is done correctly, we will be able to receive a reverse shell connection with full root control.

